Writeup author : Hicham Terkiba (@IOBreaker)
Try Hack Me – Box Description :
These challenges are aimed towards learning about the “Static Analysis” technique used to analyse the malware. The main aim for this room is not to used any types of debuggers neither the executable’s/programs should be run on any platform. You are required to answer all the questions without even using the debugger and even not executing the executable’s/programs.
String1.exe_
Just to be sure that the file is a zip one 🙂
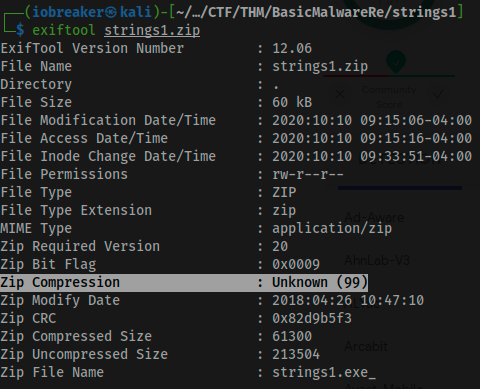
$ exiftool strings1.zip
ExifTool Version Number : 12.06
File Name : strings1.zip
Directory : .
File Size : 60 kB
File Modification Date/Time : 2020:10:10 09:15:06-04:00
File Access Date/Time : 2020:10:10 09:15:16-04:00
File Inode Change Date/Time : 2020:10:10 09:33:51-04:00
File Permissions : rw-r--r--
File Type : ZIP
File Type Extension : zip
MIME Type : application/zip
Zip Required Version : 20
Zip Bit Flag : 0x0009
Zip Compression : Unknown (99) <==========
Zip Modify Date : 2018:04:26 10:47:10
Zip CRC : 0x82d9b5f3
Zip Compressed Size : 61300
Zip Uncompressed Size : 213504
Zip File Name : strings1.exe_
Ok, I had a zip file that contains one file named stirngs1.exe_, but Zip compression type is unknown
I tried to unzip it
$ unzip strings1.zip
Archive: strings1.zip
skipping: strings1.exe_ unsupported compression method 99
But unzip does not succeed to do the job
I decided to use xarchive (more file types and compression support)
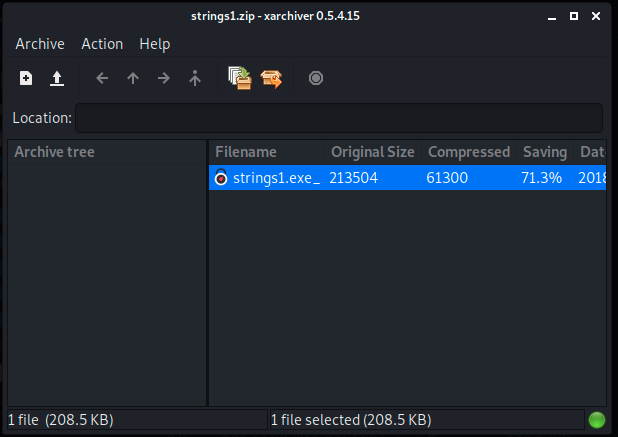
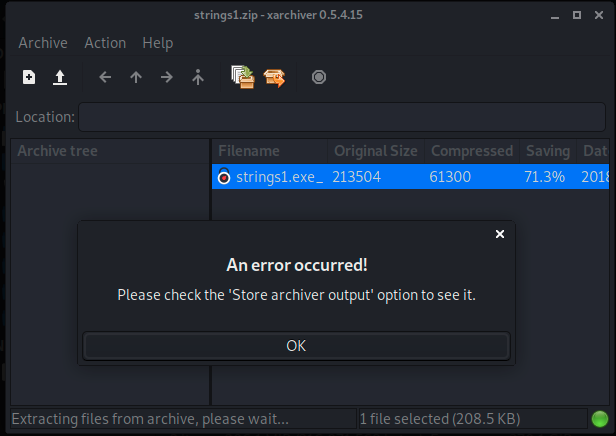
The result was the same, so i decided to go with p7zip-full utility that support very large range of encryption/compression types
$ sudo apt-get install p7zip-full
$ 7z x -pMalwareTech strings1.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-4850HQ CPU @ 2.30GHz (40661),ASM,AES-NI)
Scanning the drive for archives:
1 file, 61498 bytes (61 KiB)
Extracting archive: strings1.zip
--
Path = strings1.zip
Type = zip
Physical Size = 61498
Everything is Ok
Size: 213504
Compressed: 61498
Bingo, I succeeded extracting the file.
