Writeup author : Hicham Terkiba (@IOBreaker)
Try Hack Me – Box Description :
This is a memory dump of compromised system, do some forensics kung-fu to explore the inside
Level : Medium
I downloaded the zip file which is the entry point.
First, I checked if the md5 hash is the correct one : ba44c4b977d28132faeb5fb8b06debce
$ md5sum victim.zip
0e0e783c777cbdb75e055bf8046c50b7 victim.zip
$ unzip victim.zip
Archive: victim.zip
inflating: victim.raw
$ md5sum victim.raw
ba44c4b977d28132faeb5fb8b06debce victim.raw
Question : What is the Operating System of this Dump file? (OS name)
I used hexEditor for that
$ hexeditor victim.raw
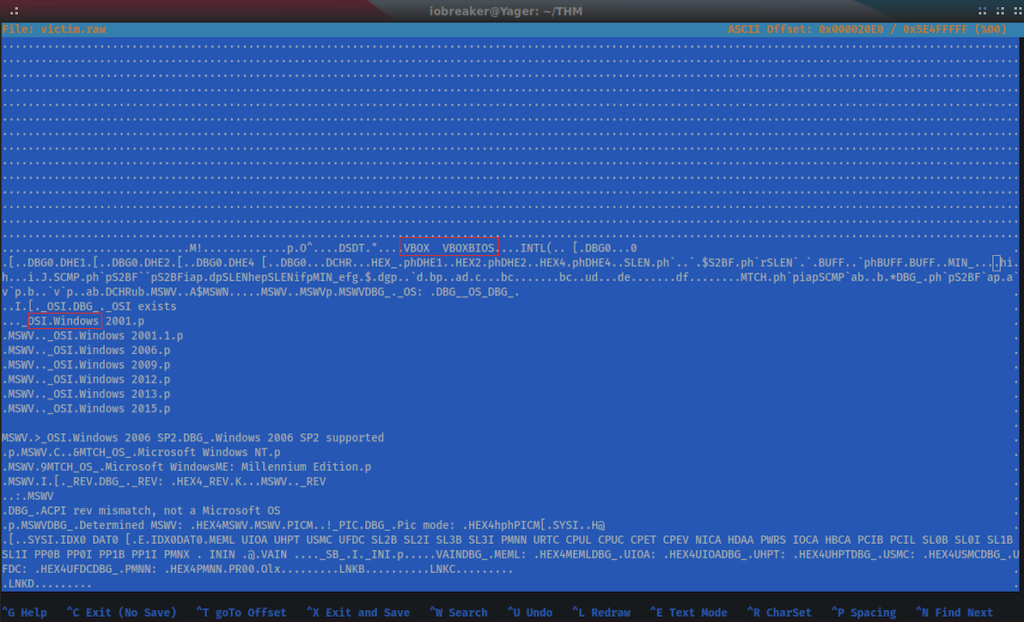
The OSName is : windows
According to the Hexdump information, the os was ruinning under VirtualBox
I got more information using volatility framwork
$ volatility -f victim.raw imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/home/iobreaker/THM/victim.raw)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf800028420a0L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002843d00L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2019-05-02 18:11:45 UTC+0000
Image local date and time : 2019-05-02 11:11:45 -0700
Question is : What is the PID of SearchIndexer?
I used volatility with plugin pslist to get all running processes by following the EPROCESS lists
$ volatility -f victim.raw --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start
------------------ -------------------- ------ ------ ------ -------- ------ ------ -------------------------
------[ REDACTED ] ----------
0xfffffa8003148b30 taskhost.exe 1788 504 8 159 1 0 2019-05-02 18:03:09 UTC+0000
0xfffffa8003172b30 explorer.exe 1860 1756 19 645 1 0 2019-05-02 18:03:09 UTC+0000
0xfffffa800315eb30 dwm.exe 1896 892 3 69 1 0 2019-05-02 18:03:09 UTC+0000
0xfffffa800300d700 VBoxTray.exe 1600 1860 13 141 1 0 2019-05-02 18:03:25 UTC+0000
0xfffffa8003367060 SearchIndexer. ==> xxxx 504 11 629 0 0 2019-05-02 18:03:32 UTC+0000
0xfffffa80033f6060 WmiPrvSE.exe 2876 628 5 113 0 0 2019-05-02 18:03:55 UTC+0000
0xfffffa8003162060 svchost.exe 1820 504 11 317 0 0 2019-05-02 18:05:09 UTC+0000
0xfffffa8003371540 wmpnetwk.exe 2464 504 14 440 0 0 2019-05-02 18:05:10 UTC+0000
0xfffffa80014eeb30 taskhost.exe 1148 504 8 176 0 0 2019-05-02 18:09:58 UTC+0000
The PID of SearchIndexer process is replaced by the xxxx
Question : What is the last directory accessed by the user?
I used the plugin shellbags in order to gather all the information about a viewed directory such as size, position, and icon
$ volatility -f victim.raw --profile=Win7SP1x64 shellbags
Volatility Foundation Volatility Framework 2.6
Scanning for registries....
Gathering shellbag items and building path tree...
------[ REDACTED ] ----------
***************************************************************************
Registry: \??\C:\Users\victim\AppData\Local\Microsoft\Windows\UsrClass.dat
Key: Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\2\0
Last updated: 2019-04-27 10:48:33 UTC+0000
Value Mru File Name Modified Date Create Date Access Date File Attr Path
------- ----- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ----
0 0 deleted_files 2019-04-27 10:30:26 UTC+0000 2019-04-27 10:38:24 UTC+0000 2019-04-27 10:38:24 UTC+0000 NI, DIR Z:\logs\dxxxxx_xxxxxxs
***************************************************************************
------[ REDACTED ] ----------
To be sure of that, I redirected the output to a text fil and did some filters to be able to sort the result
$ cat shellbags.txt | grep " DIR " | egrep -iv 'itempos1366|1970-01-01' | tr -s ' ' ' ' | cut -d ' ' -f10- | sort -u
------[ REDACTED ] ----------
2019-04-23 06:44:46 UTC+0000 DIR C:\Users\victim\Downloads\Microsoft Office Enterprise 2010 Corporate Final (full activated)\Microsoft Office Enterprise 2010 Corporate Final (full activated)
2019-04-23 07:08:44 UTC+0000 NI, DIR C:\Users\victim\AppData\LocalLow\Mozilla
2019-04-23 07:26:08 UTC+0000 NI, DIR Local\Temp\VBE
2019-04-27 10:27:26 UTC+0000 RO, DIR C:\Program Files (x86)
2019-04-27 10:33:16 UTC+0000 NI, DIR Local\Temp\TCD9312.tmp
2019-04-27 10:33:16 UTC+0000 NI, DIR Local\Temp\TCD9405.tmp
2019-04-27 10:36:06 UTC+0000 DIR C:\Program Files (x86)\Capture
2019-04-27 10:38:22 UTC+0000 NI, DIR Z:\logs
2019-04-27 10:38:24 UTC+0000 NI, DIR Z:\logs\dxxxxxx_xxxxxxs <========== THE LAST ONE
The Last visited drectory is Z:\logs\dxxxxx_xxxxxxs , caracters are replaced by the xxxx
Question : There are many suspicious open ports; which one is it? (ANSWER format: protocol:port)
The plugin i used was the netscan
$ volatility -f victim.raw --profile=Win7SP1x64 netscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Proto Local Address Foreign Address State Pid Owner Created
------[ REDACTED ] ----------
0x5c49cbb0 UDPv4 0.0.0.0:59471 *:* 1368 svchost.exe 2019-05-02 18:03:06 UTC+0000
0x5c4a31c0 UDPv4 0.0.0.0:59472 *:* 1368 svchost.exe 2019-05-02 18:03:06 UTC+0000
0x5c4a31c0 UDPv6 :::59472 *:* 1368 svchost.exe 2019-05-02 18:03:06 UTC+0000
0x5c4ac630 UDPv4 0.0.0.0:3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c4ac630 UDPv6 :::3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c519b30 UDPv4 0.0.0.0:3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c537ec0 UDPv4 0.0.0.0:3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c690360 UDPv4 0.0.0.0:0 *:* 1004 svchost.exe 2019-05-02 18:02:56 UTC+0000
0x5c690360 UDPv6 :::0 *:* 1004 svchost.exe 2019-05-02 18:02:56 UTC+0000
0x5c6918e0 UDPv4 0.0.0.0:5355 *:* 1004 svchost.exe 2019-05-02 18:02:56 UTC+0000
0x5c6918e0 UDPv6 :::5355 *:* 1004 svchost.exe 2019-05-02 18:02:56 UTC+0000
0x5c692ae0 UDPv4 0.0.0.0:5355 *:* 1004 svchost.exe 2019-05-02 18:02:56 UTC+0000
0x5c7f9600 UDPv4 0.0.0.0:3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c7f9600 UDPv6 :::3702 *:* 1368 svchost.exe 2019-05-02 18:03:14 UTC+0000
0x5c44e1b0 TCPv4 0.0.0.0:5357 0.0.0.0:0 LISTENING 4 System
0x5c44e1b0 TCPv6 :::5357 :::0 LISTENING 4 System
0x5c528010 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System
0x5c528010 TCPv6 :::445 :::0 LISTENING 4 System
0x5c534c60 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 504 services.exe