I started by exploring file’s metadata
$ file strings1.exe_
strings1.exe_: PE32 executable (GUI) Intel 80386, for MS Windows
$ exiftool strings1.exe_
ExifTool Version Number : 12.06
File Name : strings1.exe_
Directory : .
File Size : 208 kB
File Modification Date/Time : 2018:04:26 13:47:11-04:00
File Access Date/Time : 2020:10:11 04:09:04-04:00
File Inode Change Date/Time : 2020:10:11 04:09:04-04:00
File Permissions : rw-r--r--
File Type : Win32 EXE
File Type Extension : exe
MIME Type : application/octet-stream
Machine Type : Intel 386 or later, and compatibles
Time Stamp : 2018:04:26 13:47:10-04:00
Image File Characteristics : Executable, 32-bit
PE Type : PE32
Linker Version : 10.0
Code Size : 5120
Initialized Data Size : 207360
Uninitialized Data Size : 0
Entry Point : 0x22b0
OS Version : 5.1
Image Version : 0.0
Subsystem Version : 5.1
Subsystem : Windows GUI
It seems to be a windows executable (32bit) with GUI support
I used strings to see it the flag can be grabbed directly
$ strings strings1.exe_ | grep -i FLAG
FLAG{WORK-REPUBLIC-LIMIT-BUILDING-RIGHT}
FLAG{WORK-SOCIAL-LIVING-PROMOTE-LAWS}
FLAG{WORK-SOVIET-ENSURED-STATE-THE}
FLAG{WORK-STANDING-STATE-CITIZEN-PROHIBITED}
FLAG{WORK-SUN-SHALL-AND-SATISFY}
FLAG{WORK-SUPREME-SHALL-THE-CAUSE}
FLAG{WORK-SYSTEMS-ARTICLE-COURT-REPUBLIC}
FLAG{WORK-THE-FOR-THE-UNION}
FLAG{WORK-THEIR-ONCE-SPECIFIC-OTHER}