0x5c534c60 TCPv6 :::49156 :::0 LISTENING 504 services.exe
0x5c535010 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 504 services.exe
0x5c6de720 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 920 svchost.exe
0x5c6de720 TCPv6 :::49154 :::0 LISTENING 920 svchost.exe
0x5c6e0df0 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 920 svchost.exe
0x5c717460 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 512 lsass.exe
------[ REDACTED ] ----------
A lot of process founded that can be the answer to the question, but to be dure which one is the one I am looking for, I checked if any malious process exist using malfind
$ volatility -f victim.raw --profile=Win7SP1x64 malfind
Volatility Foundation Volatility Framework 2.6
Process: explorer.exe Pid: 1860 Address: 0x3ee0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x03ee0000 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x03ee0010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x03ee0020 00 00 ee 03 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x03ee0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x03ee0000 0000 ADD [EAX], AL
0x03ee0002 0000 ADD [EAX], AL
0x03ee0004 0000 ADD [EAX], AL
0x03ee0006 0000 ADD [EAX], AL
0x03ee0008 0000 ADD [EAX], AL
0x03ee000a 0000 ADD [EAX], AL
0x03ee000c 0000 ADD [EAX], AL
0x03ee000e 0000 ADD [EAX], AL
0x03ee0010 0000 ADD [EAX], AL
0x03ee0012 0000 ADD [EAX], AL
0x03ee0014 0000 ADD [EAX], AL
0x03ee0016 0000 ADD [EAX], AL
0x03ee0018 0000 ADD [EAX], AL
0x03ee001a 0000 ADD [EAX], AL
0x03ee001c 0000 ADD [EAX], AL
0x03ee001e 0000 ADD [EAX], AL
0x03ee0020 0000 ADD [EAX], AL
0x03ee0022 ee OUT DX, AL
0x03ee0023 0300 ADD EAX, [EAX]
0x03ee0025 0000 ADD [EAX], AL
0x03ee0027 0000 ADD [EAX], AL
0x03ee0029 0000 ADD [EAX], AL
0x03ee002b 0000 ADD [EAX], AL
0x03ee002d 0000 ADD [EAX], AL
0x03ee002f 0000 ADD [EAX], AL
0x03ee0031 0000 ADD [EAX], AL
0x03ee0033 0000 ADD [EAX], AL
0x03ee0035 0000 ADD [EAX], AL
0x03ee0037 0000 ADD [EAX], AL
0x03ee0039 0000 ADD [EAX], AL
0x03ee003b 0000 ADD [EAX], AL
0x03ee003d 0000 ADD [EAX], AL
0x03ee003f 00 DB 0x0
Process: explorer.exe Pid: 1860 Address: 0x3f90000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 2, PrivateMemory: 1, Protection: 6
0x03f90000 00 00 00 00 00 00 00 00 4b 5b b2 8d 2d d2 00 01 ........K[..-...
0x03f90010 ee ff ee ff 00 00 00 00 28 01 f9 03 00 00 00 00 ........(.......
0x03f90020 28 01 f9 03 00 00 00 00 00 00 f9 03 00 00 00 00 (...............
0x03f90030 00 00 f9 03 00 00 00 00 80 00 00 00 00 00 00 00 ................
0x03f90000 0000 ADD [EAX], AL
0x03f90002 0000 ADD [EAX], AL
0x03f90004 0000 ADD [EAX], AL
0x03f90006 0000 ADD [EAX], AL
0x03f90008 4b DEC EBX
0x03f90009 5b POP EBX
0x03f9000a b28d MOV DL, 0x8d
0x03f9000c 2dd20001ee SUB EAX, 0xee0100d2
0x03f90011 ff DB 0xff
0x03f90012 ee OUT DX, AL
0x03f90013 ff00 INC DWORD [EAX]
0x03f90015 0000 ADD [EAX], AL
0x03f90017 0028 ADD [EAX], CH
0x03f90019 01f9 ADD ECX, EDI
0x03f9001b 0300 ADD EAX, [EAX]
0x03f9001d 0000 ADD [EAX], AL
0x03f9001f 0028 ADD [EAX], CH
0x03f90021 01f9 ADD ECX, EDI
0x03f90023 0300 ADD EAX, [EAX]
0x03f90025 0000 ADD [EAX], AL
0x03f90027 0000 ADD [EAX], AL
0x03f90029 00f9 ADD CL, BH
0x03f9002b 0300 ADD EAX, [EAX]
0x03f9002d 0000 ADD [EAX], AL
0x03f9002f 0000 ADD [EAX], AL
0x03f90031 00f9 ADD CL, BH
0x03f90033 0300 ADD EAX, [EAX]
0x03f90035 0000 ADD [EAX], AL
0x03f90037 008000000000 ADD [EAX+0x0], AL
0x03f9003d 0000 ADD [EAX], AL
0x03f9003f 00 DB 0x0
Process: svchost.exe Pid: 1820 Address: 0x24f0000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 128, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x024f0000 20 00 00 00 e0 ff 07 00 0c 00 00 00 01 00 05 00 ................
0x024f0010 00 42 00 50 00 30 00 70 00 60 00 00 00 00 00 00 .B.P.0.p.`......
0x024f0020 48 8b 45 28 c7 00 00 00 00 00 c7 40 04 00 00 00 H.E(.......@....
0x024f0030 00 48 8b 45 28 48 8d 40 08 48 89 c2 48 8b 45 20 .H.E(H.@.H..H.E.
0x024f0000 2000 AND [EAX], AL
0x024f0002 0000 ADD [EAX], AL
0x024f0004 e0ff LOOPNZ 0x24f0005
0x024f0006 07 POP ES
0x024f0007 000c00 ADD [EAX+EAX], CL
0x024f000a 0000 ADD [EAX], AL
0x024f000c 0100 ADD [EAX], EAX
0x024f000e 0500004200 ADD EAX, 0x420000
0x024f0013 50 PUSH EAX
0x024f0014 0030 ADD [EAX], DH
0x024f0016 007000 ADD [EAX+0x0], DH
0x024f0019 60 PUSHA
0x024f001a 0000 ADD [EAX], AL
0x024f001c 0000 ADD [EAX], AL
0x024f001e 0000 ADD [EAX], AL
0x024f0020 48 DEC EAX
0x024f0021 8b4528 MOV EAX, [EBP+0x28]
0x024f0024 c70000000000 MOV DWORD [EAX], 0x0
0x024f002a c7400400000000 MOV DWORD [EAX+0x4], 0x0
0x024f0031 48 DEC EAX
0x024f0032 8b4528 MOV EAX, [EBP+0x28]
0x024f0035 48 DEC EAX
0x024f0036 8d4008 LEA EAX, [EAX+0x8]
0x024f0039 48 DEC EAX
0x024f003a 89c2 MOV EDX, EAX
0x024f003c 48 DEC EAX
0x024f003d 8b4520 MOV EAX, [EBP+0x20]
Process: svchost.exe Pid: 1820 Address: 0x4d90000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 256, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x04d90000 20 00 00 00 e0 ff 0f 00 0c 00 00 00 01 00 05 00 ................
0x04d90010 00 42 00 50 00 30 00 70 00 60 00 00 00 00 00 00 .B.P.0.p.`......
0x04d90020 ba fc ff ff ff 03 55 20 03 55 5c b9 04 00 1a 00 ......U..U\.....
0x04d90030 4c 8b c5 ff 95 e0 37 00 00 8b 4d 24 89 08 48 8d L.....7...M$..H.
0x04d90000 2000 AND [EAX], AL
0x04d90002 0000 ADD [EAX], AL
0x04d90004 e0ff LOOPNZ 0x4d90005
0x04d90006 0f000c00 STR WORD [EAX+EAX]
0x04d9000a 0000 ADD [EAX], AL
0x04d9000c 0100 ADD [EAX], EAX
0x04d9000e 0500004200 ADD EAX, 0x420000
0x04d90013 50 PUSH EAX
0x04d90014 0030 ADD [EAX], DH
0x04d90016 007000 ADD [EAX+0x0], DH
0x04d90019 60 PUSHA
0x04d9001a 0000 ADD [EAX], AL
0x04d9001c 0000 ADD [EAX], AL
0x04d9001e 0000 ADD [EAX], AL
0x04d90020 bafcffffff MOV EDX, 0xfffffffc
0x04d90025 035520 ADD EDX, [EBP+0x20]
0x04d90028 03555c ADD EDX, [EBP+0x5c]
0x04d9002b b904001a00 MOV ECX, 0x1a0004
0x04d90030 4c DEC ESP
0x04d90031 8bc5 MOV EAX, EBP
0x04d90033 ff95e0370000 CALL DWORD [EBP+0x37e0]
0x04d90039 8b4d24 MOV ECX, [EBP+0x24]
0x04d9003c 8908 MOV [EAX], ECX
0x04d9003e 48 DEC EAX
0x04d9003f 8d DB 0x8d
Process: wmpnetwk.exe Pid: 2464 Address: 0x280000
Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE
Flags: CommitCharge: 16, MemCommit: 1, PrivateMemory: 1, Protection: 6
0x00280000 41 ba 80 00 00 00 48 b8 38 a1 e6 ff fe 07 00 00 A.....H.8.......