FLAG{WORK-THEIR-OTHER-DISPUTES-THE}
FLAG{WORK-USSR-AND-ARE-ARE}
FLAG{WORK-WORKING-AND-AND-INTELLIGENTSIA}
FLAG{WORLD-AND-FOR-AUTHORITY-ORGANISATIONS}
FLAG{WORLD-INTO-BROAD-THE-CHAIRMAN}
FLAG{WORLD-REACHED-THE-STATE-SOVIETS}
FLAG{YAKUT-SOCIALIST-THE-WORK-CAPITAL}
FLAG{YEARS-AND-COUNCIL-INDIVIDUAL-WHICH}
FLAG{YEARS-BODIES-THE-ARTICLE-OTHER}
FLAG{YEARS-HAS-STATE-THE-THEIR}
FLAG{YEAR-THEIR-FORCES-SUBJECT-CONSTRUCTIVE}
FLAG{YOUNG-BODIES-AND-SOCIALISM-SPOUSES}
[--- REDACTED ---]
$ strings strings1.exe_ | grep -i FLAG | sort -u | wc -l
4196
I ended up with 4196 possible flags. I cannot test them all so i tought that it was the time to fire up Ghidra
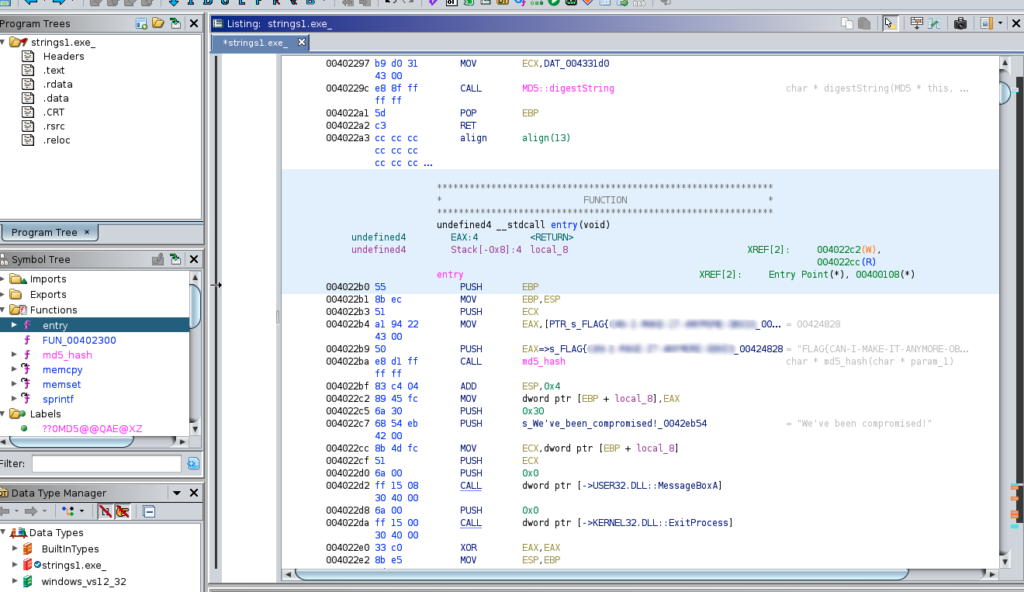
Two functions were important; the first one is the entry point function and the second one is the md5_hash function
It’s very easy to understand the flow of this program from the assembly code, nothing complicated
- Program start
- Doing some inits
- Retrieving the value of the FLAG and storing it into EAX registry
- Calling md5_hash function to get the string hash
- Display the all via a messagebox
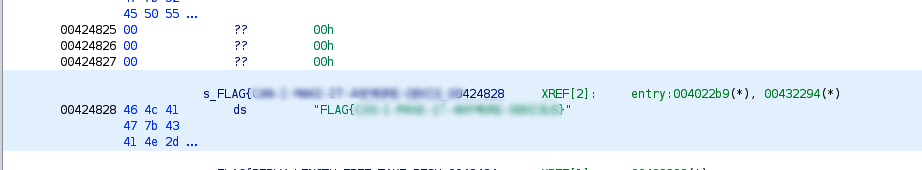
If you follow the xREF related to the FLAG, you can easily see the full FLAG string
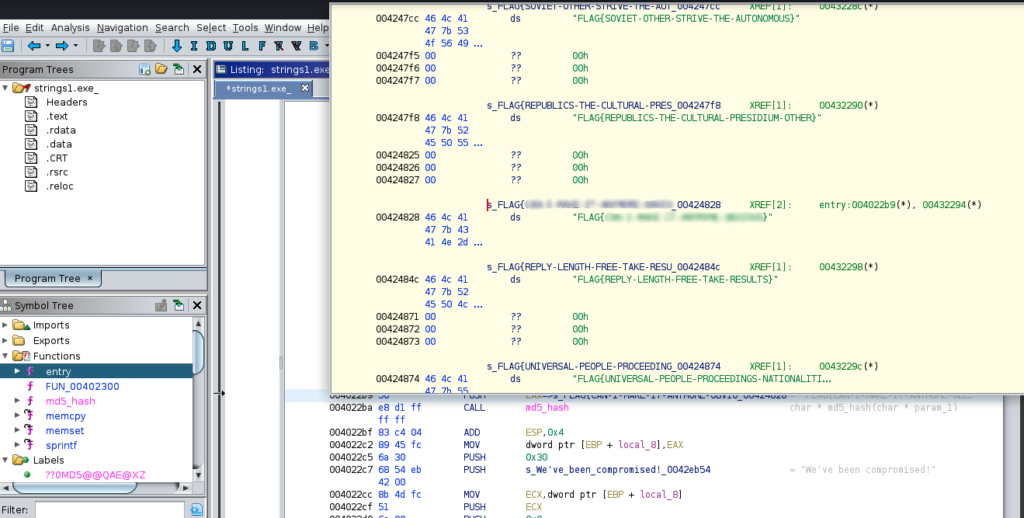
And finally the flag 😉
String2.exe_
As usual
$ exiftool strings2.zip
ExifTool Version Number : 12.06
File Name : strings2.zip
Directory : .