0x00280010 48 ff 20 90 41 ba 81 00 00 00 48 b8 38 a1 e6 ff H...A.....H.8...
0x00280020 fe 07 00 00 48 ff 20 90 41 ba 82 00 00 00 48 b8 ....H...A.....H.
0x00280030 38 a1 e6 ff fe 07 00 00 48 ff 20 90 41 ba 83 00 8.......H...A...
0x00280000 41 INC ECX
0x00280001 ba80000000 MOV EDX, 0x80
0x00280006 48 DEC EAX
0x00280007 b838a1e6ff MOV EAX, 0xffe6a138
0x0028000c fe07 INC BYTE [EDI]
0x0028000e 0000 ADD [EAX], AL
0x00280010 48 DEC EAX
0x00280011 ff20 JMP DWORD [EAX]
0x00280013 90 NOP
0x00280014 41 INC ECX
0x00280015 ba81000000 MOV EDX, 0x81
0x0028001a 48 DEC EAX
0x0028001b b838a1e6ff MOV EAX, 0xffe6a138
0x00280020 fe07 INC BYTE [EDI]
0x00280022 0000 ADD [EAX], AL
0x00280024 48 DEC EAX
0x00280025 ff20 JMP DWORD [EAX]
0x00280027 90 NOP
0x00280028 41 INC ECX
0x00280029 ba82000000 MOV EDX, 0x82
0x0028002e 48 DEC EAX
0x0028002f b838a1e6ff MOV EAX, 0xffe6a138
0x00280034 fe07 INC BYTE [EDI]
0x00280036 0000 ADD [EAX], AL
0x00280038 48 DEC EAX
0x00280039 ff20 JMP DWORD [EAX]
0x0028003b 90 NOP
0x0028003c 41 INC ECX
0x0028003d ba DB 0xba
0x0028003e 83 DB 0x83
0x0028003f 00 DB 0x0
I founded malicious hidden processes :
- 1820
- 1860
- 2464
So when i crosschecked the previous list with those processes i founded the answer
$ volatility -f victim.raw --profile=Win7SP1x64 netscan | egrep '1820|1860|2464'
Volatility Foundation Volatility Framework 2.6
0x5c201ca0 UDPv4 0.0.0.0:5005 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5c201ca0 UDPv6 :::5005 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5c692940 UDPv4 0.0.0.0:5005 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5c7bac70 UDPv4 0.0.0.0:5004 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5c7bac70 UDPv6 :::5004 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5ca517c0 UDPv4 0.0.0.0:5004 *:* 2464 wmpnetwk.exe 2019-05-02 18:05:14 UTC+0000
0x5cabcdd0 TCPv4 0.0.0.0:554 0.0.0.0:0 LISTENING 2464 wmpnetwk.exe
0x5cad94a0 TCPv6 -:49158 ::1:2869 CLOSED 2464 wmpnetwk.exe
0x5d5f79c0 TCPv4 0.0.0.0:554 0.0.0.0:0 LISTENING 2464 wmpnetwk.exe
0x5d5f79c0 TCPv6 :::554 :::0 LISTENING 2464 wmpnetwk.exe
So the answer was udp:xxxx (xxxx was the port number)
Question : Vads tag and execute protection are strong indicators of malicious processes; can you find which they are? (ANSWER format: Pid1;Pid2;Pid3)
I already answered to this question 😉
‘www.go.ru’ (write full url without any quotation marks)
I decided to dump the malicious processes and save them for analysis
$ volatility -f victim.raw --profile=Win7SP1x64 procdump -p 1860 --dump-dir .
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
------------------ ------------------ -------------------- ------
0xfffffa8003172b30 0x00000000ffa20000 explorer.exe OK: executable.1860.exe
$ volatility -f victim.raw --profile=Win7SP1x64 procdump -p 1820 --dump-dir .
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
------------------ ------------------ -------------------- ------
0xfffffa8003162060 0x00000000ff300000 svchost.exe OK: executable.1820.exe
$ volatility -f victim.raw --profile=Win7SP1x64 procdump -p 2464 --dump-dir .
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
------------------ ------------------ -------------------- ------
0xfffffa8003371540 0x00000000ff190000 wmpnetwk.exe OK: executable.2464.exe
I decided to upload the files to virustotal to see if it can detect something
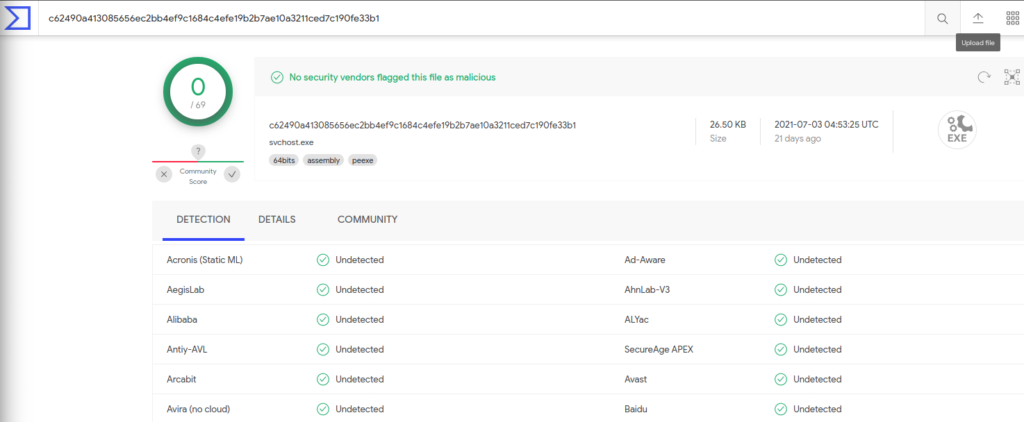

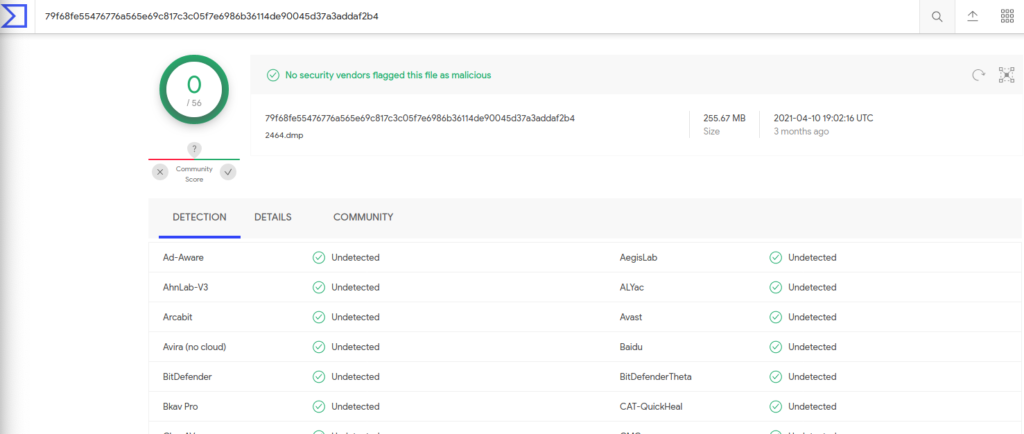
No process was detected as malicious
I did the same for memory dump
$ volatility -f victim.raw --profile=Win7SP1x64 memdump -p 1860 --dump-dir .
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing explorer.exe [ 1860] to 1860.dmp
$ volatility -f victim.raw --profile=Win7SP1x64 memdump -p 1820 --dump-dir .
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing svchost.exe [ 1820] to 1820.dmp
$ volatility -f victim.raw --profile=Win7SP1x64 memdump -p 2464 --dump-dir .