File Size : 3.3 kB
File Modification Date/Time : 2020:10:10 09:15:06-04:00
File Access Date/Time : 2020:10:10 09:15:06-04:00
File Inode Change Date/Time : 2020:10:11 05:53:17-04:00
File Permissions : rw-r--r--
File Type : ZIP
File Type Extension : zip
MIME Type : application/zip
Zip Required Version : 20
Zip Bit Flag : 0x0009
Zip Compression : Unknown (99)
Zip Modify Date : 2018:04:26 13:00:00
Zip CRC : 0x83b7384e
Zip Compressed Size : 3227
Zip Uncompressed Size : 9216
Zip File Name : strings2.exe_
I extracted it using the same process as for strings1
$ 7z x -pMalwareTech strings2.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-4850HQ CPU @ 2.30GHz (40661),ASM,AES-NI)
Scanning the drive for archives:
1 file, 3425 bytes (4 KiB)
Extracting archive: strings2.zip
--
Path = strings2.zip
Type = zip
Physical Size = 3425
Everything is Ok
Size: 9216
Compressed: 3425
Just to see if any thing is inside the file
$ binwalk -M strings2.exe_
Scan Time: 2020-10-11 05:54:16
Target File: /mnt/hgfs/CTF/THM/BasicMalwareRe/strings2/strings2.exe_
MD5 Checksum: f5eaee18d00949d7ce52a9363647ce67
Signatures: 391
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Microsoft executable, portable (PE)
Ok so I added strings2.exe_ to Ghidra project and start analysing it
I noticed that strings2 add a lot of values to the stack, one after the other
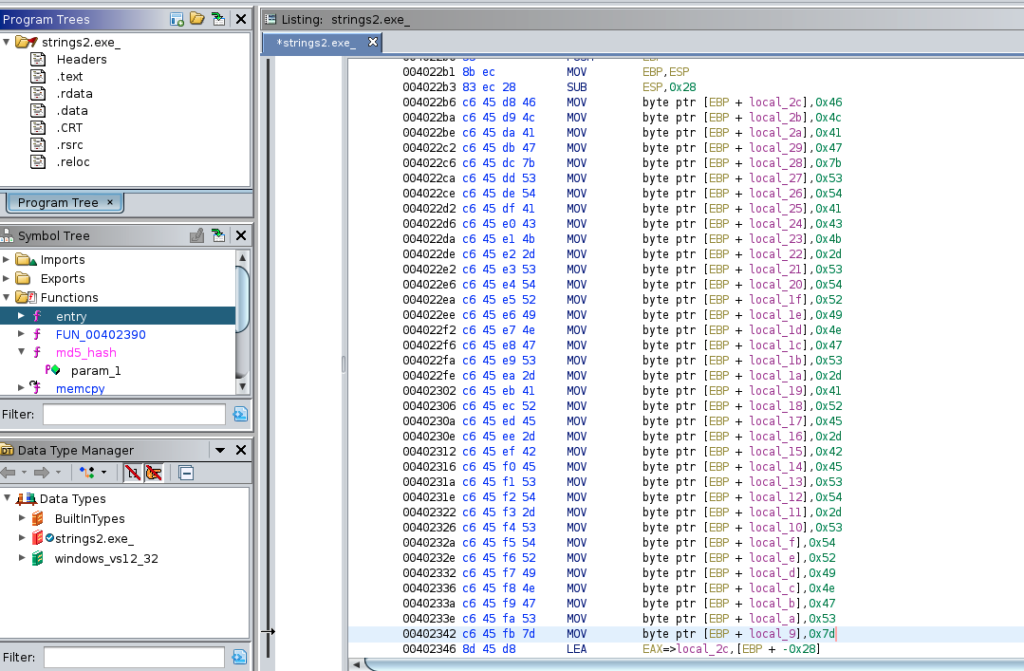
I extracted the values in hexadecimal
$ cat hex.txt | cut -d '=' -f 2 | sed -e 's/ |\;//g'
0x46;
0x4c;
0x41;
0x47;
0x7b;
0x53;
0x54;
0x41;
0x43;
0x4b;
0x2d;
0x53;
0x54;
0x52;
0x49;
0x4e;
0x47;
0x53;
0x2d;
0x41;
0x52;
0x45;
0x2d;
0x42;
0x45;
0x53;
0x54;
0x2d;
0x53;
0x54;
0x52;
0x49;
0x4e;
0x47;
0x53;
0x7d;
and with a little bash script I converted the hex values to get an ASCII representation
FLAG=""; for i in `cat hex.txt | cut -d '=' -f 2 | sed 's/[\s|;]//g'`