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing wmpnetwk.exe [ 2464] to 2464.dmp
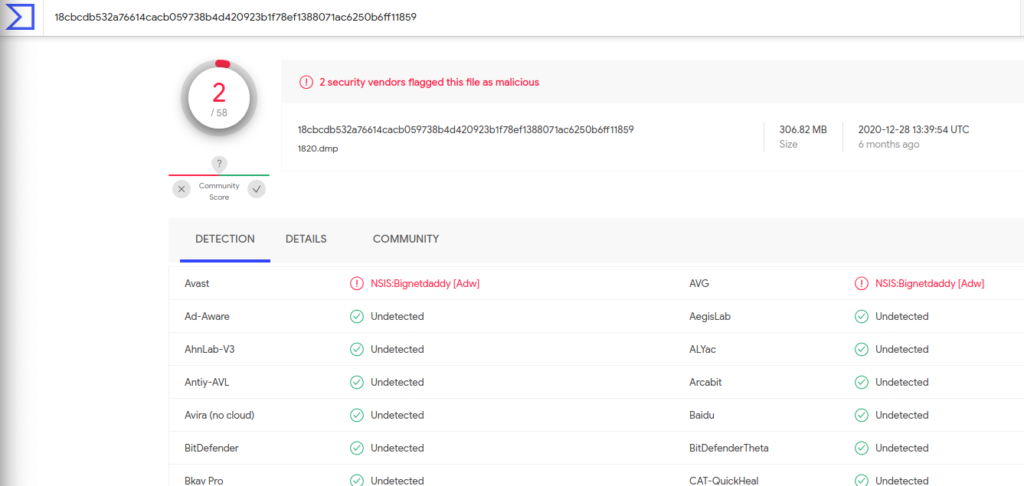
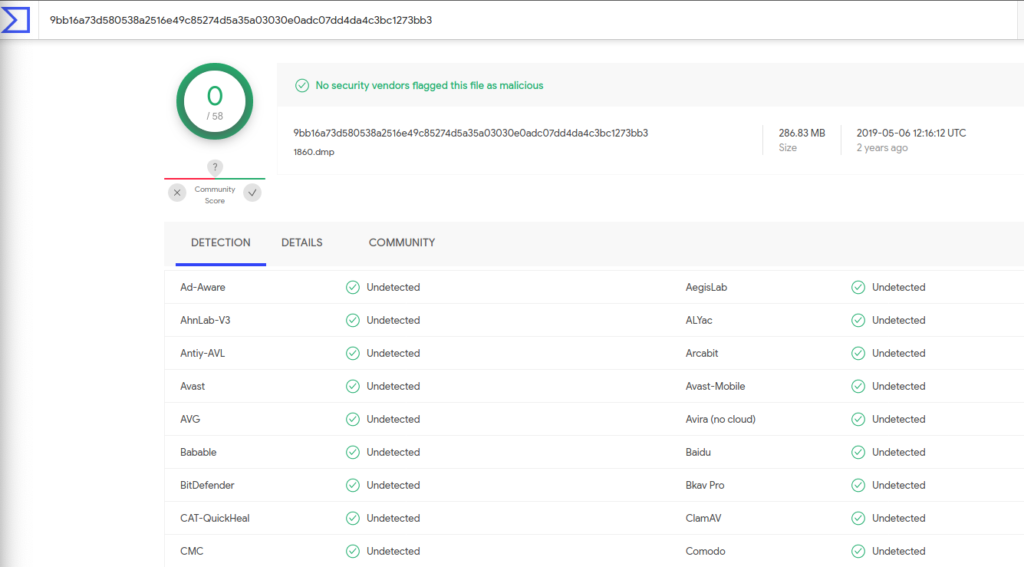
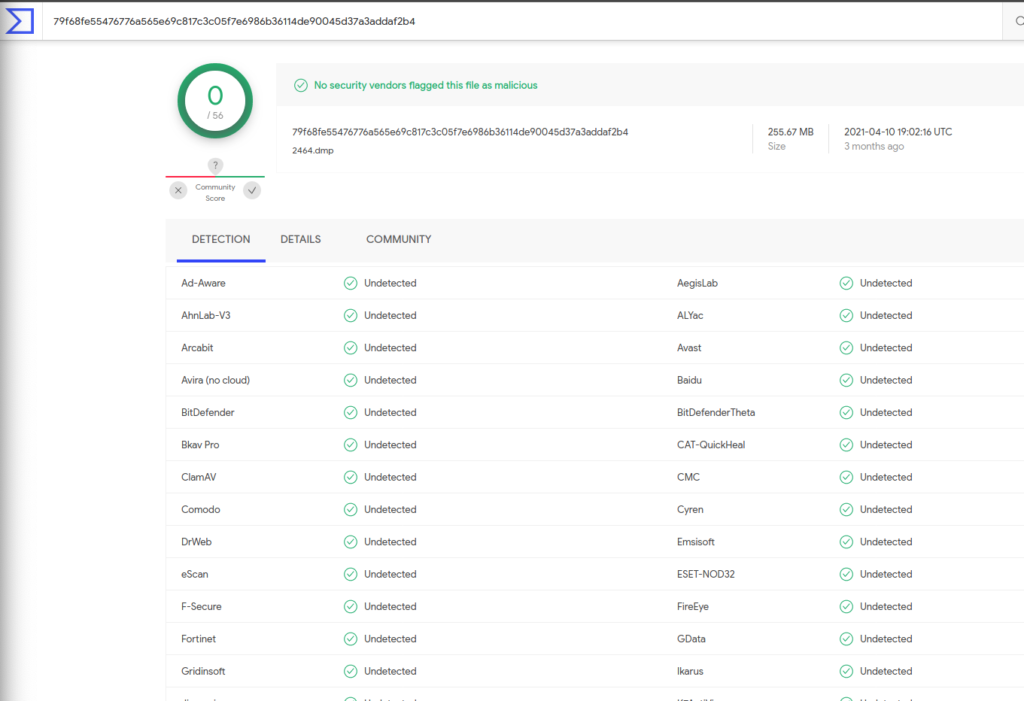
Only 1820.dmp was detected by avast as a malicious
Time to get strings and much theme with the www.go****.ru as indicated in the question
$ strings 1820.dmp 1860.dmp 2464.dmp| egrep -i 'www.go([[:alpha:]])*.ru'
www.google.ru
www.gocaps.ru
www.goporn.ru
www.godyaev.ru
www.goldfon.ru
www.gogo.ru
www.godvesny.ru
www.gogoasia.ru
www.goldorden.ru
www.goexchange.ru
www.goldchrome.ru
According to the hint : This site is little naughty, I spoted it easily 🙂
Question : ‘www.i.com’ (write full url without any quotation marks)
Hint : Do you like football
$ strings 1820.dmp 1860.dmp 2464.dmp| egrep -i 'www.i([[:alpha:]])*.com$'
www.itau.com
www.imdb.com
www.ikaka.com
www.icsalabs.com
www.icubed.com
www.icq.com
www.infospyware.com
www.ibookprice.com
www.irangoals.com
www.ixomodels.com
www.infosecpodcast.com
www.idealpackhk.com
www.identityhit.com
www.incodesolutions.com
www.indielisboa.com
www.intsecureprof.com
www.internationalservicecheck.com
if you want to be more specific counting the number of missing characters
$ strings 1820.dmp 1860.dmp 2464.dmp| egrep -i 'www.i([[:alpha:]]){4}.com$'
www.ikaka.com
Question : ‘www.ic**.com’
Hint : Very strong IOC
IOC stands for Indicators Of Compromise
$ strings 1820.dmp 1860.dmp 2464.dmp | egrep -i 'www.ic([[:alpha:]]){6}.com$'
www.icsalabs.com
Question : 202..233. (Write full IP)
$ strings 1820.dmp 1860.dmp 2464.dmp | egrep -i '202.([[:digit:]]){3}.233'
202.107.233.211
Question : ***.200.**.164 (Write full IP)