do
FLAG=${FLAG}`echo $i | xxd -r -p`
done
echo $FLAG
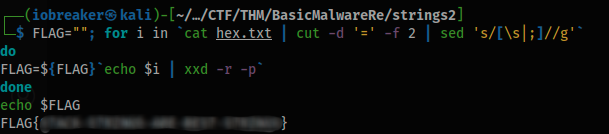
And finally got the flag 😉
String3.exe_
Nothing new, just extracting the file strings3.exe_
$ 7z x -pMalwareTech strings3.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.utf8,Utf16=on,HugeFiles=on,64 bits,4 CPUs Intel(R) Core(TM) i7-4850HQ CPU @ 2.30GHz (40661),ASM,AES-NI)
Scanning the drive for archives:
1 file, 11456 bytes (12 KiB)
Extracting archive: strings3.zip
--
Path = strings3.zip
Type = zip
Physical Size = 11456
Everything is Ok
Size: 52736
Compressed: 11456
Nothing interesting to check
$ binwalk -M strings3.exe_
Scan Time: 2020-10-11 09:09:11
Target File: /mnt/hgfs/CTF/THM/BasicMalwareRe/strings3/strings3.exe_
MD5 Checksum: 7ca469245329b093fc6284e55ebf993e
Signatures: 391
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Microsoft executable, portable (PE)
I added strings3.exe_ to Ghidra project and start analysing it
After finding the entry point, i started looking how the program operates
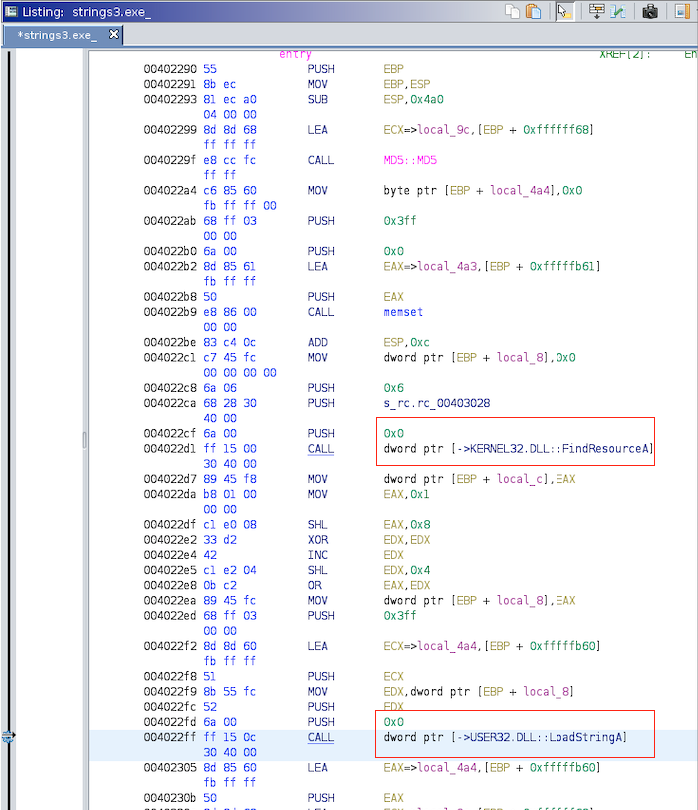
Nothing complicated, The program use two functions
- FindResourceA -> from kernel32.dll (Determines the location of a resource with the specified type and name)
- LoadStringA -> from user32.dll (Loads a string resource and either copies the string into a buffer or returns a read-only pointer to the string resource itself)
I was interested by the second function (LoadStringA) and especially by the uID parameter that was passed to it in order to retrieve the string i am looking for
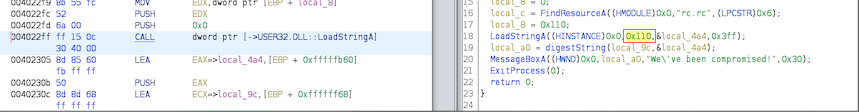
The uID in our case is equal to 0x110 in hexadecimal
$ echo $((16#110))
272
It’s equal to 272 in decimal
I displayed the ressources and searched for the one with the id 272

And finally got the flag 😉
Enjoy 😉