$ strings 1820.dmp 1860.dmp 2464.dmp | egrep -i '([[:digit:]]){3}.200.([[:digit:]]){2}.164'
phttp://209.200.12.164/drm/provider_license_v7.php
Question : 209.190.***.***
$ strings 1820.dmp 1860.dmp 2464.dmp | egrep -i '209.190.([[:digit:]]){3}.([[:digit:]]){3}'
`http://209.190.122.186/drm/license-savenow.asp
Question : What is the unique environmental variable of PID 2464?
$ volatility -f victim.raw --profile=Win7SP1x64 envars -p 2464
Volatility Foundation Volatility Framework 2.6
Pid Process Block Variable Value
-------- -------------------- ------------------ ------------------------------ -----
2464 wmpnetwk.exe 0x00000000002c47a0 ALLUSERSPROFILE C:\ProgramData
2464 wmpnetwk.exe 0x00000000002c47a0 APPDATA C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming
2464 wmpnetwk.exe 0x00000000002c47a0 CommonProgramFiles C:\Program Files\Common Files
2464 wmpnetwk.exe 0x00000000002c47a0 CommonProgramFiles(x86) C:\Program Files (x86)\Common Files
2464 wmpnetwk.exe 0x00000000002c47a0 CommonProgramW6432 C:\Program Files\Common Files
2464 wmpnetwk.exe 0x00000000002c47a0 COMPUTERNAME VICTIM-PC
2464 wmpnetwk.exe 0x00000000002c47a0 ComSpec C:\Windows\system32\cmd.exe
2464 wmpnetwk.exe 0x00000000002c47a0 FP_NO_HOST_CHECK NO
2464 wmpnetwk.exe 0x00000000002c47a0 LOCALAPPDATA C:\Windows\ServiceProfiles\NetworkService\AppData\Local
2464 wmpnetwk.exe 0x00000000002c47a0 NUMBER_OF_PROCESSORS 1
2464 wmpnetwk.exe 0x00000000002c47a0 OxxxxxxxxE 1 <====== HRE
2464 wmpnetwk.exe 0x00000000002c47a0 OS Windows_NT
----------- [ REDACTED ] ------------------
The only variable available (not standard one) is : OxxxxxxxE (characters hidden by the xxxxx)
Enjoy 😉